WGU D320 OA Study Guide II - 2025 | Cloud Security: SOX, CLOUD Act, and STRIDE📖
Hello, travelers of the digital world! When it comes down to it, cloud security might seem like an unpleasant topic, this is a combination of ‘geek speak’ and legal mumbo jumbo. Together we will demystify these high-founded theories and add a little twist of humor. Let’s imagine the world of cloud security as a bustling airport. Data flows like planes in and out, security measures guard against hijackers, and everything needs to run on time. Our job? To make sure this digital airport operates safely, efficiently, and without unexpected turbulence. Enter three crucial elements:
- SOX and CLOUD Acts: The Sarbanes-Oxley Act (SOX) ensures financial transparency and accountability in organizations, while the CLOUD Act governs data storage and access across borders, particularly for U.S. law enforcement.
- Disaster Recovery and Business Continuity Planning: Disaster recovery focuses on restoring operations after an incident, while business continuity ensures ongoing business functions. RPO (Recovery Point Objective), RTO (Recovery Time Objective), MTTR (Mean Time to Repair), and MTD (Maximum Tolerable Downtime) are critical metrics for defining recovery priorities.
- STRIDE – Threat Modeling Framework: STRIDE is a security framework used to identify potential threats, encompassing Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
Buckle up, take your favorite beverage, sit back, and let me take you through how these concepts interrelate to maintain safety in our digital skies. Spoiler alert: After this, you will feel like you know everything there is to know about cloud security!
How to Use This Guide for the WGU D320 OA Exam?📖
The D320 Managing Cloud Security OA exam at WGU evaluates your understanding of cloud security compliance, disaster recovery planning, and threat modeling. This guide simplifies the key concepts of SOX and CLOUD acts, disaster recovery and business continuity planning (difference between RPO, RTO, MTTR, MTD (MAD)), and the STRIDE – Threat Modeling Framework to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D320 OA exam.

Understanding the Sarbanes-Oxley Act (SOX) and the CLOUD Act for D320 OA📝
In today’s technology-driven world, managing cloud security is more critical than ever. To help organizations ensure the safety and compliance of their data, laws like the Sarbanes-Oxley Act (SOX) and the CLOUD Act have been established. Let’s dive into these laws to understand their purpose, key provisions, and impact on cloud security.
What is the Sarbanes-Oxley Act (SOX)?
SOX was passed in 2002 because of several corporate frauds that been realized earlier in the same year like Enron and World com. The main aim is increased corporate governance, as well as the enhancement of the reliability of the provided financial information. Here’s how SOX works and its importance:
- Purpose of SOX: As its name suggests, SOX aims to prevent investor losses by enhancing the credibility of information disclosed by the firms that issue stocks. They require companies to put up a comprehensive internal control system designed principally to curb fraud and mismanagement.
- Key Provisions of SOX:
- Section 404: This section demands that the companies should establish and sustain sound internal controls over their financial reporting systems. The internal controls the independent auditors must assess and report on them.
- Section 302: Annual and quarterly reports filed by the corporations have to be certified by the senior corporate officers as not being misleading. If they do not follow the laid down rules, they suffer serious consequences.
- Impact on IT and Cloud Security:
- Data Management: Businesses need to encrypt data to avoid leakage or alteration of funds and other economic data stored on the cloud.
- Access Control: Only the relevant personalities can view or come across sensitive data.
- Audit Trails: Even in cloud environments, much documentation of all financial transactions shall be kept.
Another difficulty of SOX compliance for companies is the case if they use cloud services; the latter has to be in compliance with these regulations too. For instance, a cloud provider should provide efficient encryption, provisions on access, and recording solutions.
What is the CLOUD Act?
The CLOUD Act stands for Clarifying Lawful Overseas Use of Data Act was passed in 2018. It also discusses how police forces can use information stored in the cloud and the problems that may arise if the data is hosted in a different country. This law addresses a realization of a rise in the adoption of cloud services among companies across the globe.
- Purpose of the CLOUD Act: The CLOUD Act facilitates how U.S. law enforcement agencies obtain lawful access to data that has been stored by cloud providers based in the United States regardless of their location at the physical level.
- Key Provisions of the CLOUD Act:
- Data Access: U.S. authorities can request data from U.S. companies, regardless of where the data is stored globally.
- International Agreements: The law facilitates agreements between the U.S. and other countries, enabling smoother data sharing.
- Impact on Cloud Security:
- Data Privacy: Companies must ensure compliance with U.S. laws while also respecting the privacy laws of other countries where their data resides.
- Security Measures: Organizations must protect data from unauthorized access, whether from hackers or unauthorized governmental requests.
- Responsibility of Cloud Providers: Cloud providers need to offer tools like encryption and logging to help their clients meet these obligations.
Comparing SOX and the CLOUD Act
While both SOX and the CLOUD Act influence how organizations handle cloud security, their focus areas differ significantly:
Feature | Sarbanes-Oxley Act (SOX) | CLOUD Act |
Purpose | Ensures financial transparency and accountability | Governs law enforcement access to data |
Scope | Applies to publicly traded companies in the U.S. | Applies to U.S.-based cloud providers |
Compliance Impact | Mandatory with severe penalties for non-compliance | Indirect, focusing on data access |
Focus | Financial reporting integrity | Data privacy and cross-border access |
Why Do These Laws Matter For D320 OA?
Both SOX and the CLOUD Act shape the way organizations manage cloud security. SOX emphasizes internal controls and transparency in financial reporting, while the CLOUD Act addresses the challenges of storing data across borders. Together, these laws highlight the importance of robust security measures, ethical data management, and understanding global compliance frameworks.
For students studying cloud security in the WGU D320 module, understanding these laws equips them with the knowledge to navigate legal and ethical challenges in a globalized digital world. With such insights, they can confidently tackle WGU D320 OA questions and prepare for real-world scenarios.
Disaster Recovery and Business Continuity Planning For D320 OA 📝
This paper aims to establish the repercussions of disasters natural or man-made in businesses. To ensure that organizations can recover quickly and continue operations seamlessly, two essential strategies come into play: Business Continuity and Disaster Recovery will be examined shortly as BCM-related concepts and practices. Here are details for these concepts along with vital planning parameters RPO, RTO, MTTR, and MTD.
What is Disaster Recovery (DR)?
Disaster Recovery concentrates on the renewal of IT systems and data after the disaster has occurred. It is as if you have a plan for house construction after the storm has brought down your house. DR enables organizations to recover their essential systems or reduce their losses when an issue happens.
- Purpose of DR: DR is specifically about IT systems and data. Its goal is to restore these systems to full functionality after a disruption.
- Components of DR:
- Backup Systems: Regularly saving data to secure locations.
- Recovery Tools: Using tools and technologies to retrieve and restore data.
- Testing Plans: Simulating disasters to test recovery processes.
What is Business Continuity (BC)?
Business Continuity is a broader approach. While DR is a part of BC, this strategy ensures that the entire business can continue operating during and after a disaster. It’s like making sure you can still live comfortably while your house is being rebuilt.
- Purpose of BC: Ensures critical business functions continue, such as customer support, supply chain operations, and communication channels.
- Components of BC:
- Risk Assessments: Identifying potential threats to operations.
- Continuity Plans: Developing step-by-step guides for keeping the business running.
- Training and Testing: Preparing employees and testing plans regularly.
Key Metrics in Disaster Recovery and Business Continuity Planning
To measure and manage recovery, organizations use specific metrics:
- Recovery Point Objective (RPO):
- Definition: RPO defines how much data an organization can afford to lose, measured in time. For example, if backups are done every 12 hours, the RPO is 12 hours.
- Focus: Data recovery.
- Example: A company sets an RPO of 6 hours, meaning it can’t afford to lose more than 6 hours’ worth of data.
- Recovery Time Objective (RTO):
- Definition: RTO specifies how quickly systems must be restored after a disaster. If a company can tolerate a 4-hour downtime, the RTO is 4 hours.
- Focus: System restoration.
- Example: A critical application must be operational within 2 hours of failure.
- Mean Time to Repair (MTTR):
- Definition: MTTR is the average time taken to fix a system or component and restore it to functionality.
- Focus: Repair efficiency.
- Example: If it takes an average of 3 hours to repair a server, the MTTR is 3 hours.
- Maximum Tolerable Downtime (MTD):
- Definition: MTD is the longest period a business can afford to be offline without suffering irreparable damage.
- Focus: Business continuity.
- Example: A company sets its MTD at 8 hours, meaning any downtime beyond this could lead to significant losses.
Differences Between RPO, RTO, MTTR, and MTD
These metrics work together to form a comprehensive recovery strategy, but each has a distinct focus:
Metric | Definition | Focus | Example |
RPO | Maximum acceptable data loss in time | Data recovery | Can lose no more than 6 hours of data |
RTO | Maximum acceptable downtime in time | System restoration | Must restore services within 4 hours |
MTTR | Average time to repair a system/component | Repair efficiency | Takes 3 hours to repair a server |
MTD | Maximum downtime before unacceptable impact | Business continuity | Can tolerate being offline for 8 hours |
How These Metrics Work Together
- RPO should be less than RTO, as you want to minimize data loss before restoring operations.
- RTO and MTTR contribute to the total recovery time, which should not exceed the MTD.
Importance of DR and BC Planning
Effective disaster recovery and business continuity planning are critical for the following reasons:
- Minimizing Financial Losses: Downtime and data loss can lead to significant revenue loss.
- Maintaining Customer Trust: Ensuring uninterrupted service boosts customer confidence.
- Compliance with Regulations: Many industries require strict recovery and continuity plans to protect sensitive data.
Real-World Example
Imagine a retail company that experiences a cyberattack. If it has an RPO of 6 hours, it ensures backups are available to recover data from 6 hours before the attack. With an RTO of 2 hours, critical systems like online ordering are backed up within 2 hours, minimizing customer disruption. The MTTR for server repair is 1.5 hours, ensuring a quick resolution. However, if the attack causes downtime beyond the MTD of 8 hours, the company might face severe reputational and financial damage.
For students in the WGU D320 module, understanding these concepts is key to excelling in WGU D320 OA questions and preparing for careers in cloud security management. Proper planning ensures businesses can weather any storm and bounce back stronger.
Tired of reading blog articles?
Let’s Watch Our Free WGU D320 Practice Questions Video Below!
Understanding the STRIDE Threat Modeling Framework For D320 OA 📖
Risk assessment can be described as playing a significant role in cloud security where it is impracticable to avert risks hence the prediction of the prospective threats can help in protecting the systems necessary for the execution of an organization’s endeavors. The STRIDE threat modeling framework is one of the tools Microsoft came up with in an effort to assist people in managing risks early in the design of applications and systems. Now let’s dive into what exactly is STRIDE how it functions and why it has significance for students of cloud security.
What is STRIDE?
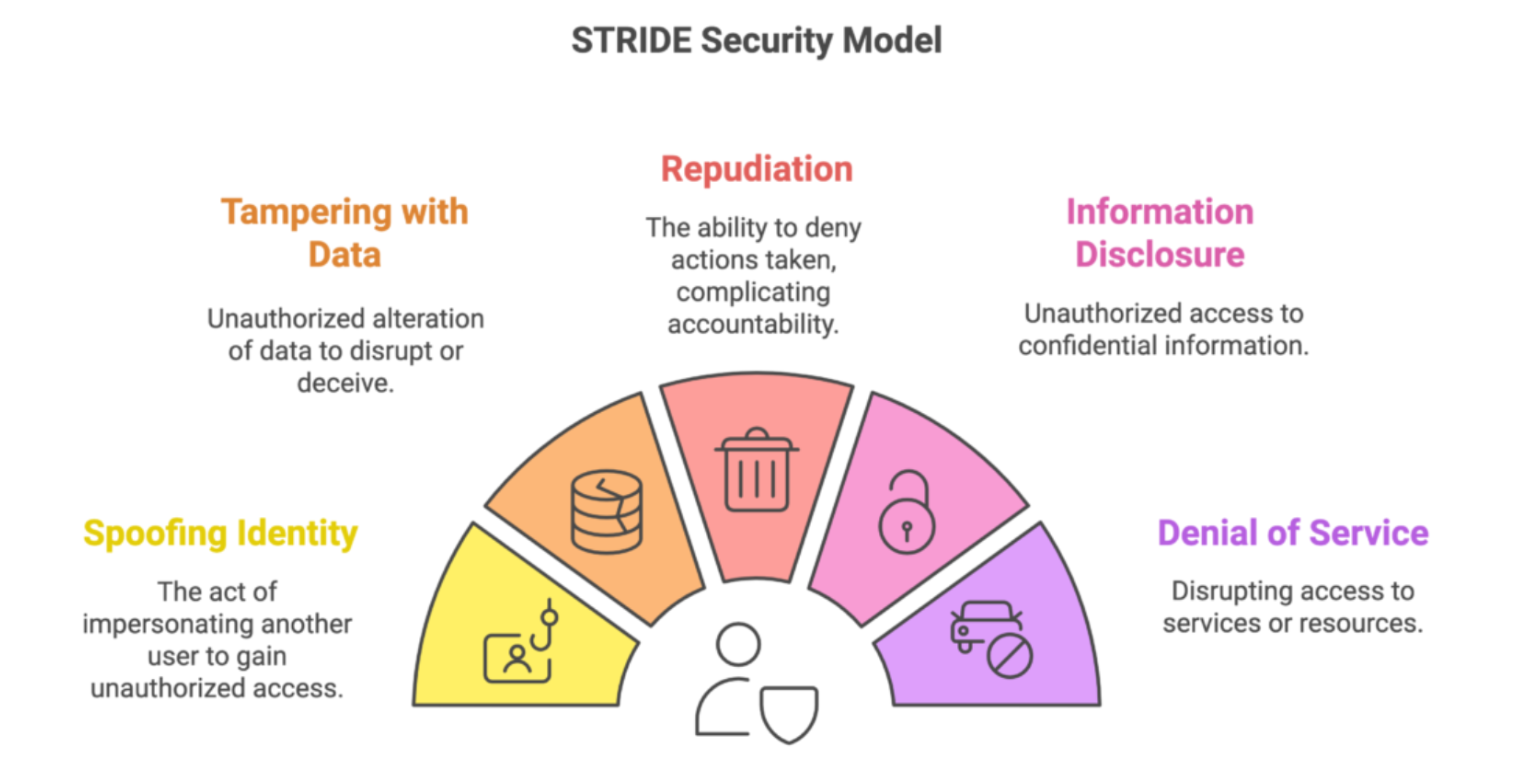
Revealing security threats in applications, STRIDE is a systematic approach. Each letter in the acronym represents a different type of threat:
- Spoofing: Faking an identity in order to be allowed into a restricted area.
- Tampering: Illegitimate modification of data or configuration of a system.
- Repudiation: Denying responsibility for actions, which makes accountability difficult.
- Information Disclosure: Gaining unauthorized access to confidential information.
- Denial of Service (DoS): Disrupting services so that legitimate users cannot access them.
- Elevation of Privilege: Gaining unauthorized access to perform actions beyond one’s permissions.
Each of these threats targets specific security principles, such as authenticity, integrity, confidentiality, availability, and authorization.
Breaking Down the STRIDE Threat Categories
Here is a closer look at each category and how it impacts cloud security:
Threat | Desired Property | Example |
Spoofing | Authenticity | An attacker impersonates a user to gain access to sensitive data. |
Tampering | Integrity | A hacker modifies configuration files to disrupt a system. |
Repudiation | Accountability | A user denies making unauthorized changes to a system. |
Information Disclosure | Confidentiality | Sensitive data is exposed due to misconfigured cloud settings. |
Denial of Service | Availability | Attackers flood a server with traffic, making it unavailable. |
Elevation of Privilege | Authorization | A user exploits a bug to gain admin-level access. |
Applying STRIDE in Cloud Security
When working with cloud environments like AWS, Azure, or Google Cloud, STRIDE helps identify and mitigate unique threats such as:
- Infrastructure Misconfigurations: Errors in the setup that can expose systems to attackers.
- Insecure APIs: Vulnerabilities in API endpoints that attackers can exploit.
- Unauthorized Access to Resources: Weak access controls that allow intrusions.
- Supply Chain Attacks: Exploiting vulnerabilities in third-party software or services.
Using STRIDE, teams can model these threats, assess risks, and prioritize mitigations to create a secure environment.
Steps for Threat Modeling with STRIDE
- Model the System: Create diagrams of the system’s processes, data flows, and trust boundaries.
- Identify Threats: Apply the STRIDE categories to each component of the system.
- Analyze and Prioritize Risks: Determine the likelihood and impact of each threat.
- Implement Mitigations: Develop security measures like encryption, authentication, or logging to address identified risks.
Real-World Examples of STRIDE
- Spoofing in Banking Apps: That is why the attackers synchronize phishing means to the impersonation of an actual representative of a chosen bank to steal login credentials.
- Tampering in Healthcare: An attacker can maliciously update the patient data within a healthcare application resulting in wrong treatment.
- Repudiation in E-commerce: A user denies authorizing a fraudulent transaction due to a lack of secure logging.
- Information Disclosure in Cloud Storage: Misconfigured permissions allow attackers to access sensitive customer data.
- Denial of Service in Retail: High traffic from an attack overwhelms servers during a major sale event.
- Elevation of Privilege in Corporate Systems: A regular employee exploits a vulnerability to gain admin-level access, exposing confidential data.
Best Practices for Using STRIDE
- Incorporate Early: Begin threat modeling during the design phase of applications.
- Collaborate: Work with cross-functional teams to cover all aspects of security.
- Regular Updates: Reassess threats after significant system changes or updates.
- Utilize Tools: Use tools like Microsoft’s Threat Modeling Tool for streamlined analysis.
Why is STRIDE Important For D320 OA?
By using STRIDE, organizations can proactively identify vulnerabilities and design robust security controls. For students in the WGU D320 module, mastering STRIDE equips them with the skills to handle real-world cloud security challenges effectively. Understanding this framework is not only essential for addressing WGU D320 OA questions but also for building safer systems in professional environments.
Whether securing a banking app, a retail website, or a healthcare platform, STRIDE empowers teams to think critically about security and protect against potential threats. With its structured approach, STRIDE remains an invaluable tool in the arsenal of cloud security professionals.

Wrapping Up Your Cloud Security Journey: A Final Prep for WGU D320 OA📖
You’ve explored the critical concepts of cloud security—from SOX’s financial oversight to the CLOUD Act’s global data management and STRIDE’s proactive threat modeling. These topics are more than just academic; they are essential tools for managing and safeguarding digital environments.
As you prepare for your final WGU D320 OA assessment, remember to revisit these frameworks and examples. Understanding SOX ensures financial transparency, the CLOUD Act teaches global data compliance, and STRIDE equips you to identify and mitigate security threats. Mastering these will not only help you excel in the exam but also build a foundation for your future career.
Take a deep breath, focus on your strengths, and go into the assessment with confidence. Good luck—you’ve got this!






