WGU D487 OA Study Guide I - 2025 | Mastering Threat Modeling📖
After you develop a new software system you must deal with serious cybersecurity threats that emerge to create an assault opportunity. Any unprotected building eventually gives access to intruders because locks serve as essential security measures. The rescue strategy appears through threat modeling practices.
The implementation of threat modeling permits organizations to foresee security threats and recognize them early so they can control their development into extensive cyberattacks. The article details:
- Threat Modeling Frameworks – STRIDE/DREAD/PASTA: STRIDE identifies threats in six areas: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. DREAD assesses risks based on Damage, Reproducibility, Exploitability, Affected Users, and Discoverability. PASTA focuses on risk analysis using attack simulations.
- SANS Institute Cyber Defense Seven-Step Recipe for Threat Modeling: This method involves identifying assets, defining security needs, modeling the system, spotting threats, prioritizing risks, assessing controls, and creating mitigation strategies.
There is no need for concern if software development is new to you because threat modeling remains straightforward despite its serious nature. Learning to play chess like a pro means you can avoid checkmate by hackers when you understand their moves ahead of time. Let’s dive in!
How to Use This Guide for the WGU D487 OA Exam?📖
The D487 Secure Software Design OA exam at WGU evaluates your understanding of threat modeling frameworks, cyber defense strategies, and security risk management. This guide simplifies the key concepts of threat modeling frameworks (STRIDE, DREAD, PASTA) and the SANS Institute Cyber Defense seven-step recipe for threat modeling to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D487 OA exam.

Understanding Threat Modeling Frameworks For D487 OA: STRIDE, DREAD, and PASTA📝
Software development requires security to function as the primary focus during the creation stage. Organizations must perform threat modeling as an essential procedure to find upcoming security risks before turning them into vulnerabilities. Different methods provide security professionals along with developers tools to detect threats combined with efficient defensive measures. Among common threat modeling structures are STRIDE DREAD and PASTA. These security frameworks use separate methods for understanding and protecting software system vulnerabilities.
Reading instructions that break down these frameworks for understanding will be provided in this section to serve non-experts.

What is STRIDE?
Microsoft developed STRIDE as a threat modeling framework to assist developers and security teams when identifying and sorting security threats. The method analyzes all potential entry points that attackers could exploit. The acronym STRIDE stands for:
- Spoofing: Pretending to be someone else to gain unauthorized access.
- Tampering: Modifying data or code without permission.
- Repudiation: Denying an action took place, making it difficult to track accountability.
- Information Disclosure: Exposing sensitive information to unauthorized individuals.
- Denial of Service (DoS): Preventing legitimate users from accessing a service.
- Elevation of Privilege: Gaining higher access rights than authorized.
How is STRIDE Used?
STRIDE is typically applied during the design phase of software development. By mapping each component of a system to these threat categories, developers can proactively identify vulnerabilities. This structured approach ensures that security concerns are addressed early, reducing the risk of costly security flaws later in the development cycle.
Example: Imagine an online banking system. Using STRIDE, developers can assess potential threats:
- Attackers might spoof user credentials.
- They could tamper with transaction records.
- A malicious insider may repudiate fraudulent actions.
- Poor encryption might lead to information disclosure.
- A bot attack could cause a denial of service.
- Hackers might exploit software bugs to elevate privileges and gain unauthorized access.
STRIDE provides a systematic way to identify and mitigate these risks before the software is deployed.
What is DREAD?
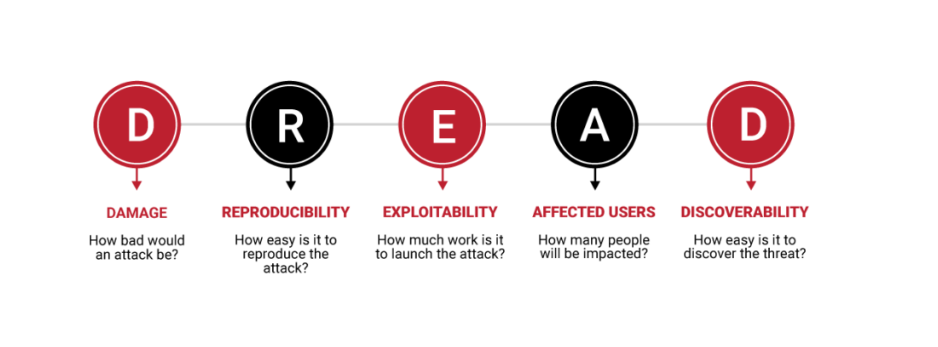
While STRIDE helps identify threats, DREAD is used to prioritize them based on risk levels. DREAD evaluates each threat based on five key factors:
- Damage Potential: How much harm could this threat cause?
- Reproducibility: How easily can this threat be repeated?
- Exploitability: How simple is it to exploit this vulnerability?
- Affected Users: How many people could be impacted?
- Discoverability: How easy is it to find this vulnerability?
Each factor is rated on a scale of 0 to 10, and the total score determines the severity of the threat:
- Critical: 40-50
- High: 25-39
- Medium: 11-24
- Low: 1-10
How is DREAD Used?
DREAD is often used in combination with STRIDE. Once potential threats are identified using STRIDE, security teams rank them using DREAD to decide which ones to fix first. This helps in allocating security resources effectively, ensuring that the most damaging and exploitable threats are addressed with priority.
Example: Suppose a company discovers two vulnerabilities:
- A minor information disclosure issue scoring 15 on DREAD (Medium risk).
- A privilege escalation flaw scoring 45 (Critical risk).
In this case, the company should fix the privilege escalation issue first since it has a much higher risk impact.
What is PASTA?
The PASTA (Process for Attack Simulation and Threat Analysis) represents a comprehensive risk-based business approach to threat modeling. PASTA delivers strategic threat mitigation through its approach which connects business requirements with technical security weaknesses beyond what STRIDE and DREAD provide.
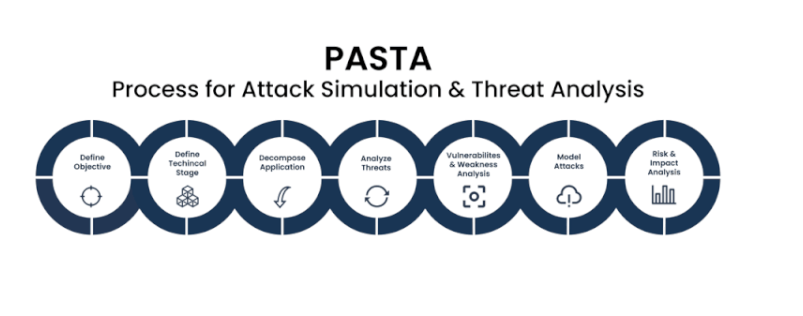
PASTA follows a seven-step process:
- Define Objectives: Identify business goals and security objectives.
- Define Technical Scope: Determine system components and technical boundaries.
- Decompose the Application: Break down the system into smaller parts for analysis.
- Analyze Threats: Identify threats specific to each component.
- Analyze Weaknesses & Vulnerabilities: Identify potential security flaws.
- Model Attacks: Simulate how a real-world attacker might exploit the system.
- Assess Risk & Impact: Evaluate how each threat affects business operations.
How is PASTA Used?
PASTA is often applied later in the development cycle or even in production environments where businesses need to align security measures with real-world threats. It allows organizations to simulate attacks and understand how vulnerabilities could impact operations.
Example: A financial institution using PASTA might discover that its online banking system is vulnerable to phishing attacks that could lead to fraud. Instead of just fixing the technical flaw, they might also implement:
- Stronger authentication methods (like two-factor authentication).
- User education programs to raise awareness about phishing scams.
PASTA’s business-focused approach ensures that security solutions are aligned with real-world risks rather than just technical concerns.
Comparing STRIDE, DREAD, and PASTA
Feature | STRIDE | DREAD | PASTA |
Focus | Categorizing threats | Risk assessment | Business risk alignment |
Approach | Lists six threat types | Assigns numerical risk | Simulates attack scenarios |
Best Use | Early design phase | Prioritizing threats | Mature security programs |
Complexity | Simple, easy to use | Moderate complexity | Advanced, time-consuming |
Strength | Systematic framework | Helps prioritize risks | Aligns security with business objectives |
Weakness | May list irrelevant threats | Time-consuming analysis | Requires expert knowledge |
Each framework serves a different purpose, and the choice depends on the organization’s security goals, resources, and development stage.
Importance For the D487 OA
The development of secure software programs needs threat modeling as an integral essential step. Organizations achieve better security risk management through implementing frameworks which include STRIDE, DREAD, and PASTA. STRIDE provides threat classification but DREAD establishes threat severity levels and PASTA establishes security connections to business aims.
The examinees of WGU D487 must grasp these frameworks both to succeed in their tests and to strengthen security implementations in genuine software development. The integration of these security methodologies enables organizations to develop software systems that maintain high resilience and strength along with maximum security features.
Understanding the SANS Institute Cyber Defense Seven-Step Recipe For D487 OA📝
Users must conduct threat modeling of their software systems on a continuous basis because security dangers keep adapting to demand proactive risk management strategies from organizations. Through the SANS Institute Cyber Defense Seven-Step Recipe for Threat Modeling organizations obtain a step-by-step method for identifying and reducing potential security vulnerabilities prior to exploitation attempts.
This method helps security assessments begin during development for better protection against major security incidents. A detailed explanation of the SANS Institute Cyber Defense Seven-Step Recipe will follow using simplified steps for easy learning and implementation.

Step 1: Create a Threat Modeling Team
The first step in the process is to assemble a diverse team of individuals responsible for identifying and analyzing security threats. A well-rounded team typically includes:
- Software Architects – Understand the overall design of the system and how its components interact.
- Developers – Know the implementation details and potential weak points in the code.
- Security Specialists – Provide expertise in cybersecurity threats and best practices.
- Business Stakeholders – Ensure security aligns with business goals and compliance requirements.
A diverse team helps to identify security risks from multiple perspectives, leading to a more comprehensive threat model. By including stakeholders from various disciplines, teams can anticipate different attack scenarios and ensure security is integrated throughout the system’s lifecycle.
Step 2: Define the Threat Modeling Scope
In this step, the team determines what aspects of the system will be analyzed. The scope includes:
- Identifying assets such as databases, APIs, and authentication systems.
- Mapping system components to understand how data flows within the system and where security risks may exist.
- Determining security boundaries to define where potential threats may emerge and where defenses should be prioritized.
A well-defined scope helps ensure that the threat modeling process remains focused, efficient, and effective in uncovering security gaps without being too broad or too narrow.
Step 3: View the System as an Adversary
To understand how an attacker might exploit the system, the team must adopt a hacker’s mindset. This step involves:
- Identifying entry and exit points where attackers could gain access, such as user authentication systems, APIs, or network connections.
- Assessing potential attack vectors, including phishing, SQL injection, and malware exploits.
- Evaluating how an attacker could manipulate or control the system, such as escalating privileges or accessing sensitive data.
By thinking like an adversary, security teams can proactively identify vulnerabilities and implement stronger defenses before an actual attack occurs.
Step 4: Identify Threats
Once potential attack vectors are identified, the next step is to classify and document security threats. The SANS Institute recommends using established models like:
- STRIDE – Categorizes threats into Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
- Threat Trees – Visually map out different ways a system could be compromised, showing the relationships between different attack paths.
Threat identification helps security teams understand where vulnerabilities exist, how they might be exploited, and what countermeasures are needed to reduce risks effectively.
Step 5: Rank the Threats
Not all threats are equally dangerous. Some may have a severe impact, while others might be minor concerns. To prioritize them, the SANS methodology suggests using the DREAD model, which ranks threats based on:
- Damage Potential – How much harm can the threat cause? Could it lead to data breaches, financial loss, or system downtime?
- Reproducibility – How easily can the threat be repeated by an attacker? If it’s simple to replicate, it poses a higher risk.
- Exploitability – How easy is it to exploit the vulnerability? The lower the effort required, the more dangerous the threat.
- Affected Users – How many users are impacted? A widespread issue affecting many users requires urgent attention.
- Discoverability – How easy is it to find the vulnerability? If an attacker can easily locate it, the risk is significantly higher.
By assigning a numerical value to each category, threats can be ranked from high priority to low priority, ensuring that the most dangerous and easily exploitable threats are addressed first.
Step 6: Implement Mitigation Measures
After ranking the threats, the next step is to determine how to respond to them. There are three possible approaches:
- Eradicate – Completely eliminate the threat by fixing the vulnerability, such as patching software or redesigning insecure components.
- Minimize – Reduce the impact of the threat with security controls, such as implementing firewalls, encryption, or multi-factor authentication.
- Accept – Acknowledge the risk but take no action (usually for low-priority threats where the cost of mitigation is higher than the risk itself).
Security teams should analyze each threat carefully and choose the most effective mitigation strategy to strengthen the system’s defenses.
Step 7: Document the Results
The final step is to record all findings from the threat modeling process. Documentation should include:
- A list of identified threats and vulnerabilities, along with their rankings and mitigation status.
- Threat trees and risk rankings for each threat to show how they were analyzed.
- Mitigation strategies and security measures implemented, ensuring accountability.
- Lessons learned and recommendations for future projects, helping teams improve security for future developments.
Proper documentation helps teams track security decisions, improve collaboration, and create a reference guide for future security assessments.
Why is the SANS Seven-Step Recipe Important?
Through its organized framework, the SANS Cyber Defense Threat Modeling enables consistent identification and protection of security threats. Security assessment methodology contains features of different techniques including STRIDE, threat trees, and DREAD because it constructs an integrated practical security assessment sequence.
By following this seven-step approach, organizations can:
- Improve security awareness among development teams and stakeholders.
- Reduce security vulnerabilities early in the development cycle, lowering the risk of exploitation.
- Prioritize the most critical threats effectively, focusing on those with the highest impact and likelihood.
- Ensure better compliance with security standards, reducing regulatory risks.
Importance For the D487 OA
The secure software design process depends heavily on threat modeling which can be implemented through the SANS Institute’s seven-step methodology to properly detect and handle security risks. The combination of suitable personnel together with a clear scope definition along with an attacker-focused perspective and threat discovery followed by risk prioritization and protection measures and process documentation enables substantial improvement of software security postures.
For security professionals and students preparing for WGU D487, mastering this approach ensures a strong foundation in threat modeling and cybersecurity defense strategies. Implementing this methodology will help in building robust and secure applications, preventing security breaches before they happen.
Tired of reading blog articles?
Let’s Watch Our Free WGU D487 Practice Questions Video Below!

Wrapping Up: Your Path to Success in WGU D487 OA📖
Threat modeling is an essential skill for anyone venturing into secure software design, and mastering frameworks like STRIDE, DREAD, and the SANS Seven-Step Recipe will equip you with the knowledge needed to safeguard applications against potential cyber threats. These methodologies provide a structured approach to identifying vulnerabilities, prioritizing risks, and implementing effective security measures—exactly the kind of understanding that will be tested in your WGU D487 OA.
So, take the time to absorb these concepts, practice applying them, and reinforce your learning by reviewing real-world security scenarios. A well-prepared security professional is always ahead of the threats, and by mastering these frameworks, you’ll not only ace your final WGU D487 OA but also be well-equipped for a successful career in cybersecurity.
Best of luck—go crush that exam!






