WGU D075 OA Study Guide III - 2025 | Mastering IT Security and Compliance📖
Computer security and safe business functioning are the most important competencies in the present-day world backed by information technologies. This article explores key concepts in networking and information security essential for protecting systems and ensuring compliance:
- Types of Networks, Firewalls, and Security Threats: Networks like LAN, WAN, and PAN enable connectivity, while firewalls (packet-filtering, stateful, proxy) protect against cyber threats. Common security threats include malware, phishing, and DoS attacks that compromise data and disrupt operations.
- Information Security Compliance (HIPAA, FERPA, GAAP, Sarbanes-Oxley Act): Organizations must follow regulations like HIPAA (health data), FERPA (student records), GAAP (financial accuracy), and Sarbanes-Oxley (corporate accountability) to ensure data security and legal compliance.
We’ll break them all down in a clear and relatable way. Not only will this help you excel in your D075 OA questions, but it will also prepare you for success in IT management. Let’s get started and turn these critical topics into stepping stones for your future career.
How to Use This Guide for the WGU D075 OA Exam?📖
The D075 Information Technology Management Essentials OA exam at WGU evaluates your understanding of networking principles, information security, and compliance regulations. This guide simplifies the key concepts of types of network, types of firewall, security threats, and information security compliance (HIPAA, FERPA, GAAP, and Sarbanes-Oxley Act) to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D075 OA exam.

Types of Firewalls and Security Threats: Mastering the Essentials for IT Management For D075 OA📝
Firewalls and network security threats are at the heart of IT management essentials. For students navigating the WGU D075 curriculum, understanding these topics can feel like decoding a complex puzzle. Let’s break it down together in a simple and engaging way so even a sixth-grader can grasp these critical concepts.
What Are Firewalls and Why Do We Need Them?
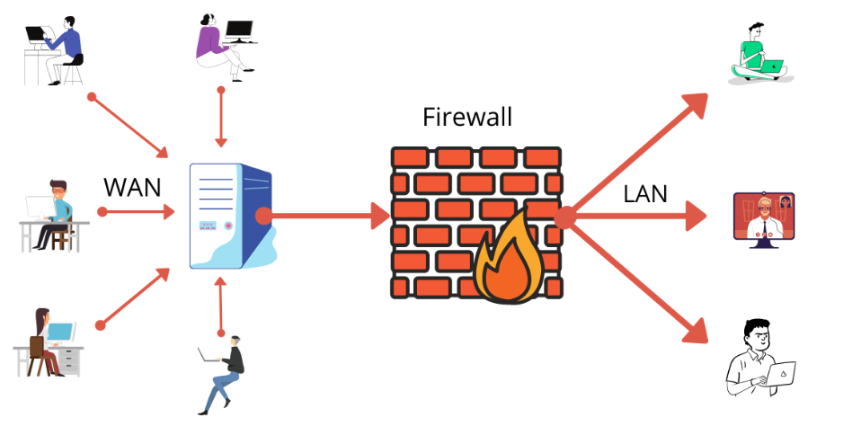
Think about the idea that your home is a computer and the Internet is a functioning city. Firewalls work like gates and doors that prevent parcels from entering while letting only good friends enter. They patrol and make sure only the desired authenticated traffic gets to ingress or egress your network.
The first of a hierarchy of controls that function together to block cyber threats is firewalls. They listen, sift, and regulate the data traffic that gets through to your network for the sake of its security. With no firewalls, your network can be likened to an open door; anyone can come in, and do a lot of damage.
Functionality of Firewalls
Firewalls do more than just block unwanted traffic; they are multi-functional tools that ensure a network’s safety. Here’s a deeper dive into what firewalls actually do:
- Traffic Monitoring and Control:
Firewalls inspect every piece of data trying to enter or leave your network. This data comes in the form of packets, which are like little envelopes containing the information being sent. Firewalls act like customs officers, opening each envelope to verify if the sender and receiver are legitimate. If something looks suspicious or doesn’t match the rules, the firewall blocks it. This constant monitoring ensures that your network only allows safe and trustworthy traffic.
- Access Control:
Firewalls enforce access control policies, deciding who or what gets in or out. Imagine a party where only guests on the list can enter. Firewalls operate similarly—they check every visitor against a set of rules. If someone’s not on the list, they’re denied entry. This prevents unauthorized users or harmful software from gaining access to your network.
- Protection Against Malware:
Malware in general which could include a virus or ransomware in a network can cause serious problems. Firewalls are barriers that prevent information from originating or passing through security on identified security threats and prevent the spread of infection. For instance, if your COMPUTER gets an unwelcome visitor with the type of virus, the firewall program will not allow the said virus to infect other devices in the network.
- Intrusion Prevention:
It is worth mentioning that today’s firewalls offer intrusion prevention systems (IPS). These systems can work in real-time to be able to identify hacking and prevent it. Imagine having a dog guard, the one that will growl and bite when someone tries to trespass.
- Application Layer Filtering:
Other firewalls are able to monitor data contents to a greater extent, for instance, proxy firewalls. For instance, they can search emails for disgusting messages or links leading to hazardous websites before they are delivered to your mailbox. Such a high level of filtering makes it impossible for the ‘bad’ stuff to even get through to do the damage.
- Logging and Reporting:
Firewalls keep a detailed log of all network activity. These logs are like security cameras that record everything, allowing IT managers to review and identify any suspicious behavior. If a breach occurs, the logs can help pinpoint what went wrong.
- Compliance with Regulations:
Most sectors demand some form of adherence to data protection regulation from the business. Firewalls assist organizations in such compliance by providing security features that guard such corporate information as healthcare records or financial data.
Support for Virtual Private Networks (VPNs):
Firewalls can sometimes act alongside VPNs to form secure remote access for employees. Think about a channel reserved for identified and approved individuals only; this is what VPN does, while firewalls make sure these channels are safe.
When integrated, these functionalities make firewalls work as protective guards, preventing your network from being a hostile ground for communication.
Types of Firewalls
Firewalls come in various types, each designed to tackle specific security challenges. The table below summarizes the most common types:
Type of Firewall | How It Works | Strengths | Limitations |
|---|---|---|---|
Packet Filtering Firewall | Acts like a checkpoint, inspecting basic packet information (e.g., source, destination) and allowing or blocking based on pre-set rules. | Fast and efficient for basic security needs. | Cannot inspect the contents of packets; vulnerable to advanced threats. |
Stateful Inspection Firewall | Monitors ongoing conversations (sessions) between devices and ensures packets are part of legitimate communication. | More secure than packet filtering, as it tracks the state of connections. | Requires more resources, which can slow down performance on large networks. |
Proxy Firewall | Serves as an intermediary between users and the internet, filtering all incoming and outgoing traffic and hiding users’ identities. | Provides anonymity and can cache frequently accessed data for quicker access. | Thorough inspections can slow down overall traffic. |
Next-Generation Firewall | Combines traditional firewall features with advanced capabilities like intrusion prevention and application monitoring. | Highly secure with multiple functionalities, making it ideal for complex networks. | Expensive and complex to manage. |
Web Application Firewall | Filters and monitors HTTP traffic between web applications and users, protecting against specific threats like SQL injection or cross-site scripting. | Specifically designed to secure websites and web apps from attacks. | Requires regular updates to remain effective against evolving threats. |
Such a format is more beneficial when assessing the kind of role or feature that each firewall type comes with, so that you can pick the best one for your use.
Understanding Security Threats For D075 OA
Securing networks requires firewalls to be in place to help fend off security threats, but just what are these threats? Here’s a detailed look at some of the most common types:
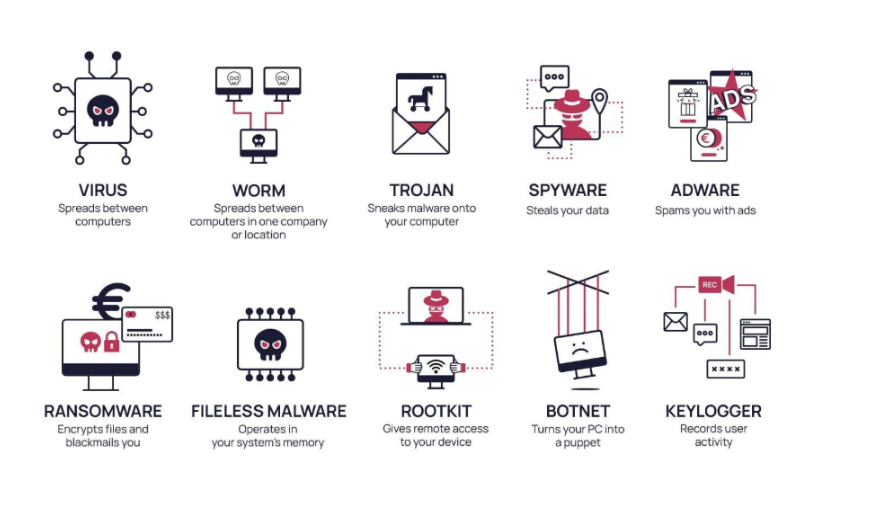
1. Malware
Malware is short for malicious software that may include viruses, worms, ransomware, and spyware. Malware specifically is software designed to execute an unauthorized function and may be deleterious to systems.
- Example: A computer virus in a hospital could mean that all patient records cannot be accessed until a ransom is paid at a particular amount.
- How Firewalls Help: This firewall’s functionality includes blocking data inflow from sites considered undesirable or dangerous and stopping the flow of viral code within a given network.
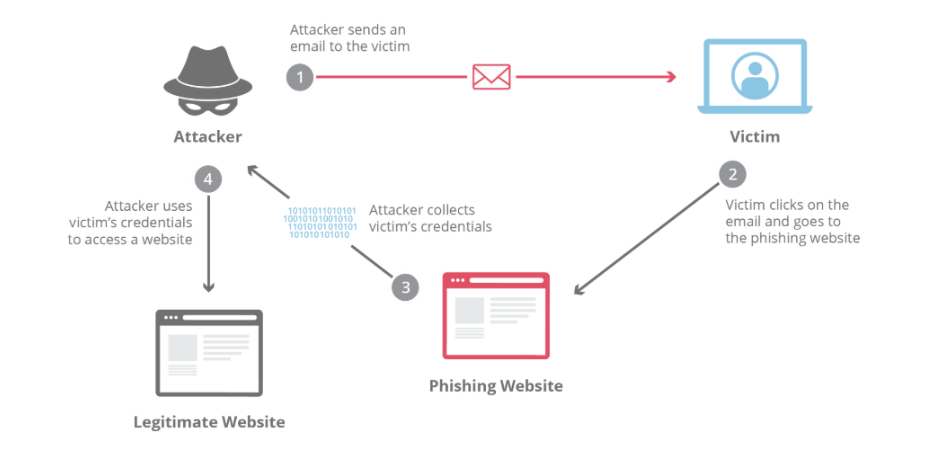
2. Phishing Attacks
Phishing is a process by which an attacker appears to be genuine in order to deceive the victims, for example, their passwords or credit card details.
- Example: Now in an example of a phishing email scam you receive an email that looks like it is from your bank, and they need for you to update your account. Merely clicking the hyperlink gets you redirected to what looks like a genuine website that targets to compel you to enter your login credentials.
- How Firewalls Help: There are firewall solutions that restrict the user from accessing phished sites as well as guarantee to eliminate deadly-looking emails.
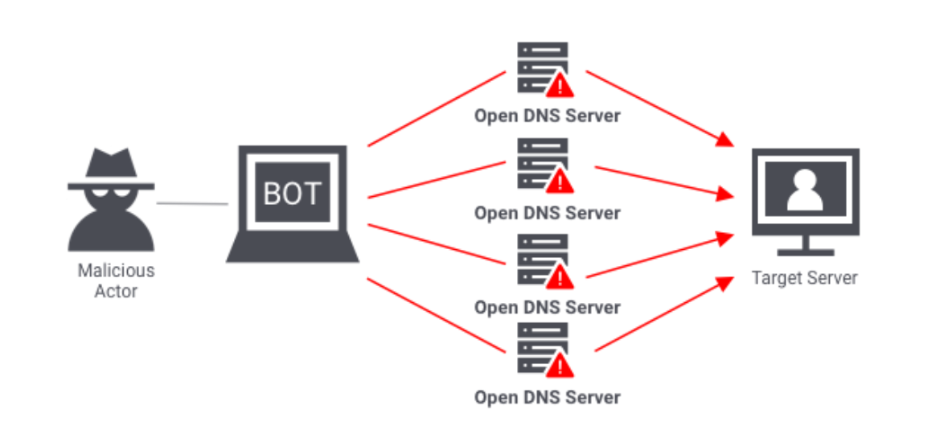
3. Denial of Service (DoS) Attacks
A DoS attack floods a system or a network with traffic that interrupts service to authorized users and makes it less functional.
- Example: Fake requests are generated aggressively during the holiday sale of an online store which makes real customers unable to access the website.
- How Firewalls Help: Firewalls can easily identify such characteristic traffic flows as DoS traffic; therefore, firewalls can counteract DoS attacks.
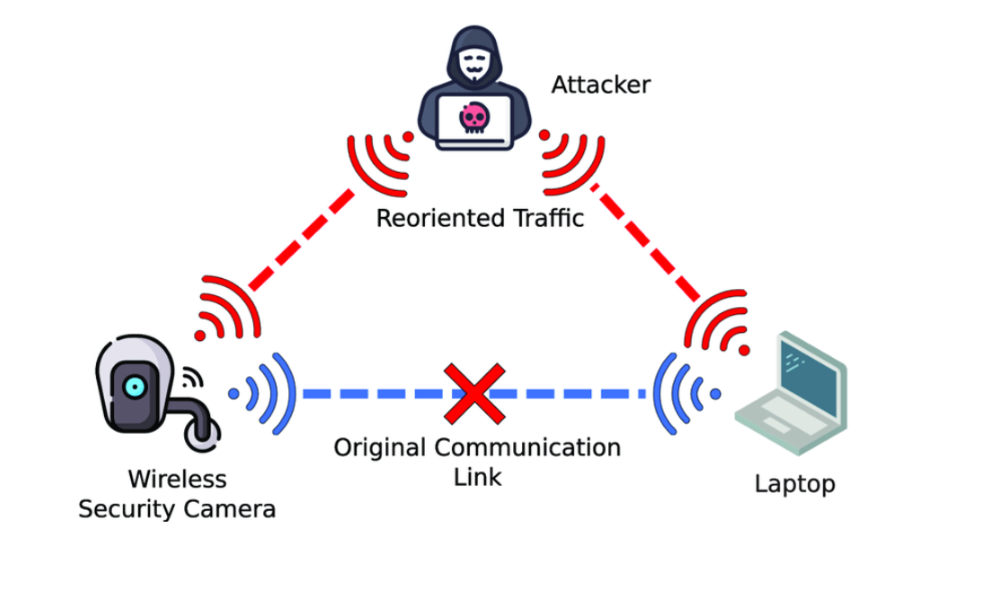
4. Man-in-the-Middle (MitM) Attacks
In a MitM attack, it becomes possible for the attacker to insert him or herself in the middle of the communicative channel between two parties without the consent of the communicating parties.
- Example: A thief eavesdrops on your connection to a free Wi-Fi network and takes your username and password when you log in to, for instance, your email.
- How Firewalls Help: Firewalls employing encryption can achieve effective blocking of attackers from monitoring the flow or even reading the contents of data being transmitted.
5. Data Breaches
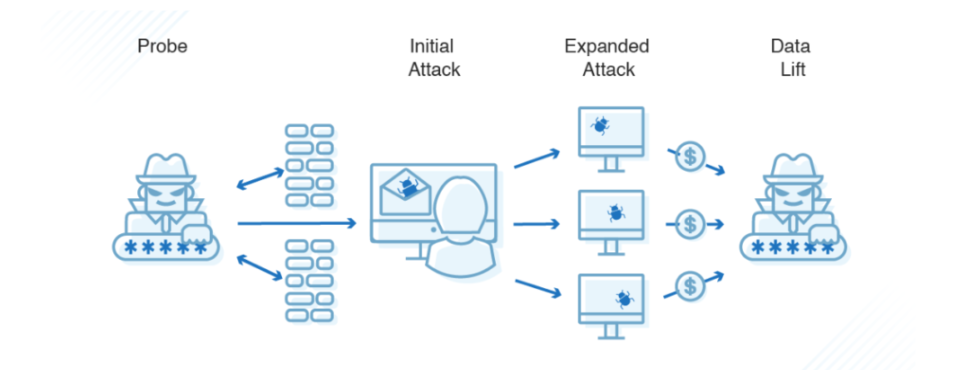
A data breach is thus a situation whereby an attacker gets unauthorized access to the database and may either steal information or make it public.
- Example: A retail company’s systems are breached and hacked into leading to the leakage of credit card details of thousands of customers.
- How Firewalls Help: Firewalls also censor who and what can pass through them and therefore only allow authorized personnel to access secure data.
6. Social Engineering
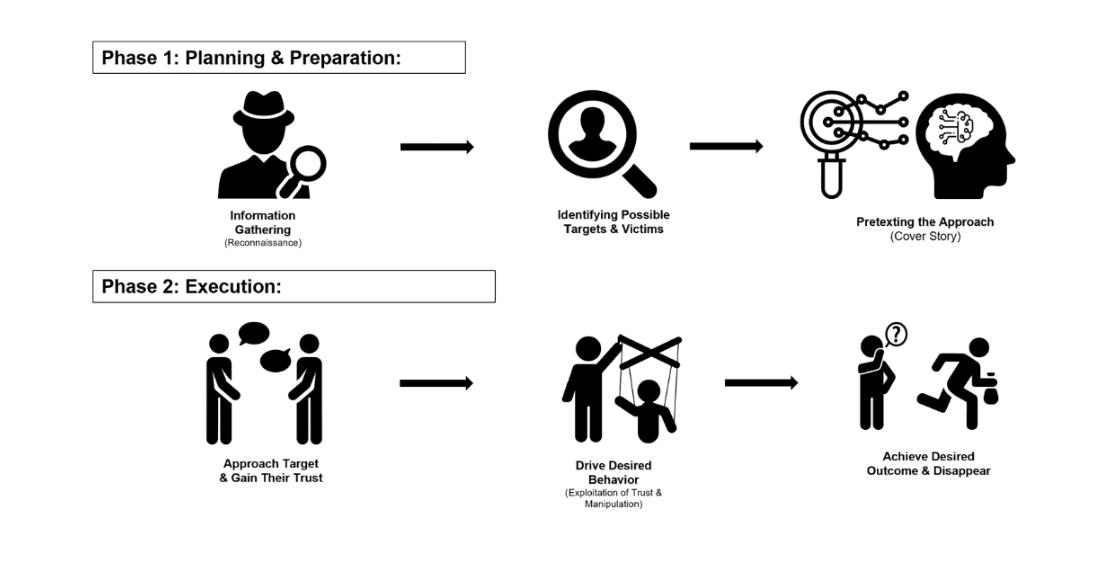
Like in phishing, social engineering consists of the use of psychological techniques to deceive people into giving out information secretly.
- Example: An attacker phones an employee and claims to be IT support and proceeds to request the employee’s login information as there is ‘some problem.’
- How Firewalls Help: In this sense, firewalls cannot prevent social engineering offenses, but they can mitigate the effects by rejecting unauthorized connection attempts.
How Firewalls and Threats Connect
Firewalls are the first line of defense against many of these threats. For instance:
- They block malware by stopping harmful packets.
- Proxy firewalls filter phishing attempts by analyzing website data.
- NGFWs identify and prevent DoS attacks in real-time.
However, firewalls alone are not enough. They need to work in conjunction with other security measures, like strong passwords, software updates, and user training, to create a robust defense.
Why This Matters for WGU D075 Students
Firewalls and threats are significant essentials in one’s training if learning WGU D075 that needs to be grasped. What you are going to learn here though will assist you significantly in D075 OA questions and is already a strong foundation for becoming to efficient IT manager.
Once you learn these fundamentals, you will have greater protection of networks, improved compliance, and data security which is always critical in the modern world that recognizes the importance of technology.
Final Thoughts
Those terms with firewalls and security threats could seem complex and scary at the first stage But if we simplify them by illustrating they are in fact easy to understand. When talking of firewalls, it will be worthwhile to liken them to doormen while the security threats are likened to unwelcome guests. Together these create a very interesting and dynamic field of IT security.
Stay tuned for more insights into WGU D075 essentials, as we continue exploring information security compliance in the next section of this series.
Understanding Information Security Compliance: Simplifying HIPAA, FERPA, GAAP, and the Sarbanes-Oxley Act For D075 OA📝
Information security compliance ensures that sensitive data is handled securely and in accordance with laws and regulations. For students studying WGU D075, understanding these compliance frameworks is vital for future careers in IT management. Let’s break down complex regulations into simple, conversational explanations and relatable examples.
What is Information Security Compliance?
Imagine you own a treasure chest filled with valuable jewels (your sensitive data). You wouldn’t just leave it open for anyone to access, right? You’d lock it, monitor it, and ensure only trusted individuals can access it. That’s what compliance does for organizations—it sets the rules for protecting the treasure.
Key principles of compliance include:
- Confidentiality: Only authorized individuals can view sensitive data.
- Integrity: Data must remain accurate and unaltered by unauthorized parties.
- Availability: Data should be accessible when needed, without unnecessary delays.
Major Compliance Regulations
Here are four major regulations, their purpose, and how they work to protect sensitive information:
- Health Insurance Portability and Accountability Act (HIPAA)
- Purpose: HIPAA protects medical information, ensuring privacy and security.
- Who It Applies To: Healthcare providers, health plans, and their business associates.
- Key Requirements:
- Protect Protected Health Information (PHI) through administrative, physical, and technical safeguards.
- Give patients rights over their health information, like accessing or correcting it.
Example: A hospital must ensure patient records are encrypted and accessible only to authorized doctors. If a doctor loses a laptop with unencrypted patient data, the hospital could face hefty fines.
- Family Educational Rights and Privacy Act (FERPA)
- Purpose: FERPA ensures the privacy of student education records.
- Who It Applies To: Schools that receive federal funding.
- Key Requirements:
- Parents can access their child’s records until the child turns 18 or enters higher education.
- Schools must obtain consent before sharing a student’s identifiable information.
Example: A school cannot share a student’s grades with a third-party app without the parent’s or eligible student’s consent. If it does, it risks penalties and losing federal funding.
- Generally Accepted Accounting Principles (GAAP)
- Purpose: GAAP provides a standardized framework for financial reporting, ensuring consistency and transparency.
- Who It Applies To: Publicly traded companies and many private organizations in the U.S.
- Key Requirements:
- Financial statements must follow consistent accounting practices.
- Accurate and transparent disclosure of financial data is mandatory.
Example: A company cannot manipulate its revenue figures to attract investors. Misstating financial information could lead to investigations and loss of credibility.
- Sarbanes-Oxley Act (SOX)
- Purpose: SOX protects investors by ensuring corporations provide truthful financial disclosures.
- Who It Applies To: Publicly traded companies in the U.S. and their accounting firms.
- Key Requirements:
- CEOs and CFOs must personally certify the accuracy of financial reports.
- Companies must establish internal controls to prevent fraud.
Example: If a CFO signs off on a fraudulent report, they could face fines or even imprisonment. SOX ensures accountability at the executive level.
Why is Compliance Important?
Adhering to compliance regulations benefits organizations in several ways:
- Protects Sensitive Data: It stops violations and unauthorized access.
- Avoids Penalties: It is important not to violate any rule at work because penalties are not only stinging financially but also legally.
- Builds Trust: Showcase security and transparency thus promoting more customer confidence.
- Encourages Accountability: Assists in promoting ethical practices within organizations.
For instance, violation of HIPAA rules can attract fines of as much as $1.5 million per violation. The failure in this compliance can trigger a data breach that results in the loss of clients and a blemished reputation.
How These Regulations Impact Organizations
The table below illustrates how compliance with these regulations affects organizations:
Regulation | Operational Impact | Financial Impact | Example |
|---|---|---|---|
HIPAA | Requires secure systems, data encryption, and staff training. | Fines up to $1.5 million per violation; additional costs for security enhancements. | A clinic invests in encrypted electronic health record (EHR) software to comply with HIPAA. |
FERPA | Schools must maintain secure student databases and train staff on record access protocols. | Risks loss of federal funding or legal actions for non-compliance. | A university implements role-based access to student records, limiting access to authorized staff. |
GAAP | requires mandatory audits, consistent practices of constructing accounting records, and the reporting of the same. | Failure to adhere to these rules has business legal consequences, decreased investors’ confidence, and reputational costs. | A company receives an audit verdict learning about errors it made in revenue-related computations. |
Sarbanes-Oxley Act (SOX) | Requires robust internal controls, ongoing compliance training, and investment in secure financial systems. | High compliance costs but improves investor trust; executives face personal liability for non-compliance. | A CFO certifies the accuracy of financial statements after thorough internal reviews. |
How to Simplify Compliance For D075 OA
Understanding compliance doesn’t have to be daunting. Here are some relatable ways to explain it:
- Compare compliance to rules in a game: Just like players must follow rules to win fairly, organizations must follow regulations to operate securely and ethically.
- Use real-world analogies: For instance, HIPAA is like a locked medical diary—it ensures no one reads your private health information without permission.
Why It Matters for WGU D075 Students
Understanding of compliance, especially among students aspiring to practice in the IT management field. These frameworks make sure that corporations do not behave immorally, keep clients’ information safe, and build up credibility in the market. It is also important that anyone in IT practicing their profession knows basic compliance that prepares them for real-life issues.
HIPAA covers handling health information, FERPA handles student records, while GAAP and SOX are for ethical and secure share reporting of financial information.
Final Thoughts
To many people, information security compliance may possibly appear complicated, but essentially it is just a process of observing certain rules that shield important information and promote records. Learning the answers to D075 OA questions is not only relevant to passing this particular course at WGU but is fundamental in order to gain a solid understanding of IT concepts in the ever-advancing technology world.
Stay tuned for more insights into WGU D075 essentials as we continue exploring the critical topics that define IT management.
Tired of reading blog articles?
Let’s Watch Our Free WGU D075 Practice Questions Video Below!

Conclusion: Achieving Excellence in WGU D075 OA with Key Business Insights📖
Mastering IT security and compliance is more than just a requirement for your WGU D075 course; it’s a crucial skill set for navigating the challenges of today’s digital landscape. From understanding how firewalls protect against cyber threats to ensuring compliance with regulations like HIPAA, FERPA, GAAP, and SOX, you now have the foundational knowledge to excel both academically and professionally.
These concepts aren’t just about protecting data—they’re about fostering trust, accountability, and efficiency in every aspect of IT management. By breaking down these complex topics into simple terms, you’re better equipped to tackle D075 OA questions and apply these principles in real-world scenarios.
As you move forward, remember that IT security and compliance are not just technical skills; they’re opportunities to lead and make a meaningful impact in the tech-driven world. Keep exploring, learning, and building on these essentials—your future as a confident IT manager awaits!






