WGU D487 OA Study Guide II - 2025 | Mastering Secure Software Development📖
The scenario of constructing a house without any locks or doors during initial development leads to security disorders and invites dangers. Programming projects experience severe consequences when security measures are added after the completion of development work. Software development security integration must begin from the project’s initial stages because cyber threats perpetually change in present times. This part of Secure Software Design provides an explanation of essential practices for developing secure well-functioning applications that maintain structure.
To truly understand how to create secure software, you need to grasp three fundamental concepts:
- SAMM vs. BSIMM Models – Two major security assessment frameworks that guide organizations in improving their software security posture.
- The Security Development Lifecycle (SDL) – A structured approach that ensures security is integrated into every phase of software development.
- Agile vs. Waterfall Project Management – Two contrasting methodologies that influence how security is embedded in the development process.
The combined use of these three fundamental principles ensures the development of functional software that demonstrates high resistance against cyber attacks. Throughout this article, we will simplify these concepts for readers who might have no previous knowledge about them. The content provided here offers assistance to students solving WGU D487 OA questions alongside those who want to improve their secure software design proficiency. The time is now to integrate security through every phase of your development framework.
How to Use This Guide for the WGU D487 OA Exam?📖
The D487 Secure Software Design OA exam at WGU evaluates your understanding of secure software development methodologies, security frameworks, and project management strategies. This guide simplifies the key concepts of SAMM vs BSIMM models, the fundamental goals of the security development lifecycle (SDL), and agile vs waterfall project management to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D487 OA exam.

SAMM vs. BSIMM Models: Understanding the Key Differences For D487 OA📝
Developing software with security requires organizations to establish organized procedures. Two key models for software assurance maturity are SAMM (Software Assurance Maturity Model) along BSIMM (Building Security In Maturity Model). The frameworks work toward enhancing software security yet employ distinctive strategies for improvement. Your organization’s requirements dictate the selection of an appropriate model between SAMM and BSIMM.
What Are SAMM and BSIMM?
Before diving into their differences, let’s first understand what these two models are:
- BSIMM (Building Security In Maturity Model) is a descriptive framework. It observes how real-world companies implement security practices and provides a benchmark for organizations to compare their security measures.
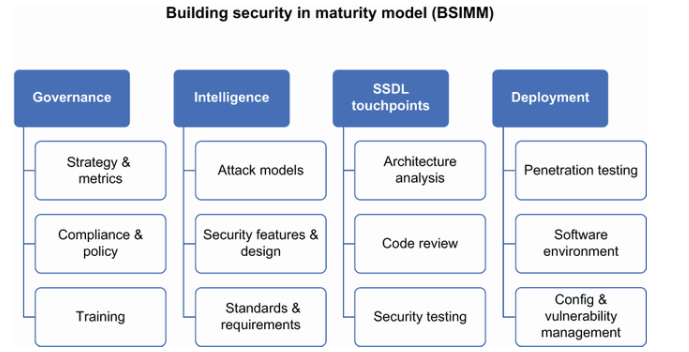
- SAMM (Software Assurance Maturity Model) is a prescriptive framework. It offers a clear roadmap for organizations to enhance their software security by implementing structured security practices.
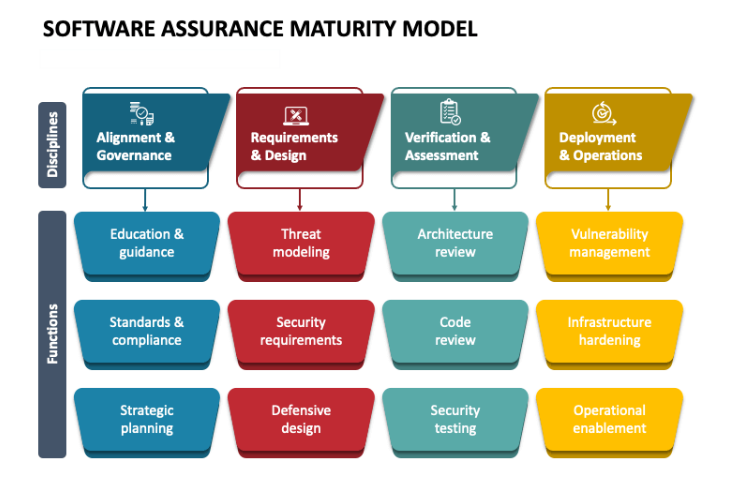
Through its defined security practices this framework provides organizations with a specific direction to boost their software security measures.
Key Differences Between SAMM and BSIMM
Feature | BSIMM | SAMM |
Approach | Descriptive – Observes and documents real-world security practices | Prescriptive – Provides specific guidance on security improvements |
Scoring System | Binary (Yes/No) for each security practice | Scale from 0 to 1, allowing partial credit |
Access | Proprietary – Requires consulting Synopsys for assessment | Open-source – Free to use and modify |
Maturity Levels | Measures activity levels but does not define maturity levels | Defines three maturity levels with clear objectives and success metrics |
Comparison | Helps organizations compare security practices with industry standards | Focuses on internal security improvements based on unique risks |
Flexibility | Less flexible but provides a well-tested industry methodology | Highly customizable to an organization’s specific needs |
Best for | Large enterprises looking for benchmarking data | Organizations (small or large) that need a tailored security framework |
Choosing Between BSIMM and SAMM
Each model is designed for different use cases. Here’s when to choose one over the other:
When to Choose BSIMM
- You want to compare your security measures against industry peers.
- Your organization already has security practices in place and wants to refine them.
- You need a well-tested, data-driven methodology.
- Your company is large and can handle the resource-intensive nature of BSIMM.
When to Choose SAMM
- You need a flexible, customizable framework to build security practices.
- Your team is smaller and requires an easier start.
- You are developing a security framework from scratch.
- You want a model that supports continuous improvement.
- You prefer an open-source model that you can modify based on your needs.
Implementation Complexity: Which One is Easier to Adopt?
BSIMM is more complex to implement because it requires organizations to measure against 120+ security practices, making it resource-intensive. It also lacks flexibility because it follows a structured methodology. Smaller organizations may find BSIMM overwhelming due to the level of detail required.
On the other hand, SAMM is simpler and allows for a more tailored approach. Because of its flexibility, organizations can gradually implement security controls and scale them as needed.
Complexity Factor | BSIMM | SAMM |
Number of Security Practices | 120+ practices, extensive measurement required | Simpler structure, easier to adopt |
Flexibility | Fixed methodology, little room for customization | Highly customizable based on specific needs |
Scalability | Ideal for large enterprises, challenging for small teams | Scales well for smaller teams and organizations |
Overall Ease of Adoption | More complex and time-consuming | Easier to start and adopt |
Scalability: Which Model Works Better for Small Organizations?
For small organizations, SAMM is generally a better choice due to its flexibility and ease of implementation:
- BSIMM is designed for large enterprises and may be difficult for small teams to adopt because of its high resource requirements.
- SAMM is open-source and scalable, making it a practical option for smaller organizations.
- BSIMM requires external assessments, which can be costly for smaller companies, whereas SAMM allows self-assessments, reducing costs.
If you’re running a small security team or a startup, SAMM provides a more practical, cost-effective, and flexible way to integrate security into your software development lifecycle.
Importance For the D487 OA
BSIMM and SAMM provide separate value to software security improvement efforts although they operate for different uses. BSIMM suits enterprises with substantial size who need industrial standards yet SAMM provides adjustable implementation steps to help organizations improve their security posture.
When selecting between SAMM and BSIMM, organizations should consider their size, budget, and security goals. If your team needs a flexible and evolving security approach, SAMM is the way to go. However, if industry benchmarking is your priority, BSIMM offers the right insights.
Regardless of the model chosen, prioritizing security in software development is crucial in today’s digital landscape. As covered in WGU D487, understanding different security models can help build robust security frameworks that protect applications and data effectively.
Fundamental Goals of the Security Development Lifecycle (SDL) For D487 OA📝
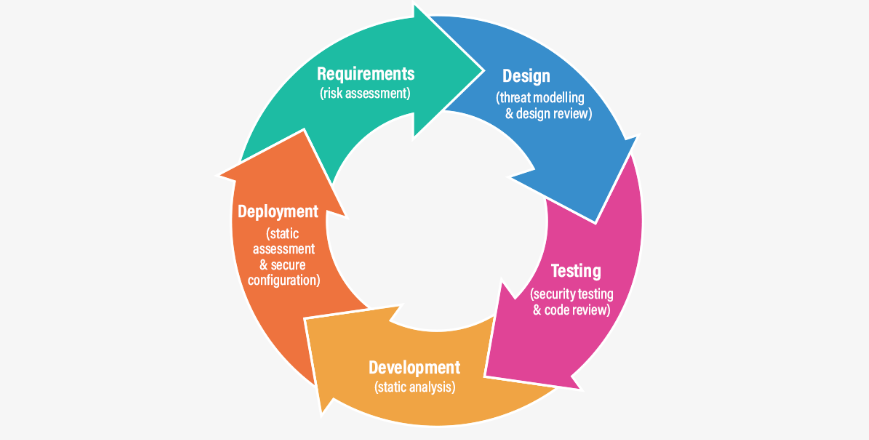
Every phase of development requires software security to be embedded as a core component. The Security Development Lifecycle (SDL) operates as a structured process to integrate security measures into software development since its initial stages because it enhances application immunity against threats.
Why Is the Security Development Lifecycle (SDL) Important?
Imagine building a house. Building security measures would be part of your construction plan from the start rather than leaving it for the end. Software development requires the implementation of the same security principles. The SDL process establishes security evaluation throughout the complete software development period before construction and throughout its lifecycle.
The fundamental goals of SDL include:
- Reducing Security Risks – Identifying and fixing vulnerabilities early in the process.
- Ensuring Compliance – Adhering to security regulations and industry standards.
- Continuous Improvement – Updating security measures to counter evolving threats.
Now, let’s break these goals down step by step.
1. Reduction of Security Risks
The earlier a vulnerability is found, the easier (and cheaper) it is to fix. SDL integrates security from the start, ensuring that risks are mitigated early.
- Secure Design – Before writing a single line of code, developers identify potential threats and design security controls accordingly.
- Threat Modeling – A structured approach to identifying possible attack scenarios and mitigating them before they become real problems.
- Secure Coding Practices – Writing code in a way that prevents vulnerabilities like SQL injection or buffer overflow attacks.
- Regular Code Reviews – Checking for security flaws as part of the development process.
By catching issues early, SDL reduces the cost and impact of security vulnerabilities.
2. Compliance with Standards and Regulations
Many industries have strict security requirements that companies must follow. SDL ensures compliance with:
- Legal frameworks (e.g., GDPR, HIPAA, PCI-DSS)
- Industry security standards (e.g., NIST, ISO 27001, OWASP guidelines)
- Internal security policies that businesses set for themselves
Ignoring compliance can lead to legal consequences, financial penalties, and reputational damage. SDL helps businesses stay on the right side of the law while ensuring customer data remains secure.
3. Continuous Improvement and Adaptation
Cyber threats evolve constantly, so security measures must keep up. SDL promotes continuous monitoring and improvement through:
- Security Testing – Using techniques like penetration testing, fuzz testing, and dynamic analysis to find vulnerabilities.
- Incident Response Planning – Preparing a plan for addressing security incidents if they occur.
- Regular Patching and Updates – Keeping software secure by fixing vulnerabilities as they arise.
- Security Training for Developers – Educating teams on emerging threats and best practices.
By integrating these measures, SDL ensures that security isn’t just a one-time step but a continuous process.
Stages of SDL and How They Support Security
SDL is structured into several key stages, each with specific security objectives:
Stage | Key Goal | Activities Involved |
Requirements | Identify security objectives | Define security needs, conduct risk assessments |
Design | Build security into the architecture | Threat modeling, security design reviews |
Implementation | Develop secure code | Code reviews, static analysis |
Verification | Validate security controls | Penetration testing, dynamic analysis |
Release | Secure deployment | Security sign-off, post-release monitoring |
Response | Address security incidents | Incident response, patch management |
Each stage strengthens security by identifying and addressing potential vulnerabilities before they reach users.
Defense in Depth: The Key to a Strong SDL
One core principle of SDL is Defense in Depth—a strategy that layers multiple security measures to minimize risk. Think of it like a castle with multiple layers of defense:
- Access Management – Restricting unauthorized access through multi-factor authentication and least privilege principles.
- Network Security – Using firewalls, intrusion detection systems, and VPNs to protect data.
- Endpoint Protection – Securing individual devices with antivirus software and encryption.
- Data Security – Encrypting sensitive data and applying strong password policies.
- Continuous Monitoring – Using security logs and alerts to detect threats in real time.
By applying multiple layers of security, SDL ensures that even if one defense fails, others remain in place.
Importance For the D487 OA
Organizations use the Security Development Lifecycle (SDL) framework as an essential method to construct secure software from the beginning of development. The fundamental security aims of risk mitigation and compliance maintenance support organizations in producing applications that will survive contemporary cyber dangers.
The integration of security measures across development phases through SDL produces software products that combine functionality with safety characteristics and reliability mechanisms as well as resilience features. The implementation of SDL guarantees throughout the Agile or Waterfall methodology that security treatments become an early development priority instead of getting pushed to the end.
Tired of reading blog articles?
Let’s Watch Our Free WGU D487 Practice Questions Video Below!
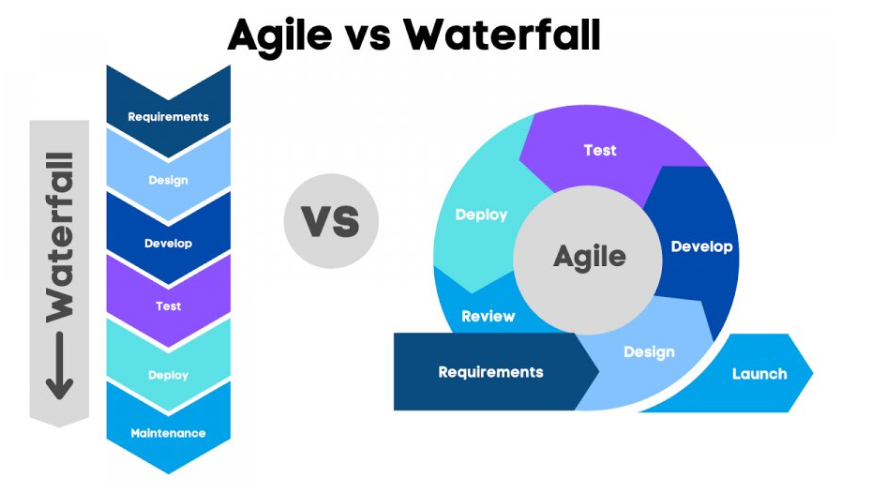
Agile vs. Waterfall Project Management: Key Differences and Best Use Cases For D487 OA📖
Project management serves as the key operational element for software development by optimizing project completion results. Two main project management approaches that organizations employ today include Agile together with Waterfall. Businesses and development teams will achieve better project results through the right approach selection when they understand both methodologies’ basic distinctions and advantages.
What Are Agile and Waterfall?
Both Agile and Waterfall are structured project management methodologies, but they differ significantly in execution:
- Waterfall: A linear and sequential approach where each phase of the project must be completed before moving to the next.
- Agile: An iterative and flexible methodology that allows for continuous improvement and adaptation to change throughout the development process.
Each methodology has distinct advantages and challenges, making them suitable for different project types.
Key Differences Between Agile and Waterfall
Feature | Waterfall | Agile |
Planning | Detailed planning at the start | Continuous planning throughout the project |
Flexibility | Rigid, changes are difficult to implement | Highly adaptable, changes are welcomed |
Development Approach | Sequential, step-by-step execution | Iterative, with regular feedback and updates |
Speed of Delivery | Final product delivered at the end of the project | Small, working versions released in short cycles (sprints) |
Testing | Testing occurs at the end of development | Continuous testing throughout the process |
Risk Management | High risk due to late testing | Lower risk, as issues are identified and resolved early |
Customer Involvement | Limited interaction until completion | Continuous involvement and feedback |
Best For | Projects with well-defined requirements | Projects where requirements may evolve |
When to Use Waterfall
Waterfall is ideal for projects with fixed requirements and a clear end goal. It is best suited for:
- Government or regulatory projects that require strict adherence to predefined guidelines.
- Large infrastructure projects where changes would be costly.
- Projects with a predictable outcome, such as building a database system.
Waterfall offers teams a defined workflow that requires them to meet all requirements before advancement throughout the process. Changes to projects under this approach become expensive and time-intensive due to its fixed structure.
When to Use Agile
Agile thrives in dynamic and evolving environments, making it ideal for:
- Software development projects where user needs may change over time.
- Startups developing new products with uncertain requirements.
- Projects that require frequent updates and continuous customer feedback.
The iterative nature of Agile allows teams to adapt quickly to changes, ensuring that the end product remains relevant and meets user expectations.
Advantages of Agile Over Waterfall
Agile offers several benefits that make it a preferred choice for many organizations:
- Flexibility: Agile accommodates changes easily, making it suitable for projects where requirements may shift.
- Faster Delivery: Working software is delivered in short cycles, providing immediate value.
- Better Collaboration: Encourages communication between developers, stakeholders, and customers.
- Risk Mitigation: Continuous testing helps identify and resolve issues early, reducing overall project risk.
- Higher Customer Satisfaction: Frequent feedback ensures the product aligns with user expectations.
While Agile is highly effective, it requires strong communication and an ability to adapt to an evolving project scope.
How Agile Handles Changes vs. Waterfall
One of the biggest differences between Agile and Waterfall is how they handle change:
- Agile embraces change, allowing teams to make adjustments throughout the development cycle.
- Waterfall resists change, as it follows a predetermined plan with little room for modification.
Change Factor | Waterfall | Agile |
Adaptability | Fixed scope, changes are discouraged | Open to changes, scope can evolve |
Implementation of Changes | Requires formal approval and extensive rework | Integrated continuously with minimal disruption |
Customer Feedback | Limited involvement until the end | Frequent feedback, ensuring alignment with user needs |
For projects where uncertainty is high, Agile offers a more practical and effective approach.
Importance For the D487 OA
Agile together with Waterfall methods functions separately in project management situations. The selection process between Agile and Waterfall methodologies depends on how complex the project is the needs of stakeholders and adaptability requirements.
- Waterfall is best for structured, well-defined projects with minimal changes.
- Agile is ideal for dynamic projects that require frequent iterations and customer feedback.
Students enrolled in WGU D487 must learn the characteristics of Agile and Waterfall methods to pick appropriate frameworks for each project. A professional working in IT must understand how Agile or Waterfall methods should be applied to different projects in order to achieve project success.
Final Thoughts: Secure Software Design and Your WGU D487 OA 📖
Congratulations on making it through! Secure software development isn’t just about passing a test—it’s about integrating security into every step of the process.
From SAMM vs. BSIMM models to the Security Development Lifecycle (SDL) and Agile vs. Waterfall, you now understand key principles essential for building secure software. These concepts will be critical for your WGU D487 OA.
As you prepare, focus on applying these frameworks, understanding their real-world impact, and recognizing security risks. The WGU D487 OA is your chance to showcase your knowledge, so stay confident, review thoroughly, and trust in what you’ve learned.
Good luck—you’ve got this!






