WGU D315 OA Study Guide II - 2025 | Authentication, Authorization, and Accounting (AAA)📖
To be honest, nobody can or would like the idea of leaving doors open, be it the literal one such as your house or an open access Wi-Fi connection. However, simply keeping things closed and secure is not enough if you don’t know who is outside trying to get in and why they want to get into your house, what they do when they get in. This is where the trio commonly known as the three As- Authentication, Authorization, and Accounting or simply AAA comes in handy. Think of AAA as the ultimate bouncer at the exclusive club that is your network. And for the ones who do beat the system and get inside your house, We need a bodyguard to remove them from the premises promptly. For this task IDS and IPS will be your ally.
- IDS and IPS: Intrusion Detection Systems (IDS) monitor network traffic for threats and alert administrators, while Intrusion Prevention Systems (IPS) actively block malicious activity, preventing security breaches.
- AAA (Authentication, Authorization, and Accounting): AAA ensures secure access control by authenticating users, authorizing permissions, and accounting for actions, enhancing security and compliance in network environments.
In this article, let’s endeavor to parse out the bare basics of AAA IDS and IPS. How Authentication identifies you, Authorization determines what you’re allowed, and Accounting measures what you’ve done all in an effort to protect your network. And how IDS and IPS protect your network. If you are a tech nerd or reviewing your questions for WGU D315 OA this is your chance to get acquainted with the basics of network security. Ready to dive in? Let’s get started!
How to Use This Guide for the WGU D315 OA Exam?📖
The D315 Network and Security – Foundations OA exam at WGU evaluates your understanding of network security principles, intrusion detection, and access control mechanisms. This guide simplifies the key concepts of IDS and IPS and AAA to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D315 OA exam.

Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): Understanding the Guardians of Network Security For D315 OA📝
Imagine your house is protected by an advanced security system. One system watches and alerts you when someone suspiciously tries to enter. Another system not only watches but takes action to stop the intruder. These systems are like IDS and IPS in the world of network security, designed to safeguard data and resources from malicious activity.
What is an IDS?
An IDS also known as Intrusion Detection System is often used as the initial detection mechanism in any network security system. It checks traffic and computer systems for any issues similar to violations, intrusions, Trojans, worms, and other anomalies. IDS works when it discovers something wrong by sending a notification to the system administrators in order to analyze the situation and take necessary actions. But it does not fight or uninstall the threat itself. In other words, it is similar to a smoke alarm which alerts you of the existence of smoke but cannot put off the fire.
Types of IDS
IDS systems come in two main types, each offering distinct security functionalities to protect networks and devices from cyber threats:
1. Network-Based IDS (NIDS):
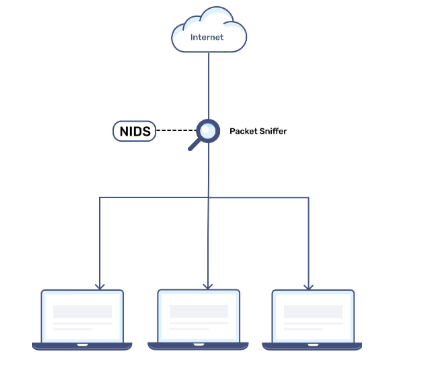
- This is a network-based IDS that inspects all traffic flowing within the network either incoming or going out. This work scrutinizes data packets as they move through the network searching for patterns of hostility or proofs of an attack.
- Strategically placed near critical points such as firewalls or network gateways, NIDS acts like a border patrol, ensuring harmful traffic doesn’t penetrate further into the system.
- For example, if an unauthorized user tries to launch a denial of service DoS attack, NIDS can detect the huge traffic flow of probably malicious traffic before the network becomes overwhelmed by it.
- NIDS excels at providing a bird’s-eye view of the entire network but may struggle to detect threats that originate from within encrypted traffic or from individual devices.
2. Host-Based IDS (HIDS):
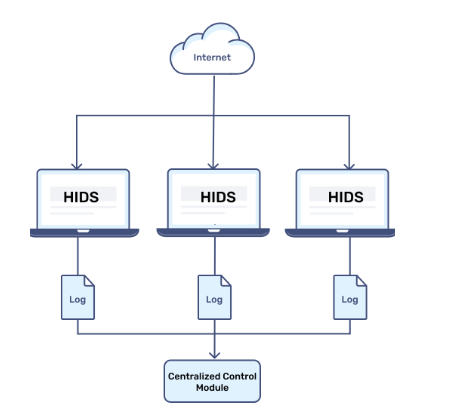
- HIDS is targeted at individual devices or end-points, such as laptop computers, servers, or workstations. Unlike other solutions that focus on the analysis of activity across the whole network, it watches over local syslog, file, and application events.
- Locally deployed on the device, HIDS functions as a bodyguard of the host, making sure any unauthorized changes or suspect activities are prevented on the host.
- For example, if a hacker tries to modify sensitive files on a server, HIDS can detect the activity and alert security teams immediately.
- HIDS is particularly useful for monitoring high-value systems containing sensitive data but requires careful configuration to avoid performance impacts on the host device.
Combined, both NIDS and HIDS offer protection since they initially scan incoming network traffic as a NIDS while the HIDS protects particular devices from internal and outside threats.
How IDS Works
IDS uses sophisticated techniques to analyze and flag potential security threats by constantly monitoring and examining network traffic and system activities. Here is a detailed breakdown of how IDS works:
- Traffic Analysis:
- The IDS inspects all incoming and outgoing data packets on a network or host.
- It examines packet headers, payloads, and traffic patterns to identify anomalies or malicious signatures.
- This inspection occurs in real-time to provide immediate alerts when a potential threat is detected.
- Signature-Based Detection:
- Relies on a database of known attack patterns or signatures.
- Compares network activity to these patterns and raises an alert if a match is found.
- Example: Detecting malware that matches a known virus signature.
- Anomaly-Based Detection:
- Establishes a baseline of normal network activity.
- Identifies deviations from this baseline, flagging them as suspicious.
- Example: Unusual login attempts at odd hours or from unexpected locations.
- Behavioral Monitoring:
- IDS can detect unusual user behaviors, such as repeated failed login attempts or access to restricted files.
- These actions, while not part of known attacks, may signify insider threats or compromised accounts.
- Alert Mechanisms:
- Generates notifications through email, SMS, or integration with a centralized security dashboard.
- Logs all detected incidents for further analysis and reporting.
- Data Logging:
- Keeps detailed records of detected activities.
- These logs are crucial for forensic investigations and improving future security measures.
- Scalability and Adaptation:
- Advanced IDS systems can scale to monitor large networks and adapt to evolving threats by incorporating machine learning to refine anomaly detection and minimize false positives.
By using these methods, an IDS provides a thorough defense mechanism, helping organizations identify potential threats before they escalate into significant security breaches.
What is an IPS?
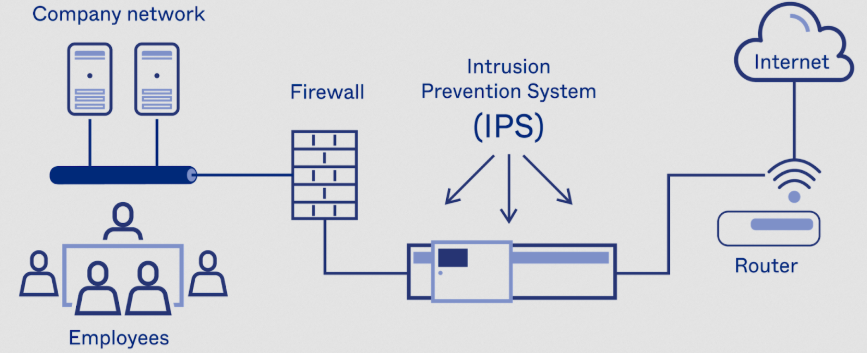
An IPS has capability more than IDS which is known as an intrusion prevention system. It’s not a tool that merely alerts you when there might be trouble; it prevents it. Sited right at the center of the traffic stream, an IPS analyzes data packets as they pass through the network looking for any wrongdoing that needs to be prevented. While an IDS functions more or less in a ‘sniffing’ mode and only alerts the user when it detects something suspicious or that conforms to a known signature, an IPS proactively examines every packet in some detail, for instance, using signature matching, or anomaly detection. Through the prevention of threats like malware or unauthorized access, it protects the network and its structure. It also has the deep packet inspection (DPI) capacity to detect well-hidden and smarter threats, providing pregnant security.
Types of IPS
Similar to IDS, IPS can also operate at different levels, providing specialized protection based on the scope and focus of the system:
- Network-Based IPS (NIPS):
- The inner flow of traffic between computers is used to monitor and secure the whole network by NIPS. They also effectively eliminate bad packets and shield against intruder attacks by scanning the data at the network boundaries or center.
- Such type of IPS is sometimes embedded in firewalls and employs complex strategies including deep packet inspection to detect potential dangers like DDoS, viruses, and phishing attacks.
- Example: If for instance, an email contains an infected file or any other malicious file, NIPS can prevent it from ever reaching the recipient or the end device.
- Host-Based IPS (HIPS):
- HIPS is installed on individual devices, such as servers, desktops, or mobile devices, to provide localized protection. It monitors system files, and application behavior, and logs for signs of malicious activity.
- HIPS is particularly effective against attacks that target specific systems, like unauthorized software installations, file modifications, or exploitation of application vulnerabilities.
- Example: If an attacker tries to execute a harmful script on a server, HIPS can block the action and alert administrators immediately.
By employing both NIPS and HIPS, organizations ensure comprehensive protection, with NIPS safeguarding the network as a whole and HIPS providing detailed defense for critical endpoints.
- Network-Based IPS (NIPS):
- Protects the entire network by blocking harmful traffic.
- Uses techniques like deep packet inspection to identify threats.
- Host-Based IPS (HIPS):
- Monitors and defends individual devices.
- Prevents activities like unauthorized application modifications or suspicious processes from running.
How IPS Works
IPS systems are designed to be proactive and operate in real-time to secure the network, ensuring that malicious activities are identified and blocked before they can cause harm. Unlike IDS, which primarily focuses on detection, IPS takes immediate actions to neutralize threats. Here’s a detailed breakdown of how they function:
- Inline Traffic Monitoring:
- Inline traffic monitoring means that the IPS is placed directly in the network’s data flow, analyzing every packet as it passes through. This strategic positioning allows the IPS to act as a gatekeeper, deciding in real time whether data packets should be allowed, blocked, or flagged for further review.
- This method ensures that malicious packets are identified and neutralized before they reach their destination, providing an essential layer of security. Unlike systems that only monitor traffic passively, inline monitoring actively filters and protects the network as data moves through.
- For example, in the case of an attempted SQL injection attack targeting a database, the IPS can recognize the malicious payload within the data packet and block it instantly, protecting the database from being compromised.
- Positioned within the data stream, analyzing every packet before it reaches its destination.
- Blocks malicious traffic while allowing legitimate data to pass through.
- Detection Techniques:
- Signature-Based Detection: Compares incoming data against a library of known attack signatures.
- Anomaly-Based Detection: Flags unusual behavior that doesn’t match the network’s normal activity patterns.
- Policy-Based Detection: Enforces predefined security rules created by administrators.
- Automated Response:
- Drops malicious packets instantly.
- Blocks IP addresses associated with attacks.
- Resets suspicious network connections to protect sensitive resources.
- Deep Packet Inspection (DPI):
- Examines packet contents in detail to detect hidden threats.
- Useful for identifying sophisticated attacks like zero-day exploits.
- Logging and Reporting:
- Records all blocked incidents and provides detailed reports for further analysis.
- Enables security teams to continuously improve their defenses.
Key Differences Between IDS and IPS
While IDS and IPS share similar goals, their functionalities differ significantly:
Feature | IDS | IPS |
Function | Monitors and detects threats | Detects and prevents threats |
Action | Sends alerts to administrators | Takes immediate action to block threats |
Response | Passive | Active |
Placement | Outside the firewall | In-line with network traffic |
Impact on Network | Minimal impact | May introduce slight latency |
Why Are IDS and IPS Important?
IDS and IPS are critical components of modern cybersecurity strategies. Here’s why:
- Threat Detection: They identify a wide range of cyber threats, including malware, unauthorized access attempts, and denial-of-service attacks.
- Compliance: Help organizations meet security standards and regulations.
- Real-Time Protection: Provide continuous monitoring and immediate action to maintain network integrity.
Challenges of Using IDS and IPS
Despite their advantages, implementing IDS and IPS systems can present challenges:
- False Positives:
- Anomaly-based detection may flag normal traffic as suspicious, leading to unnecessary alerts.
- Anomaly-based detection may flag normal traffic as suspicious, leading to unnecessary alerts.
- Performance Impact:
- Inline IPS systems can introduce slight delays in data flow.
- Inline IPS systems can introduce slight delays in data flow.
- Configuration Complexity:
- Proper tuning of detection settings requires expertise to avoid missing threats or overloading with false alerts.
- Proper tuning of detection settings requires expertise to avoid missing threats or overloading with false alerts.
Best Practices for Implementation
To optimize the effectiveness of IDS and IPS systems:
- Keep Software Updated: Regularly update signature databases and detection algorithms to counter emerging threats.
- Monitor Logs Regularly: Analyze alerts and logs to identify potential security gaps.
- Conduct Routine Testing: Test and fine-tune systems to reduce false positives and improve accuracy.
Importance For D315 OA
Consider an organization facing multiple security challenges. By deploying an IDS, it gets alerts about potential threats like unusual login attempts. Simultaneously, the IPS blocks malicious traffic targeting its web servers. In integrations, collectively, they form a complete protective periphery that prevents the lapse of valuable assets and maintains operational excellence.
Thus, IDS and IPS are significant components of the network security system that are indispensable to the understanding of network security basics. Such knowledge not only helps develop answers to the WGU D315 OA questions but also allows students ready to face real-life cybersecurity challenges.
Authentication, Authorization, and Accounting (AAA): The Pillars of Secure Network Management For D315 OA📝
Security in the World of networks is reducing the risk at the same time that allowing usability on resources is the aim and their segmentation is used. This is where the necessity to use the framework of Authentication, Authorization, and Accounting (AAA) comes from, as it is the basis of managing and protecting digital spaces. Now to break down AAA to understand its functionality and the meaning of each part let’s go ahead and discuss the principles of the model.
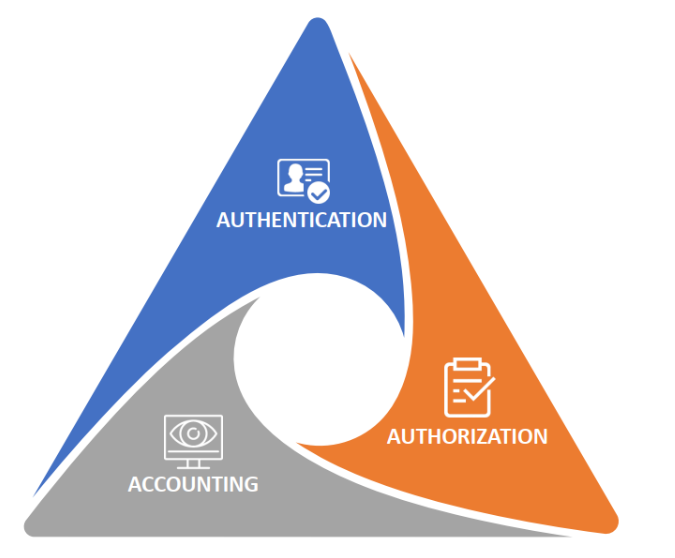
What is AAA?
AAA is a security framework designed to manage access to network resources while keeping a record of user activities. It consists of three core components:
- Authentication: Verifying who the user is.
- Authorization: Determining what the user is allowed to do.
- Accounting: Tracking user activities for auditing and compliance.
These three components work together to create a robust security infrastructure that protects against unauthorized access and ensures accountability.
1. Authentication: Verifying Identity
Authentication is the process of confirming a user’s identity before granting access to a network or system. Think of it as a digital ID check to ensure only authorized individuals can enter.
How Authentication Works
- Password-Based Authentication: Users provide a password or passphrase to verify their identity. While simple, this method is vulnerable to attacks like phishing or brute force.
- Multi-Factor Authentication (MFA): Combines two or more verification methods, such as:
- Something you know (password).
- Something you have (a security token or smartphone).
- Something you are (biometric data like fingerprints or facial recognition).
- Biometric Authentication: Uses physical characteristics unique to the user, such as fingerprints, voice, or iris patterns.
- Protocols Used:
- RADIUS (Remote Authentication Dial-In User Service): Centralizes authentication for network devices.
- TACACS+ (Terminal Access Controller Access-Control System Plus): Provides more granular control over device-level access.
Why Authentication Matters
Authentication ensures that only verified users can access network resources, significantly reducing the risk of unauthorized access and potential breaches.
2. Authorization: Defining Permissions
Once a user’s identity is verified, authorization determines what actions they are allowed to perform and what resources they can access.
How Authorization Works
- Role-Based Access Control (RBAC): Permissions are assigned based on the user’s role within the organization. For example, a manager may have access to financial data, while an intern does not.
- Discretionary Access Control (DAC): The owner of a resource decides who can access it and what actions they can perform.
- Mandatory Access Control (MAC): Access is governed by strict policies set by the organization.
- Principle of Least Privilege: Users are granted the minimum level of access necessary to perform their job functions.
Why Authorization Matters
By clearly defining what users can and cannot do, authorization prevents misuse of resources and minimizes the risk of accidental or intentional damage to the network.
3. Accounting: Monitoring and Recording Activities
Accounting involves tracking user activities and resource usage to provide insights for auditing, compliance, and troubleshooting purposes.
How Accounting Works
- Logging Activities: Records details such as login times, actions performed, and accessed resources.
- Generating Reports: Creates summaries of user behavior and system performance for review.
- Auditing: Ensures that activities comply with organizational policies and identifies any irregularities.
Why Accounting Matters
Accounting provides visibility into user actions, enabling organizations to detect and respond to suspicious activities, ensure compliance with regulations, and improve resource management.
Importance of AAA in Network Security
AAA is critical for building a secure and manageable network environment. Here’s why:
- Enhanced Security: Ensures only authenticated users access resources, enforces access policies, and monitors activity to detect potential threats.
- Granular Control: Provides network administrators with detailed control over who can access specific resources and what they can do.
- Accountability: Tracks user activities, making it easier to investigate security incidents and ensure compliance.
- Support for Modern Security Models: Plays a vital role in frameworks like Zero Trust, where every access request is verified and logged.
Real-World Applications of AAA
- Corporate Networks: Ensures employees access only the tools and data necessary for their roles.
- Cloud Services: Protects sensitive data by requiring strong authentication and tracking user activity.
- Educational Institutions: Manages access to online resources, ensuring students and staff can use the system securely.
Importance For D315 OA
Understanding the principles of AAA is essential for anyone studying network security, especially students tackling WGU D315 OA questions. By mastering Authentication, Authorization, and Accounting, students can grasp how these pillars support robust and scalable security systems, ensuring safe and efficient management of digital resources.
Tired of reading blog articles?
Let’s Watch Our Free WGU D315 Practice Questions Video Below!

Wrapping It All Up: Your Path to WGU D315 Success📖
By this point, you should be well acquainted with the AAA triumvirate—cornerstones of security in today’s networks. Each component plays a crucial role: An authentication mechanism makes certain that only authorized people can access the network, an Authorization determines what such a person is capable of doing, and an accounting maintains a logbook of all activities done. Combined they make a strong platform used in handling as well as protecting networks. Also, you should be aware of the internal workings of IDS and IPS.
As you prepare for the WGU D315 OA, remember that these concepts are not just theoretical but fundamental to real-world cybersecurity. Grasping these topics will not only help you ace the final OA but also set a solid foundation for your future endeavors in the tech world.
So, study diligently, practice what you’ve learned, and approach the exam with confidence. You’ve got this! Good luck on your journey to mastering network security and nailing your WGU D315 assessment.






