WGU D334 OA Study Guide II - 2025 | Mastering Cryptographic Security📖
Have you ever wondered how websites, online transactions, and encrypted messages stay secure in an era of cyber threats? Well, behind the scenes, cryptographic security is working its magic. But don’t worry, you don’t need to be a secret agent to understand it! This article will break down three crucial cryptographic topics:
- PKCS (Public Key Cryptography Standards): PKCS is a set of standards for implementing public-key cryptography, including protocols for encryption, digital signatures, and key management.
- Block and Key Sizes in Common Ciphers (Including Google 23BRAIDS and DEREK): This section explores block and key sizes used in common encryption ciphers, such as RSA, AES, and newer algorithms like Google’s 23BRAIDS and DEREK, which focus on security and efficiency.
- Certificate Authority Rules: Certificate Authorities (CAs) enforce rules for issuing and managing digital certificates, ensuring trust in public key infrastructure (PKI) systems, and verifying the identity of entities on the internet.
Whether you’re tackling WGU D334 OA questions or just curious about digital security, this guide will make these complex topics easy to grasp. Get ready to unlock the mysteries of cryptographic security!
How to Use This Guide for the WGU D334 OA Exam?📖
The D334 Introduction to Cryptography OA exam at WGU evaluates your understanding of cryptographic standards, encryption techniques, and digital security. This guide simplifies the key concepts of PKCS (Public Key Cryptography Standards), block and key sizes of the most common ciphers (including Google 23BRAIDS and DEREK), and certificate authority rules to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D334 OA exam.

Understanding PKCS (Public Key Cryptography Standards) For D334 OA 📝
Technology exists to protect secret communications from unauthorized access by friends-to-friend. Cryptography assists us with achieving this exact security goal. The art of information security exists through cryptography. Digital systems make use of special keys to lock and unlock messages in the same way that padlocks demand the correct keys for entry. Security standards known as PKCS (Public Key Cryptography Standards) determine key usage protocols.
The Public Key Cryptography Standards form a standardized set that enables cryptographic systems to coexist and function properly with each other. Online communications remain secure through these standards and protected along with digital signatures and encrypting data. If you’re studying WGU D334, understanding PKCS will give you a strong foundation in cryptographic security.
What is PKCS?
PKCS stands for Public Key Cryptography Standards. These are a group of rules and guidelines that help ensure cryptographic security across different applications. The standards were originally developed by RSA Security LLC in the early 1990s to promote the use of their cryptographic techniques. While PKCS is not officially an industry standard, some of its parts have been widely adopted by organizations like the Internet Engineering Task Force (IETF).
The main goal of PKCS is interoperability, meaning it helps different security systems understand and use public key cryptography in the same way. Without these standards, different software and devices might not be able to communicate securely.
Key PKCS Standards and Their Functions
PKCS consists of multiple numbered standards, each serving a different role in cryptography. The table below provides an overview of the key PKCS standards and their respective functions.
PKCS Standard | Function |
PKCS #1: RSA Cryptography Standard | Defines how RSA encryption and digital signatures work, includes message encryption functions, and provides guidelines for padding schemes. |
PKCS #3: Diffie-Hellman Key Agreement Standard | Allows two people to create a shared secret key over an insecure network and is used for secure key exchange. |
PKCS #5: Password-Based Encryption Standard | Introduces PBKDF2, a method that strengthens passwords by adding extra random data (salt) and repeating the encryption multiple times. |
PKCS #7: Cryptographic Message Syntax Standard | Used for signing and encrypting messages; forms the basis for secure email communication such as S/MIME. |
PKCS #8: Private-Key Information Syntax Standard | Defines how private keys should be stored and protected, ensuring that they are encrypted or safely encoded. |
PKCS #10: Certification Request Standard | Establishes the format of messages that request a digital certificate from a Certificate Authority (CA). |
PKCS #11: Cryptographic Token Interface | Provides a way for cryptographic devices like Hardware Security Modules (HSMs) and smart cards to store and manage encryption keys securely. |
PKCS #12: Personal Information Exchange Syntax Standard | Defines a secure file format for storing private keys and corresponding public key certificates, used in Java KeyStores and client authentication. |
PKCS #15: Cryptographic Token Information Format Standard | Ensures that users of cryptographic tokens can securely identify themselves to applications. |
Why is PKCS Important?
PKCS plays a vital role in modern cybersecurity. Here’s why it matters:
1. Ensures Secure Communication
PKCS standards make sure that sensitive information, such as passwords and private keys, remains protected. They are used in online banking, secure emails, and encrypted messaging services.
2. Promotes Compatibility
Different companies and software developers follow PKCS, ensuring that cryptographic systems can work together seamlessly.
3. Helps Prevent Cryptographic Errors
By following PKCS, developers avoid common mistakes that can lead to security vulnerabilities.
4. Strengthens Authentication Methods
PKCS standards help create digital signatures and encryption techniques that verify identities and protect sensitive transactions.
Real-World Applications of PKCS
PKCS standards are widely used in different areas of cybersecurity. Some examples include:
- Online transactions: Secure credit card payments and banking services rely on PKCS standards.
- Secure messaging: Apps like WhatsApp use PKCS-based encryption techniques.
- Digital certificates: PKCS helps verify websites and secure email communications.
- Cloud security: Many cloud providers use PKCS #11 for key management.
Understanding PKCS is just the beginning—now let’s explore block and key sizes in common ciphers, including Google’s 23BRAIDS and DEREK, to see how encryption strength plays a crucial role in cybersecurity, a key concept in WGU D334.
Understanding Block and Key Sizes in Common Ciphers For D334 OA📝
Security within cryptographic systems mainly depends on block size and key size according to cryptographic standards. Block size together with key size control both the system’s processing limitations and attack resilience. Whether you’re preparing for WGU D334 OA questions or simply exploring encryption concepts, understanding these elements is crucial.
Different encryption algorithms use different block and key sizes to provide a balance between security and performance. In this section, we’ll explore these concepts in-depth and discuss some notable ciphers, including Google’s 23BRAIDS and DEREK.
What Are Block and Key Sizes?
Block Size
The system for data encryption determines a set number of data points that the encryption cipher processes during each operation. The AES (Advanced Encryption Standard) encryption system divides data into units of 128 bits before processing each segment. Secure encryption depends on increased block size which lowers the chances that attackers could detect repeating patterns in the encryption data.
Key Size
A key size determines the length of the encryption key, measured in bits. A larger key size generally means stronger encryption, making it harder for attackers to crack the encryption using brute force methods. For example:
- AES-128 uses a 128-bit key
- AES-256 uses a 256-bit key
Larger crypto keys increase security but decrease speed because they need greater computational power. Security and performance operate as opposite factors in this system.
Symmetric vs. Asymmetric Ciphers
Encryption algorithms can be broadly classified into symmetric and asymmetric ciphers, and their key sizes differ accordingly.
Type of Cipher | Description | Key Size |
Symmetric Ciphers | Uses the same key for both encryption and decryption. Faster but requires secure key sharing. | 128, 192, 256 bits (AES) |
Asymmetric Ciphers | Uses a public key for encryption and a private key for decryption. More secure but slower. | 1024, 2048, 4096 bits (RSA) |
Common Ciphers and Their Block and Key Sizes
Below is a table summarizing some of the most commonly used encryption algorithms, including block size, key size, and other essential details.
Cipher | Type | Block Size (bits) | Key Size (bits) | Rounds | Notes |
AES | Symmetric Block | 128 | 128, 192, 256 | 10, 12, 14 | Most widely used modern cipher |
DES | Symmetric Block | 64 | 56 | 16 | Considered weak due to small key size |
3DES | Symmetric Block | 64 | 112, 168 | 48 | More secure than DES but slower |
Blowfish | Symmetric Block | 64 | 32–448 | 16 | Flexible key size |
Twofish | Symmetric Block | 128 | Up to 256 | 16 | Strong alternative to AES |
RC4 | Symmetric Stream | N/A | 40–2048 | N/A | Used in SSL but vulnerable |
RSA | Asymmetric | N/A | 1024, 2048, 4096 | N/A | Used for secure key exchange |
ECC (Elliptic Curve Cryptography) | Asymmetric | N/A | 256+ | N/A | Stronger security with shorter key size |
The Role of Google’s 23BRAIDS and DEREK
Google’s 23BRAIDS and DEREK are recent cryptographic techniques designed to enhance modern encryption protocols. While not widely known, these ciphers represent advances in secure communication and key management.
23BRAIDS
- Designed to provide lightweight, efficient encryption.
- Optimized for low-power devices and IoT security.
- Uses a balanced combination of block size and key size to achieve security with minimal processing power.
DEREK
- Developed for high-speed encryption in cloud computing.
- Features a dynamic key adjustment mechanism that enhances security while maintaining efficiency.
- Designed to resist quantum computing attacks by using advanced key expansion techniques.
How Block Size Affects Security
Block size plays a crucial role in ensuring the security of an encryption algorithm:
- Larger block sizes (e.g., 128-bit in AES) reduce the chances of pattern repetition, making encryption stronger.
- Smaller block sizes (e.g., 64-bit in DES) are more prone to collisions and dictionary attacks.
- Some encryption schemes allow variable block sizes, giving flexibility in security and performance trade-offs.
Choosing the Right Cipher for Security
When selecting a cipher, consider:
- Security requirements: Higher key sizes provide stronger security but require more processing power.
- Performance: If speed is a priority (e.g., for real-time applications), lightweight ciphers like 23BRAIDS may be a better choice.
- Compatibility: Many systems and industries have standardized encryption algorithms like AES and RSA.
Now that we’ve explored encryption fundamentals, let’s dive into the role of Certificate Authorities (CAs) in establishing digital trust and securing online identities, a critical aspect of WGU D334 OA
Tired of reading blog articles?
Let’s Watch Our Free WGU D334 Practice Questions Video Below!

Understanding Certificate Authority Rules For D334 OA📝
Online security depends entirely on the concept of trust in modern digital environments. Visitors to websites along with senders and receivers of encrypted emails rely on Certificate Authorities to verify the authenticity of all participating entities. The online security maintained through digital certificate issuance and management at the hands of CAs protects communication through both private and trustworthy methods. If you’re preparing for WGU D334 OA questions, understanding how CAs operate will give you a solid foundation in cryptographic trust systems.
What is a Certificate Authority (CA)?
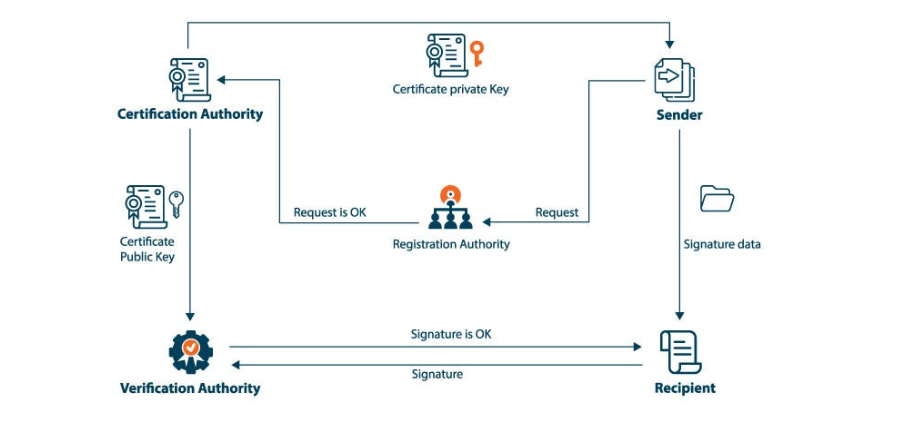
Certificate Authorities operate as trusted organizations that generate digital certificates to show that cryptographic keys actually belong to their owners. The digital certificates serve as electronic identification documents that verify website user and organizational identity to establish secure online transactions.
The Public Key Infrastructure (PKI) framework uses CAs as its fundamental element for providing secure digital interaction authenticity. Systems would lack a uniform process for online identity verification due to which they would remain exposed to impersonation risks and fraud.
Representative information within digital certificates consists of owner identification and certificate expiration time as well as the signature of the CA for authentication purposes. The process of accessing HTTPS websites requires users’ browsers to validate the website certificate with trusted CAs to establish legitimacy.
How Certificate Authorities Work
The role of a CA is not just to issue certificates but to ensure their integrity and reliability. The process of issuing a certificate follows several key steps:
1. Certificate Issuance
Before a digital certificate is issued, the applicant must first generate a public-private key pair. They then create a Certificate Signing Request (CSR), which includes their public key and identifying information. The CA verifies this information and, if everything is in order, digitally signs the certificate with its private key, linking the public key to the verified identity.
2. Trust Model
CAs operate under a trust model, where they are considered neutral and trusted by both the certificate owner and any party relying on the certificate. Web browsers and operating systems maintain a list of trusted CAs, ensuring that websites with a CA-signed certificate are authenticated as legitimate. If a certificate is issued by a trusted CA, users can confidently interact with the website without fearing impersonation attacks.
3. Certificate Usage
Digital certificates issued by CAs serve multiple purposes, including:
- Securing web browsing (HTTPS) by encrypting communications between users and websites.
- Authenticating emails using cryptographic signatures to prevent spoofing.
- Verifying digital signatures on documents to ensure authenticity.
- Enabling secure system logins by acting as credentials for authentication.
Hierarchy of Certificate Authorities
To enhance security and prevent single points of failure, CAs operate within a hierarchical structure:
CA Type | Description |
Root CA | The highest level CA, is typically kept offline to prevent attacks. It issues certificates only for Intermediate CAs. |
Intermediate CA | Acts as a middle layer between the Root CA and Issuing CA, improving security by preventing direct exposure of the Root CA. |
Issuing CA | Issues certificates to end-users and organizations for their encryption needs. |
Registration Authority (RA) | Handles identity verification before certificates are issued. |
This hierarchical structure ensures that if an Intermediate or Issuing CA is compromised, the Root CA remains secure, preserving the integrity of the entire trust chain.
Security Measures for Certificate Authorities
The implementation of security measures by CAs exists to safeguard cryptographic keys while ensuring no false certificates get released.
1. Hardware Security Modules (HSMs)
CAs store their private keys in Hardware Security Modules (HSMs)—specialized devices designed to generate, store, and protect cryptographic keys. These tamper-resistant devices prevent unauthorized access and key extraction, ensuring certificates are issued securely.
2. Offline Root CAs
Root CAs are kept offline to minimize exposure to cyberattacks. They are only activated when signing certificates for Intermediate CAs, reducing the risk of key compromise.
3. Key Ceremonies
During the creation of a CA’s private key, key ceremonies are conducted, involving multiple security personnel to ensure the key is securely generated and stored. This process prevents unauthorized access and ensures transparency in key management.
4. Access Control and Secure Storage
Only authorized personnel have access to certificate management systems. Private keys are never stored in plaintext and are securely backed up using encryption.
Certificate Revocation and Management
A digital certificate is only valid for a specified period. If a certificate is compromised, expired, or no longer trustworthy, it must be revoked. CAs maintain revocation mechanisms to prevent the continued use of invalid certificates.
Revocation Method | Description |
Certificate Revocation List (CRL) | A regularly updated list of revoked certificates that clients can check. |
Online Certificate Status Protocol (OCSP) | A real-time protocol that allows clients to verify the validity of a certificate instantly. |
Revocation ensures that certificates that are no longer secure are not trusted by browsers and systems, preventing unauthorized access and data breaches.
Risks and Challenges in CA Trust Models
While CAs are crucial to digital security, they are not infallible. Some of the most significant challenges include:
- Compromised CAs: If a CA is hacked, attackers can issue fraudulent certificates, potentially intercepting secure communications.
- Overtrust in Default CAs: Web browsers trust a large number of CAs, and if any one of them is compromised, it can pose a global security risk.
- Man-in-the-Middle Attacks: Attackers can exploit vulnerabilities in CA trust chains to impersonate legitimate websites.
Mitigation Strategies:
- Implementing DNS-based Authentication of Named Entities (DANE) to reduce reliance on CAs.
- Using Certificate Transparency Logs to track issued certificates and detect fraud.
- Encouraging organizations to use Extended Validation (EV) certificates, which require stricter verification processes.
Certificate Authorities play a crucial role in securing online interactions, and understanding their mechanisms is essential for mastering cryptography, especially for those preparing for WGU D334 OA questions.

Final Thoughts on Cryptographic Security For D334 OA 📄
Congratulations! You’ve now explored the essentials of PKCS, encryption strength, and Certificate Authority rules—three key pillars of cryptographic security. These concepts are not just theoretical; they form the backbone of secure communication, online privacy, and digital trust.
As you prepare for your WGU D334 OA, make sure you grasp these topics thoroughly. Understanding how public key cryptography works, the significance of block and key sizes, and the role of Certificate Authorities will be crucial in tackling exam questions and real-world cybersecurity challenges.
Practitioners in this field will always maintain their competitive advantage because cryptography keeps developing continuously. Continued practice combined with concept review paired with practical applications of your knowledge will lead to better results.
Best of luck with your final assessment in WGU D334 OA—you’ve got this!






