WGU D306 OA Study Guide - 2025 | Azure Managed Identities and Kubernetes Architecture📖
Have you ever felt like managing cloud security is as tricky as juggling flaming torches? Don’t worry—Azure Managed Identities and Kubernetes Architecture are here to save the day. These powerful tools take the complexity out of securing and managing cloud applications, making life easier for developers and IT teams. In this article, we’re going to demystify these two game-changing topics with a friendly and approachable touch.
- Kubernetes Architecture: Kubernetes is a container orchestration platform with a master node managing worker nodes that run containers. Key components include the API server, etcd (database), scheduler, controller manager, and kubelet, ensuring efficient workload management.
- Azure Managed Identities: Managed Identities in Azure provide secure, automatic authentication for services without storing credentials, simplifying access to Azure resources while enhancing security.
Whether you’re preparing for an exam like WGU D306 OA questions or just trying to level up your cloud skills, understanding these concepts is essential. Stick around as we dive into the details and show you how to make your cloud journey smoother than ever!
How to Use This Guide for the WGU D306 OA Exam? 📖
The D306 Azure Developer Associate OA exam at WGU evaluates your understanding of cloud-native application development, container orchestration, and identity management. This guide simplifies the key concepts of Kubernetes architecture and Azure Managed Identities to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D306 OA exam.

Understanding Kubernetes Architecture for D306📝
Kubernetes is an open-source platform that helps developers manage containerized applications. Think of it like a team manager who makes sure all players are in the right position, doing their job efficiently, and working together seamlessly. When paired with Azure’s Kubernetes Service (AKS), Kubernetes becomes even more powerful and easy to use. Let’s dive step-by-step into its architecture and understand how it all fits together.
What is Kubernetes?
Kubernetes is like the brain of an operation for containers. Containers are lightweight, self-contained packages that include everything an application needs to run. However, managing multiple containers across many computers can get chaotic. That’s where Kubernetes steps in to organize everything. It:
- Automatically deploys and manages applications.
- Scales applications up or down based on demand.
- Ensures that everything runs smoothly, even if something fails.
For example, if you were running a bakery, Kubernetes would make sure there’s always the right number of bakers (containers) for the number of orders coming in.
Azure Kubernetes Service (AKS)
AKS is Microsoft Azure’s way of making Kubernetes easier for everyone. Imagine Kubernetes is a car engine, and AKS is a fully assembled car with automatic features like cruise control. With AKS, you get:
- A Managed Control Plane: This means Azure takes care of the tough parts like upgrades and maintenance, so you can focus on your applications.
- Integration with Azure Tools: AKS works smoothly with Azure Active Directory for secure access, Azure Monitor for performance tracking, and Azure DevOps for deploying updates.
- Scalability: AKS can automatically adjust resources depending on how much traffic your application gets.
By using AKS, you not only save time but also get a secure and reliable platform to run your applications. This makes it a favorite for those preparing for exams like WGU D306 OA questions.
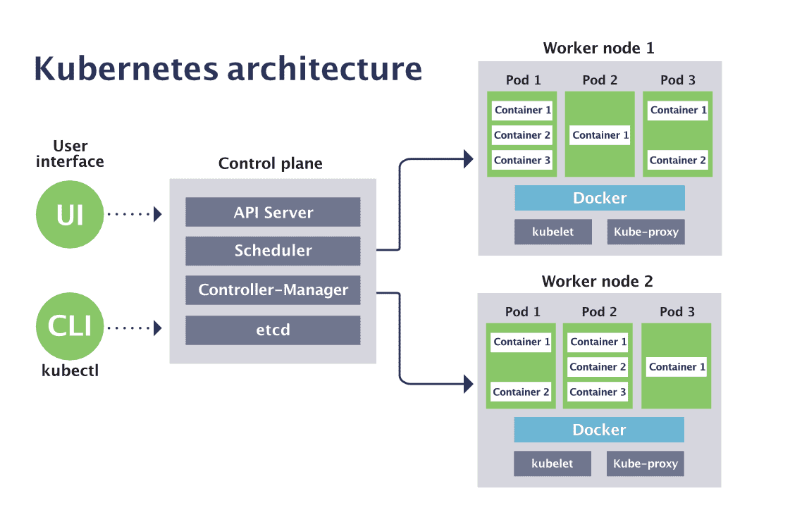
Breaking Down Kubernetes Architecture
Kubernetes is a sophisticated system made up of many components, each playing a critical role in ensuring the platform runs efficiently and reliably. Let’s explore its architecture in detail to understand how it all fits together.
- Control Plane: The control plane is the brain of Kubernetes, responsible for managing the entire cluster. Its key components include:
- API Server: This acts as the central point of communication. It processes requests from users, command-line tools, and even other internal components, ensuring smooth coordination.
- etcd: A distributed key-value store that functions as the database for Kubernetes. It stores all cluster configuration and state information, ensuring consistency and fault tolerance.
- Scheduler: This is the decision-maker that determines where new tasks (pods) should run within the cluster, optimizing resource utilization and balancing the load.
- Controller Manager: Responsible for maintaining the desired state of the cluster. For example, it ensures that if three replicas of an application are needed, they are running at all times. If one fails, it spins up another to replace it.
- API Server: This acts as the central point of communication. It processes requests from users, command-line tools, and even other internal components, ensuring smooth coordination.
- Worker Nodes: Worker nodes are the machines (either physical or virtual) where the actual workloads run. Each node has three main components:
- Kubelet: A crucial agent that communicates with the control plane, ensuring that all assigned pods are running correctly and reporting back their status.
- Kube-proxy: Handles network communication for the node, managing traffic rules and ensuring pods and services within the cluster can communicate seamlessly.
- Container Runtime: This is the engine that runs the containers on the node. Popular options include Docker and containers.
- Kubelet: A crucial agent that communicates with the control plane, ensuring that all assigned pods are running correctly and reporting back their status.
- Pods: Pods are the smallest deployable units in Kubernetes. A pod can contain one or more containers that share the same network and storage. They are often used to run tightly coupled processes, such as a web server and its helper service.
- Services: Services provide stable networking to pods, enabling consistent communication. Even if individual pods are replaced, the service ensures that users or other parts of the application can still reach them.
- Ingress: Ingress is like a gateway for managing external access to services. It allows you to define rules for HTTP and HTTPS traffic, load balancing, and SSL termination, ensuring secure and efficient user interactions.
- Add-ons: Kubernetes supports optional components known as add-ons, which enhance its functionality. These include tools for monitoring, logging, and additional networking capabilities. Add-ons are crucial for tailoring Kubernetes to meet specific operational needs. Now let’s understand how Kubernetes is structured. It has several parts, each doing a specific job.
Key Features in AKS Architecture
Feature | Description |
Networking in AKS | – Ensures communication between nodes and pods using virtual networks.- Includes Ingress Controllers for HTTP/S traffic and Load Balancers for even distribution of traffic. |
Persistent Storage in AKS | – Offers Azure Disks for single-node storage and Azure Files for shared storage.- Enables reliable stateful applications by providing secure and accessible storage solutions. |
Security and Access Control | – Implements Role-Based Access Control (RBAC) to manage user permissions.- Integrates with Azure Active Directory for secure authentication and authorization. |
Deployment Strategies | – Supports Rolling Updates to minimize downtime.- Allows Blue-Green Deployments for seamless transitions to new application versions. |
Why Learn Kubernetes For D306 OA?
Understanding Kubernetes architecture is crucial for anyone working with cloud services like Azure. It’s a key part of passing certifications such as WGU D306 and helps in managing modern applications efficiently. By using tools like AKS, you can simplify complex processes and ensure applications are always available and secure.
Kubernetes isn’t just about managing containers; it’s about transforming how we deploy and scale applications. Whether you’re a beginner or an expert, learning Kubernetes opens doors to endless opportunities in the tech world.
Understanding Azure Managed Identities For D306 OA 📝
In the world of cloud computing, security and efficiency are critical. Azure Managed Identities provide a way to connect applications with resources securely and effortlessly. Let’s break this down step-by-step to understand how Managed Identities work and why they are important.
What are Azure Managed Identities?
Azure Managed Identities offer an automatically managed identity in Microsoft Entra ID (formerly Azure Active Directory). This identity is like a trusted badge your application wears to access Azure resources. It eliminates the need for credentials like passwords or API keys, which are often a security risk if mishandled. Instead, the identity is managed directly by Azure, providing seamless and secure authentication. This means your application can connect to supported resources such as databases, storage accounts, and APIs without worrying about storing sensitive credentials. Here’s why this is significant:
- No Credential Management: Developers don’t need to manage usernames or passwords.
- Enhanced Security: Eliminates hard-coded credentials, reducing the risk of leaks.
- Cost-Effective: Managed Identities are provided at no extra cost.
Think of it as a secure pass that lets your application access specific resources without the hassle of remembering or storing credentials.
Types of Managed Identities
Azure offers two distinct types of managed identities, each designed for specific scenarios. Let’s delve into their characteristics and use cases:
- System-Assigned Managed Identity:
- Automatic Creation: This type of identity is automatically created when an Azure resource (like a Virtual Machine, App Service, or Azure Function) is provisioned. You don’t have to manually set it up.
- Lifecycle Tied to Resource: The identity is intrinsically linked to the lifecycle of the resource. If the resource is deleted, the identity is also removed. This ensures that unused identities don’t linger in your environment.
- Exclusive Use: Only the associated resource can use this identity to authenticate and access other Azure services. This exclusivity enhances security by isolating resource access.
- Ideal Use Case: Best suited for individual resources that require unique access permissions. For example, a single Virtual Machine accessing its own Azure Key Vault secrets.
- Automatic Creation: This type of identity is automatically created when an Azure resource (like a Virtual Machine, App Service, or Azure Function) is provisioned. You don’t have to manually set it up.
- User-Assigned Managed Identity:
- Standalone Creation: Unlike system-assigned identities, this type is created as a separate Azure resource. This allows greater control over its lifecycle and usage.
- Reusable Across Resources: The same identity can be assigned to multiple Azure resources, enabling them to share authentication credentials. For instance, several App Services accessing the same Azure SQL Database can use a single user-assigned identity.
- Independent Lifecycle: It exists independently of the resources it’s assigned to. Even if an associated resource is deleted, the identity remains active.
- Predefined Permissions: Permissions can be set up in advance, simplifying deployments that involve multiple resources.
- Ideal Use Case: Perfect for scenarios where multiple resources require the same identity or when compliance mandates centralized identity management, such as a fleet of microservices accessing shared storage.
- Standalone Creation: Unlike system-assigned identities, this type is created as a separate Azure resource. This allows greater control over its lifecycle and usage.
Property | System-Assigned Managed Identity | User-Assigned Managed Identity |
Creation | Automatically created with an Azure resource | Created manually as a standalone resource |
Lifecycle | Tied to the Azure resource | Independent of any specific resource |
Resource Sharing | Cannot be shared | Can be shared across multiple resources |
Permission Management | Assigned post-creation | Configured in advance |
Ideal Use Case | Unique permissions per resource | Shared identity across multiple resources |
How to Use Managed Identities
Using Managed Identities involves a few straightforward steps:
- Create a Managed Identity:
- For system-assigned identities, enable it during resource creation.
- For user-assigned identities, create them in Azure and assign the necessary permissions.
- Assign the Identity:
- Attach the user-assigned identity to the desired Azure resources, like Virtual Machines or App Services.
- Attach the user-assigned identity to the desired Azure resources, like Virtual Machines or App Services.
- Authorize Access:
- Use Role-Based Access Control (RBAC) to grant the managed identity permissions to access the target resources.
- Use Role-Based Access Control (RBAC) to grant the managed identity permissions to access the target resources.
- Access Resources:
- Applications can authenticate using the managed identity via Azure SDKs or connectors, simplifying secure resource access.
Practical Examples of Managed Identities
Here are some real-world scenarios where Azure Managed Identities make life easier:
- Accessing Azure Key Vault:
- A web application needs to retrieve secrets from Azure Key Vault.
- With a managed identity, the application can securely authenticate and access the secrets without storing sensitive credentials.
- Connecting to Azure SQL Database:
- Multiple applications need access to the same database.
- A user-assigned managed identity allows these applications to share authentication while maintaining security.
- Authenticating Azure Functions:
- An Azure Function requires access to an Azure Storage account.
- By enabling a system-assigned managed identity, the function can securely interact with the storage account without exposing connection strings.
- Accessing Azure Cognitive Services:
- An application using AI-based services, like text translation, can leverage a managed identity for seamless and secure API access.
Benefits of Azure Managed Identities
- No Credential Leaks: Removes the need for hard-coded secrets or credentials.
- Seamless Integration: Works smoothly with Azure’s Role-Based Access Control and Active Directory.
- Flexibility: User-assigned identities can be reused across multiple resources, reducing overhead.
- Cost-Efficient: Available at no additional cost, making it accessible for all Azure users.
Why Learn About Managed Identities For D306 OA?
Azure Managed Identities are essential for securing cloud applications and simplifying authentication processes. They’re also a crucial topic for certifications like WGU D306, helping students understand how to build secure and scalable cloud solutions. By mastering Managed Identities, you’re better equipped to manage resources effectively in a professional environment.
Tired of reading blog articles?
Let’s Watch Our Free WGU D306 Practice Questions Video Below!

Mastering Cloud Essentials: Good Luck with WGU D306 OA📄
Now that we’ve unpacked the magic of Azure Managed Identities and Kubernetes Architecture, it’s time for you to dive deeper into these essential concepts. These topics aren’t just building blocks for cloud computing; they’re also key areas that will be tested in the WGU D306 OA. By mastering these, you’ll be well-equipped to handle real-world cloud challenges and ace your final assessments.
Remember, Kubernetes helps you orchestrate your applications like a maestro conducting a symphony, while Azure Managed Identities ensure secure and effortless communication between your resources. Together, they form the backbone of efficient and secure cloud environments.
Take your time to practice, explore hands-on labs, and don’t shy away from revisiting these concepts until they click. With dedication and effort, success is just around the corner.
Good luck with your journey in mastering WGU D306! You’ve got this!