WGU D282 OA Study Guide II - 2025 | Cloud Security Made Easy 📖
When you think about cloud computing, security might seem like an intimidating topic—a fortress of technical jargon and complex setups. But don’t worry! Imagine your AWS environment as a bustling city. Some tools act as gatekeepers, others as detectives, and some as shields ready to defend against attackers. This article takes you on a friendly tour of three crucial AWS topics:
- Overview of AWS Services: AWS offers various services for deployment and monitoring. Elastic Beanstalk simplifies application hosting, Lambda enables serverless computing, CloudTrail logs track API activity, and CloudFormation automates infrastructure provisioning.
- Security Groups & NACLs: Security Groups act as virtual firewalls for EC2 instances, controlling inbound/outbound traffic, while Network ACLs (NACLs) provide broader subnet-level security rules.
- AWS Shield & GuardDuty: AWS Shield protects against DDoS attacks, while GuardDuty is an intelligent threat detection service that monitors AWS accounts for suspicious activity.
Each of these services is a piece of the AWS puzzle, essential for both protecting and optimizing your environment. Stick with us to see how they all work together and gain confidence for your WGU D282 OA questions—or any real-world cloud challenge!
How to Use This Guide for the WGU D282 OA Exam?📖
The D282 Cloud Foundations OA exam at WGU evaluates your understanding of cloud computing services, AWS infrastructure, and security measures. This guide simplifies the key concepts of AWS services (Elastic Beanstalk, Lambda, CloudTrail logs, CloudFormation), security groups & NACL, and AWS Shield & Guard Duty to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D282 OA exam.

Overview of AWS Services For D282 OA📝
As we ponder on the utility of the cloud for our applications, then there must be tools that make the job easier. AWS, short for Amazon Web Services, provided a number of features that would enable us to create and develop applications without having to focus on the various technicalities. Let’s dive into four important AWS tools: Including Elastic Beanstalk, AWS Lambda, CloudTrail Logs, as well as CloudFormation. These tools are known for their magical support for the developers or in other words, it is a boon for them.

Elastic Beanstalk: Your Friendly App Manager
Suppose, you would like to develop a website and do not want to spend days configuring your web and database servers. Where oh where did my resources go? Elastic Beanstalk is here to fix things! Elastic Beanstalk is a cloud-based service that is actually a Platform as a Service (PaaS) that facilitates deploying applications into the cloud. It works with Java, .NET, PHP, Node.js, Python, Ruby, Go, Docker, and it is suitable for developers who work with various types of tasks. It is almost like hiring a secretary who will do all the tiresome work so that you can concentrate on your application.
What does Elastic Beanstalk do?
- Handles the Setup: It sets up servers, databases, and other tools you need.
- Monitors Health: It keeps an eye on your app to make sure everything runs smoothly.
- Adjusts Automatically: If more people visit your app, Elastic Beanstalk adds more resources to handle the traffic.
What can you use it for?
- Launching websites or apps quickly.
- Managing app environments without deep technical knowledge.
Let’s say you’re running a small online store. With Elastic Beanstalk, you can focus on designing the store while it takes care of the servers and keeps everything running smoothly.

AWS Lambda: The Invisible Worker
Now contrast that with thinking that you have to do a task each time something occurs or happens. For instance, if a user submits a photo, you may prefer to change its size instantly. AWS Lambda seems to be the right tool for this! Lambda is a FaaS (Function as a Service), invoked by events like HTTP calls through API Gateway, object uploads in S3, or database modifications. With these event triggers, it is useful and ideal for other tasks., However, you don’t have to deal with any servers and systems: they simply exist and are ready to go whenever needed for a specific event.
What makes Lambda special?
- Event-driven: It starts working when something triggers it, like a file upload.
- Automatic Scaling: Whether it’s one request or a thousand, Lambda handles it.
- Supports Many Languages: You can write code in Python, JavaScript, and more.
What can you use it for?
- Automating tasks, like processing images or videos.
- Running quick, small programs without needing a server.
For instance, a social media app could use Lambda to automatically create thumbnails of uploaded photos. It saves time and resources because Lambda only runs when needed.

AWS CloudTrail Logs: The Detective
In a big company, it’s important to know who did what and when. AWS CloudTrail Logs is like a detective that keeps track of everything happening in your AWS account. It can integrate with other AWS services, such as CloudWatch, to create alerts based on specific events. For instance, you can set up a notification if an unauthorized user tries to access sensitive data, ensuring you’re always aware of critical activities. It records every action, so you can review it later if something goes wrong.
Why are CloudTrail Logs important?
- Records Everything: It logs all actions, like who accessed your files or changed settings.
- Helps with Security: If there’s suspicious activity, you can find out what happened.
- Ensures Compliance: Many businesses need to follow rules, and CloudTrail Logs helps prove they’re following them.
What can you use it for?
- Real-time tracking of users, which would tell management that users are not doing something they should be.
- When troubleshooting problems, often the key involves having a look at what occurred prior to something failing.
CloudTrail Log can be best described as the surveillance video of your AWS account. It doesn’t prevent others from acting, but it ensures that no one can act beyond your information level.
AWS Cloud Formation: The Blueprint Maker
Finally, we have AWS CloudFormation. Imagine you’re building a house. Before you start, you need a blueprint that shows where everything goes. CloudFormation lets you create this blueprint using specific file formats like JSON and YAML, which describe all the resources and how they should connect. CloudFormation is like a blueprint for your cloud setup. It lets you write down what resources you need and how they should connect, and then it builds everything for you.
How does CloudFormation help?
- Infrastructure as Code: Instead of clicking buttons, you write a template to describe your setup.
- Consistent Setup: You can use the same template to create identical setups in different places.
- Simplifies Updates: If you need to make changes, just update the template, and CloudFormation handles the rest.
What can you use it for?
- Creating complicated setups without missing any details.
- Managing changes to your resources over time.
For example, a company might use CloudFormation to set up servers, databases, and storage for a new app. If they need the same setup for another app, they just reuse the template.
Why These Tools Matter For D282 OA
Each of these AWS tools plays a unique role in making cloud computing easier and more efficient. Elastic Beanstalk helps you manage your apps without stress. Lambda works behind the scenes to handle specific tasks. CloudTrail Logs keeps track of everything for security and troubleshooting. CloudFormation gives you a simple way to set up and manage your resources. Together, they make AWS a powerful platform for businesses and developers alike.
Students therefore gain the ability to handle questions in the WGU D282 module with ease and also relate these with practical examples. With this backdrop of understanding how AWS empowers us to build and manage applications, we turn our attention to how AWS protects those applications.
Security Groups and Network Access Control Lists (NACL): Keeping AWS Secure For D282 OA📝
I hope you have noticed that when you create something valuable, whether it is a house or website, you would like to protect it. In AWS, it has Security Groups which are like gates in your network through which traffic can pass, and the Network Access Control List (NACLs) are like fences to your resources. Continuing with our study of appliances let us look at how they operate and in particular their use in maintaining the safety of your data.
What Are Security Groups?
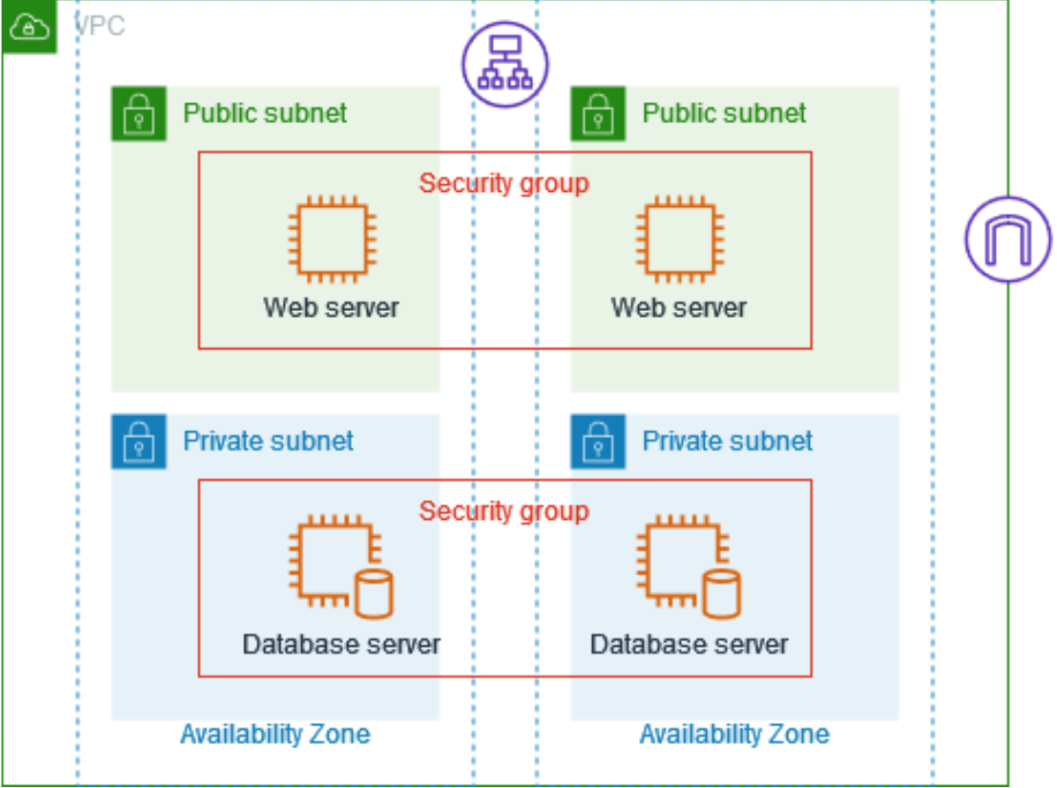
Think of a security group as a gatekeeper for your Amazon EC2 instances. It decides who can come in and who can go out. Every EC2 instance needs a security group to manage its traffic.
Key Features of Security Groups:
- Stateful Nature: If you allow traffic in, the response is automatically allowed out. This makes managing connections easier.
- Inbound Rules: You set rules to decide which incoming traffic, like web requests, is allowed.
- Outbound Rules: These rules determine which outgoing traffic, like responses to web requests, is permitted.
- Default Settings: Every Virtual Private Cloud (VPC) comes with a default security group that allows all outbound traffic but denies inbound traffic.
Use Cases:
- Allowing specific types of traffic, like HTTP for websites or SSH for remote access.
- Controlling access to an instance by allowing only trusted IP addresses.
Imagine a bank vault with a guard. The guard only lets in people who have the right key. That’s how a security group works for your cloud applications.
What Are Network Access Control Lists (NACLs)?
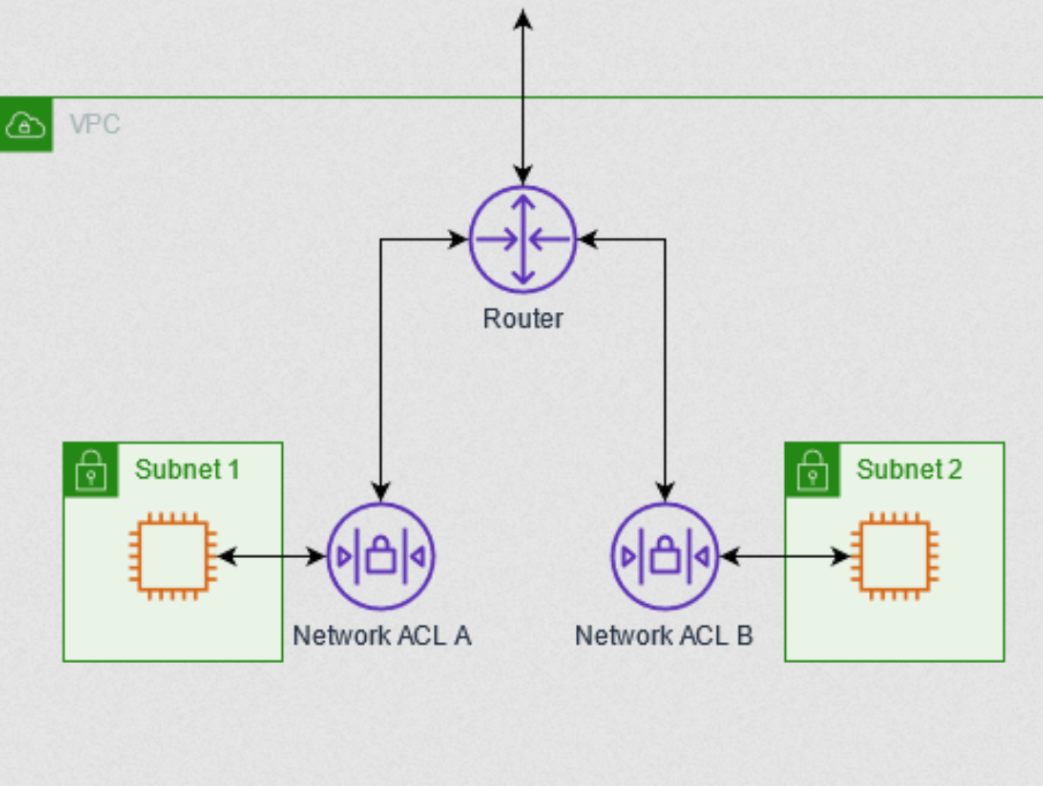
While security groups protect individual instances, NACLs guard entire subnets. Think of a NACL as a fence around a group of houses.
Key Features of NACLs:
- Stateless Nature: Unlike security groups, NACLs are stateless. If you allow incoming traffic, you must explicitly allow the response as well.
- Inbound and Outbound Rules: You can create rules to allow or deny specific traffic for your subnet.
- Rule Evaluation: Rules are evaluated in numerical order. The first matching rule determines whether traffic is allowed or denied.
- Default NACL: The default NACL for a VPC allows all traffic unless you modify it.
Use Cases:
- Blocking traffic from a specific IP address or range.
- Applying security rules across multiple instances in a subnet.
For example, if a neighborhood wants to block delivery trucks but allow residents, they would set up a rule at the fence to stop trucks while letting cars through. That’s how NACLs manage traffic.
Security Groups vs. NACLs: What’s the Difference?
Both tools are important, but they have distinct roles.
Key Differences:
- Scope: Security groups protect instances, while NACLs protect subnets.
- Statefulness: Security groups are stateful; NACLs are stateless.
- Rules: Security groups only allow traffic; NACLs can allow or deny traffic.
- Evaluation: Security group rules are evaluated collectively, while NACL rules are evaluated in order.
When to Use Them:
- Use security groups for instance-level control, like allowing SSH access.
- Use NACLs for subnet-level control, like blocking malicious IP ranges.
How to Create Security Groups and NACLs
Creating a Security Group
- Log in to the AWS Management Console: Navigate to the EC2 Dashboard.
- Select Security Groups: Under the “Network & Security” section, click “Security Groups.”
- Create a New Security Group: Click “Create Security Group” and provide a name and description.
- Set Rules:
- Add inbound rules specifying allowed traffic (e.g., allow HTTP from port 80).
- Add outbound rules specifying permitted outgoing traffic.
- Assign the Security Group: Attach it to an EC2 instance by selecting the instance and modifying its security settings.
Walkthrough: YouTube Tutorial
Creating a NACL
- Log in to the AWS Management Console: Navigate to the VPC Dashboard.
- Select Network ACLs: Under the “Security” section, click “Network ACLs.”
- Create a New NACL: Click “Create Network ACL” and assign it to a specific VPC.
- Add Rules:
- Add inbound and outbound rules to allow or deny traffic.
- Specify the rule number for order evaluation (lower numbers have higher priority).
- Associate with a Subnet: Attach the NACL to one or more subnets in your VPC.
- Apply the Least Privilege Principle: Only allow the traffic you absolutely need.
- Regular Audits: Review your rules to ensure they still meet your security needs.
- Combine Both Tools: Use security groups for instance-level rules and NACLs for broader subnet-level security.
Walkthrough: YouTube Tutorial
Why This Matters For D282 OA
Security is crucial in cloud computing. By understanding and using security groups and NACLs, you can protect your AWS resources effectively. These tools help you answer questions like those in the WGU D282 OA and ensure your applications are both functional and secure.
Tired of reading blog articles?
Let’s Watch Our Free WGU D282 Practice Questions Video Below!

AWS Shield and AWS GuardDuty: Enhancing Cloud Security For D282 OA📝
Protecting from those malicious attacks and having the capability of monitoring the applications are two of the most important needs of cloud computing security. AWS Shield, and AWS GuardDuty, are both unique tools that give strong protection to the AWS environment. Let’s find out what they are and why they are so significant.

What Is AWS Shield?
AWS Shield is like an invisible shield that protects your applications from Distributed Denial of Service (DDoS) attacks. DDoS attacks flood your application with fake traffic, making it hard for real users to access it.
Types of AWS Shield:
- AWS Shield Standard: This free service automatically protects against common DDoS attacks, ensuring your applications stay available.
- AWS Shield Advanced: This paid service offers additional features like cost protection from DDoS-related charges and access to the AWS DDoS Response Team (DRT).
Key Features:
- Automatic Detection and Mitigation: Quickly detects and stops DDoS attacks to keep your applications running.
- Customizable Protection: Works with AWS Web Application Firewall (WAF) to add extra layers of security.
- Traffic Scrubbing: Filters out malicious traffic before it reaches your applications.
Use Cases:
- Protecting websites or applications that handle sensitive information.
- Ensuring business continuity during high-profile events like sales or launches.
For example, if an online store experiences a surge in traffic during a sale, AWS Shield can block fake traffic while allowing genuine users to shop.

What Is AWS GuardDuty?
AWS GuardDuty is like a detective that monitors your AWS account for suspicious activity. It looks for unusual patterns or threats and alerts you if something doesn’t seem right.
Key Features:
- Threat Detection: Uses machine learning and threat intelligence to identify risks, like unauthorized access or malware.
- Automated Responses: This can trigger actions, like disabling compromised accounts, through AWS Lambda.
- Integration: Works with other AWS tools, like CloudTrail and VPC Flow Logs, to provide detailed insights.
Use Cases:
- Monitoring for compromised instances that may be running malware.
- Detecting unauthorized changes in your AWS resources.
Imagine someone trying to log in to your AWS account from a suspicious location. GuardDuty will notice this and send you an alert, helping you act quickly.
AWS Shield vs. AWS GuardDuty: What’s the Difference?
Feature | AWS Shield | AWS GuardDuty |
Primary Function | Prevents DDoS attacks | Detects threats within the AWS environment |
Scope | Network and application layers | User activity, API calls, and traffic |
Proactive/Reactive | Proactively stops attacks | Reactively alerts on suspicious behavior |
Key Focus | Ensures availability | Monitors for anomalies |
Action | Blocks malicious traffic | Sends alerts for detected threats |
Best Practices for Using AWS Shield and GuardDuty
- Enable Both Services: Use Shield for external protection and GuardDuty for internal monitoring.
- Integrate with Other AWS Tools: Combine these services with WAF, CloudTrail, and Lambda for a complete security solution.
- Regular Monitoring: Check alerts and reports to stay informed about potential risks.
Why These Tools Matter For D282 OA
In a cloud environment, security is a shared responsibility. AWS Shield and GuardDuty help you fulfill your part by keeping your applications available and secure. Understanding how these tools work prepares you to handle questions in the WGU D282 OA and ensures your AWS environment is protected from both external and internal threats.

Wrapping Up: Mastering Cloud Security with WGU D282 OA Confidence📄
Congratulations on completing this guide to AWS Services, Security Groups and NACLs, and AWS Shield with GuardDuty! These concepts form the backbone of AWS cloud security and management. By understanding how these tools work together, you’ll excel in the WGU D282 OA and be ready for real-world cloud challenges.
Focus on the key features and use cases we discussed—AWS Services for simplifying deployments, Security Groups and NACLs for access control, and AWS Shield and GuardDuty for robust threat protection. These services are essential for both exams and professional success.
Good luck mastering cloud security and acing the WGU D282 OA! With these tools in your arsenal, you’re ready to tackle any exam question or cloud scenario. You’ve got this!






