WGU D315 OA Study Guide I - 2025 | Mastering the Foundations of Cybersecurity📖
Everyone who uses the internet to perform tasks such as banking, shopping online, or even sending an email has data that they wish was protected at all times. The magic lies in two essential pillars of cybersecurity: the OSI Model and the CIA Triad. These are not mere glamorous alphabetical abbreviations that can be used to impress friends they form the basic structures of networks and information security. From watching how your Netflix streaming gets to your screen, to the facts about how your online shopping data doesn’t compromise anyone’s security, these are concepts in motion. You should comprehend these topics in order to pass the final OA of WGU D315.
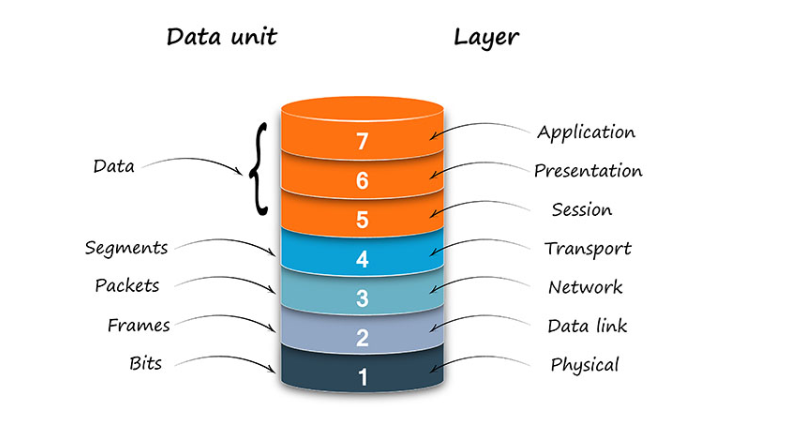
- OSI Model: The OSI (Open Systems Interconnection) Model defines seven layers—Physical, Data Link, Network, Transport, Session, Presentation, and Application—that guide how data is transmitted and processed in a network.
- CIA Triad: The CIA Triad stands for Confidentiality, Integrity, and Availability, representing core principles of information security that protect data from unauthorized access, tampering, and downtime.
Now, if for some reason you are wondering “Do I really have to learn this?”— the answer will be an absolute yes! In any case, you’re prepping for WGU D315 OA questions or just tired of being the only one not knowing what your IT friends speak about – those topics are a necessity to tame. Well, get ready because in this article we’re going to teach you cybersecurity facts and tips, in a fun and easily digestible format.
How to Use This Guide for the WGU D315 OA Exam?📖
The D315 Network and Security – Foundations OA exam at WGU evaluates your understanding of network protocols, security principles, and system architecture. This guide simplifies the key concepts of the OSI model and the CIA Triad to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D315 OA exam.
Understanding the OSI Model: A Step-by-Step Guide For D315 OA 📝
Did you ever turn your mind about how information moves through networks to integrate people, equipment, and computers? The answer is found in a brilliant structure labeled the Open Systems Interconnection (OSI) Model. In this section, we will take a closer look at what this model encompasses and discover how each of its seven layers makes this key process possible. The OSI Model is not some mere abstract concept and is, in fact, fundamental to the study of present-day computer networking. Let’s dive in!
What Is the OSI Model?
The OSI Model is a conceptual framework that helps us understand how different networking components communicate with each other. Think of it as a blueprint for how data moves from one device to another. It consists of seven distinct layers, each with specific tasks, working together to ensure smooth communication.
Imagine sending a letter: you write the message, put it in an envelope, address it, and send it through the postal system. Similarly, the OSI Model organizes data transmission in a layered structure, ensuring every step is covered.
The Seven Layers of the OSI Model

1. Physical Layer: The Foundation of Communication
The Physical Layer is the initial layer and offers facilities for all forms of network exchange. This sublayer is relevant in establishing a link between the devices through the use of cables, switches, and connectors among others. At this layer, the smallest information that can be sent is not in the form of packets or datagrams but raw data bits sent as electrical signals at high speed, light pulses, or RF signals depending on the mode of transport used. This layer describes the signals, the pins where the signal is to be connected, voltage levels, rates of data transmission, etc. For example, Ethernet cables and fiber optics are the physical transmission media for these signals Share and interpret Vonage’s signals through hubs and repeaters in order to get them across greater distances. Without Physical Layer, there would be no real means of physically transmitting or receiving data, thus, it is the most essential layer ever in a network.
- Key Responsibilities:
- Defines the physical components (e.g., cables, connectors).
- Specifies voltages, signal timing, and transmission rates.
- Manages data transmission rates and hardware specifications.
- Examples: Ethernet cables, fiber optics, network hubs, and repeaters operate at this layer.
This layer ensures that there is a physical path for the data to travel, making it the backbone of the communication process.
2. Data Link Layer: Ensuring Smooth Transfers
The functions of Data Link Layer are to accept raw data from the Physical Layer and put it in a frame for transmission. Such frames are actually structured packets of data containing headers and trailers to facilitate the passage. The layer makes sure that the transfer of data happens between nodes it addresses devices using globally assigned Media Access Control (MAC) addresses. It also enjoys self-diagnostic and eradicating features with the help of in-built algorithms and techniques such as Cyclic Redundancy Check (CRC). Through segmentation of data into frames coupled with flow control, it reduces the risks of data collisions thus enabling efficient communication between connected devices. In effect this layer polices the traffic, allowing data through to the next layer only if it is error-free.
- Key Responsibilities:
- Divides data into frames, adding headers and trailers.
- Manages Media Access Control (MAC) addresses, ensuring each device has a unique identifier.
- Detects and corrects errors in transmission through flow control.
- Examples: Ethernet protocol, Wi-Fi (802.11), and switches work at this layer.
- Sublayers:
- MAC (Media Access Control): Controls how devices access the network medium.
- LLC (Logical Link Control): Ensures data integrity and proper error checking.
This layer acts like a traffic controller, organizing and directing data to avoid collisions and losses during transmission.
3. Network Layer: The GPS of Networks
The Network Layer determines how data packets are routed across networks, playing a pivotal role in ensuring effective communication between devices. It uses logical addressing, such as IP addresses, to uniquely identify devices and define their location in a network. This layer determines the best possible route for data to travel across interconnected networks, optimizing the path based on factors like network conditions, available bandwidth, and traffic congestion. Additionally, the Network Layer is responsible for packet forwarding, which involves transmitting data from one network to another using routers. It also handles packet fragmentation and reassembly, allowing data to be sent even when networks have different maximum transmission unit (MTU) sizes. By providing these crucial services, the Network Layer acts as the GPS of networking, guiding data packets efficiently to their intended destinations across vast and complex networks.
- Key Responsibilities:
- Routes packets based on IP addresses.
- Ensures packets take the most efficient path to their destination.
- Handles fragmentation and reassembly of packets for compatibility with different networks.
- Examples: Routers and protocols like IPv4, IPv6, and ICMP operate at this layer.
Think of this layer as the GPS of networking, mapping out the best route for data to travel across interconnected systems.
4. Transport Layer: Reliable Delivery
It then identifies that the Transport Layer plays the role of creating end-to-end communication between devices through which the interconnection peripherals are reliably connected and data transfer is effectively performed. This layer creates segments of large amounts of data for the purpose of transmission and then segments them back correctly at the receiving end. An error-checking technique, it identifies and solves some problems that might be present during data transfer while ensuring that the data is received correctly. Also, LOCAL transmission protocols at the Transport Layer regulate after the data transmission to ensure that the target device used does not get overloaded with the data, by using windowing methods among others. Services like TCP (Transmission Control Protocol) are reliable because data is transmitted only if a connection is established, and then, data is resent back in case it got lost. On the other hand, the UDP provides a faster transmission for other uses such as streaming since speed is more important than anything in this instance. Look at this layer as a courier that not only guarantees that your parcel will be delivered, but also in perfect condition, and in the right order.
- Key Responsibilities:
- Segments large data into smaller pieces for easier transmission.
- Uses error detection and correction mechanisms.
- Manages data flow to prevent overloading the receiver.
- Protocols:
- TCP (Transmission Control Protocol): Ensures reliable delivery by establishing a connection and resending lost data.
- UDP (User Datagram Protocol): Faster but does not guarantee delivery, often used for streaming and gaming.
This layer is like a courier service that ensures your package is delivered securely and in the correct sequence.

5. Session Layer: Managing Conversations
The Session Layer manages the sessions or dialogues between devices, playing a crucial role in establishing, maintaining, and terminating communication sessions. Think of it as the coordinator that ensures devices can exchange data without interruptions. For instance, during an online video call, the Session Layer keeps the connection stable and synchronized, allowing participants to communicate without drops or overlaps. It also provides session recovery, meaning if the connection is interrupted, the layer ensures the session can resume from where it left off. Furthermore, this layer handles authentication to verify that devices or users are allowed to communicate, enhancing the overall security of the session. By maintaining synchronization and order, the Session Layer ensures an uninterrupted and efficient flow of data between applications on different devices.
- Key Responsibilities:
- Establishes, maintains, and terminates sessions between applications.
- Provides synchronization to ensure data flows in the correct sequence.
- Handles reconnection and authentication.
- Examples: Online video calls and file transfers depend on this layer to maintain the connection.
Imagine a moderator ensuring a meeting stays on track—this is the Session Layer’s role.

6. Presentation Layer: Data Translation
The Presentation Layer ensures that data is in a readable and usable format for the receiving application, acting as the translator of the OSI Model. This layer is responsible for interpreting data into a format that the receiving application can understand. For instance, if a file is sent in a format specific to one system, the Presentation Layer ensures it is converted into a universal format usable by the recipient’s system. Beyond translation, it provides encryption to secure data during its journey, preventing unauthorized access. Additionally, it performs data compression to reduce the size of data, making transmission faster and more efficient. Formats like JPEG for images, MP3 for audio, and ASCII for text are handled here. Without this layer, applications would struggle to interpret data correctly, and secure, efficient communication would be significantly hindered.
- Key Responsibilities:
- Converts data formats (e.g., ASCII to binary).
- Encrypts data to protect it during transmission.
- Compresses data to optimize bandwidth usage.
- Examples: SSL/TLS encryption and data format conversions like JPEG or MP3.
This layer is like a translator, ensuring that data sent in one language is understood by the recipient.

7. Application Layer: The User’s Gateway
The Application Layer interfaces directly with the end-user software in that it provides access to the network for the user. This layer enables the user to indirectly interact with network services and utilize conventional applications such as browsers, mail clients, and file transfer applications among others. It prescribes application protocols for example, HTTP for browsing, SMTP for e-mailing, and FTP for file transfer. The Application Layer also handles user network requests made through the system and makes sure that they are properly dealt with and run. For example, suppose you type in a URL in the browser to open a specific Web page; then the Application Layer handles the request. To achieve this, it offers basic services to meet the need of simplifying the overall complicated networking processes behind network applications and interfaces for network interaction to be direct.
- Key Responsibilities:
- Facilitates communication between software applications and the network.
- Defines protocols like HTTP, FTP, SMTP, and DNS.
- Examples: When you browse the web, send an email, or download a file, the Application Layer is at work.
This layer is the most visible to users and provides the tools we use every day to interact with networks.
How the OSI Model Works Together
Each layer of the OSI Model relies on the layers above and below it. For example:
- When you send an email, the Application Layer formats the message.
- The Presentation Layer encrypts the message.
- The Session Layer manages the connection to the recipient’s email server.
- The Transport Layer breaks the message into segments and ensures it’s sent without errors.
- The Network Layer determines the best route for the message.
- The Data Link Layer organizes the message into frames.
- Finally, the Physical Layer transmits the data as electrical signals over the network.
On the part of the recipient, this process is done systematically in reverse. This teamwork ensures coordination of networks, allowing the Internet, and modern applications to run as desired.
Memorizing these key concepts will be advantages when you are facing the OA of WGU D315. Now let us move on to the next topic.
Understanding the CIA Triad: The Cornerstone of Information Security For D315 OA📝
In today’s environments where global connectivity is rife and cybercrimes are on the prowl, it is important more than ever to secure data. CIA stands for confidentiality, integrity, and availability, these outline the basis of information security to this day. This framework helps organizations to protect data and make sure the information system is secure and credible. Here we will explain the CIA Triad in detail with the purpose of revealing how each aspect of the model plays a role in good cybersecurity.
What Is the CIA Triad?
The CIA Triad model is a basic model that is applied in security planning and assessment. Each element—Confidentiality, Integrity, and Availability—addresses a specific aspect of protecting information:
- Confidentiality ensures that sensitive data is accessible only to authorized individuals.
- Integrity guarantees that information remains accurate and unaltered.
- Availability ensures that information and systems are accessible when needed.
As can be seen, these three principles incorporate the formulation of extensive security policies that reduce risk and guard against cyber threats.
1. Confidentiality: Keeping Data Private
The human explanation for confidentiality is the limitation of access to sensitive information only to those personnel permitted to gain access to such information. It is such as having a diary hidden somewhere, and only you and a few selected people can open it.
- Key Methods:
- Access Controls: Senior management and HR should consider role-based permission and multi-factor authentication (MFA) in order to decide who can have access to specific data.
- Encryption: Implement data concealment where the plain language data cannot be understood in the same format whether stored or in transit.
- Data Masking: Hide some information like credit card numbers just in case it is not wanted by the wrong persons.
- Importance: Information security is significant where it is imperative to preserve the trust of customers, employees, and shareholders, follow the rules and legislation, and eliminate any possibility for a third party to use any information for their benefit. For example, encryption assures that even when the hacker intercepts the data, they cannot understand anything without the decryption key.
- Real-Life Example: Online banking platforms use HTTPS encryption to secure transactions, ensuring that account details and personal information remain confidential during transmission.
2. Integrity: Ensuring Accuracy and Trustworthiness
Integrity focuses on maintaining the accuracy and consistency of data throughout its lifecycle. It’s about ensuring that what you send is exactly what the recipient receives.
- Key Methods:
- Hashing Algorithms: Use algorithms like SHA-256 to create a unique digital fingerprint for data, ensuring that even a minor change can be detected.
- Checksums: Attach checksums to files or messages to verify their integrity during transmission.
- Digital Signatures: Authenticate data sources and ensure that information has not been tampered with.
- Importance: Integrity prevents unauthorized modifications that could lead to misinformation or fraud. For instance, accurate financial records are essential for decision-making and compliance.
- Real-Life Example: E-commerce platforms maintain the integrity of user transactions by implementing secure coding practices and conducting regular audits to detect discrepancies.
3. Availability: Ensuring Reliable Access
Availability ensures that authorized users can access information and systems whenever needed. Think of it as keeping a well-maintained bridge open so people can cross it without delays.
- Key Methods:
- Redundancy: Implement backup systems and failover mechanisms to minimize downtime.
- Disaster Recovery Plans: Develop strategies to quickly restore operations in the event of a cyber incident or natural disaster.
- Regular Updates and Maintenance: Keep hardware and software up to date to prevent vulnerabilities.
- Importance: Availability is critical for business continuity. Systems that are frequently down or inaccessible can disrupt operations and erode customer trust.
- Real-Life Example: ATMs are designed for high availability, allowing customers to access their funds at any time, even when bank branches are closed.
How the CIA Triad Works Together
While each component of the CIA Triad is vital on its own, their true strength lies in how they work together. A robust cybersecurity strategy incorporates all three principles:
- Balancing Trade-offs: For instance, increasing security through encryption (confidentiality) should not overly compromise system performance (availability).
- Identifying Weaknesses: Organizations can use the CIA Triad to evaluate potential vulnerabilities, such as weak access controls or outdated backup systems.
- Guiding Incident Response: In the event of a breach, analyzing which component of the triad was compromised helps teams respond effectively and prevent recurrence.
Real-World Applications of the CIA Triad
The CIA Triad is not just a theoretical model; it’s applied daily across industries to protect sensitive information:
- Healthcare: Adherence to such laws as HIPAA makes it possible to protect patient information, and keep records accurate and retrievable by those who have the right to access the files.
- Finance: Banks use encryption and hashing to secure transactions, while redundant systems ensure continuous access to funds.
- E-Commerce: It shows that businesses that operate online retain the data by changing them and safeguarding customer’s payments through encryptions, and other secure proceedings.
Importance For D315 OA
The CIA Triad—Confidentiality, Integrity, and Availability is also the foundation of information security. By addressing these issues, organizations will be able to create technological systems that safeguard data integrity, establish and preserve credence, and support organizational continuity. No matter if you are going through some D315 OA questions from WGU or if you are trying to work on a practical level of security then, understanding the CIA triad is a fundamental requisite in the process of building a robust cybersecurity process.
Tired of reading blog articles?
Let’s Watch Our Free WGU D315 Practice Questions Video Below!

Concluding Your Cybersecurity Journey: WGU D315 OA and the OSI Model and CIA Triad📖
The OSI Model and CIA Triad are critical concepts that are fundamental when it comes to learning about Networks and cybersecurity. The OSI Model reveals practice ways of how data passes through the layers in a network and the CIA Triad alerts of the measures needed to maintain the security, accuracy, and accessibility of such data.
Mastering these concepts is essential for success in the WGU D315 OA and beyond. They’re not just theories but practical frameworks used daily in cybersecurity. By understanding them, you’re preparing yourself for real-world challenges and opportunities in this field.
Good luck as you explore these critical topics further. Remember, the knowledge you gain here will not only help you excel academically but also equip you with skills that are highly valued in the industry. You’ve got this!






