WGU D334 OA Study Guide I - 2025 | Symmetric, Asymmetric, and Public Key Infrastructure (PKI)📖
Living in a world where distant individuals can break into your messages or take your passwords would be an extremely frightening scenario. Digital protection of information under cryptography functions as an online security mechanism. The protection of your data while conducting online shopping and system login as well as sending emails remains safeguarded through the cryptographic process. WGU D334 demands an essential knowledge of encryption techniques for students to comprehend cybersecurity effectively.
This article dives into key concepts in cryptography and public key infrastructure:
- Symmetric and Asymmetric Cryptography: Symmetric cryptography uses the same key for both encryption and decryption, while asymmetric cryptography uses a pair of keys (public and private) for secure communication.
- Cipher Modes Characteristics (ECB, CBC, CFB, OFB, CTR): This section explains different cipher modes—ECB, CBC, CFB, OFB, and CTR—highlighting their security features, strengths, and weaknesses in protecting data during encryption.
- Public Key Infrastructure (PKI): PKI is a framework for managing digital certificates and public-key cryptography, ensuring secure data exchange, authentication, and digital signatures across networks.
Protecting important information has become paramount in the current digital era because knowledge of these concepts is essential for security. This piece investigates cryptography and its methods to safeguard online connectivity!
How to Use This Guide for the WGU D334 OA Exam?📖
The D334 Introduction to Cryptography OA exam at WGU evaluates your understanding of encryption methods, cryptographic modes, and public key infrastructure. This guide simplifies the key concepts of symmetric and asymmetric cryptography, cipher modes characteristics (ECB, CBC, CFB, OFB, CTR), and public key infrastructure (PKI) to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D334 OA exam.

Understanding Symmetric and Asymmetric Cryptography For D334 OA📝
The modern digital world requires absolute protection of information. Cryptography acts as a type of protected communication system that transforms information into unreadable code that needs a matching key to recover messages. Symmetric and asymmetric cryptography serve as the main cryptographic systems to provide this security solution. This text explains both methods while showing their contrasts along with their real-life applications.
Symmetric Cryptography: The One-Key System
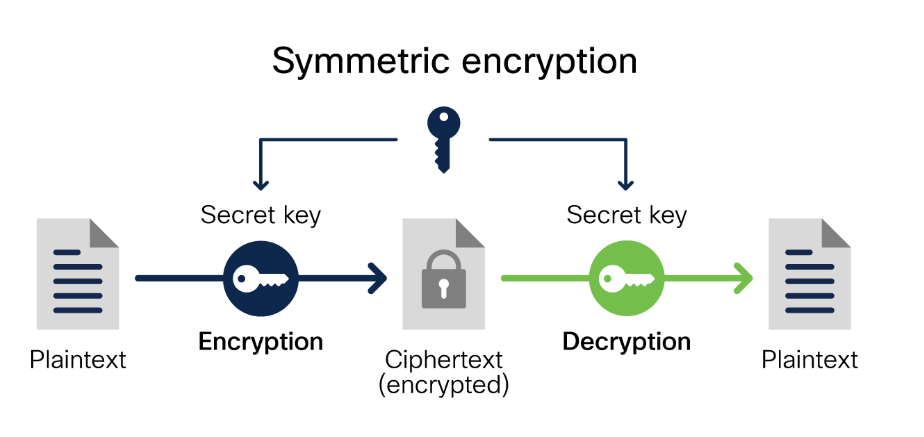
Imagine you and your friend have a special box with a lock, and you both have the same key. If you lock a message inside the box, your friend can use the same key to unlock and read it. This is how symmetric cryptography works!
How It Works
- A plaintext message is encrypted using a secret key, turning it into unreadable ciphertext.
- A particular key decrypts ciphertext to transform it into its original plaintext after being first utilized for encryption.
- Both encryption operations and decryption operations require identical keys so senders along with receivers need secure key exchange procedures before communication.
- If an attacker intercepts the key during exchange, they can decrypt all messages.
- To enhance security, the key should be changed frequently and shared through secure channels, such as using asymmetric encryption for key exchange.
Advantages of Symmetric Cryptography
- Fast and efficient: It takes less computing power, making it great for securing large amounts of data.
- Widely used: It is often used for encrypting databases, files, and messages.
Challenges of Symmetric Cryptography
- Key exchange problem: A secure method to establish identical keys between parties represents the key exchange problem due to the necessity of sharing keys without enemy interception.
- Less secure: If a hacker gets the key, they can decrypt all encrypted data.
Examples of Symmetric Cryptography
- AES (Advanced Encryption Standard) – Used for securing sensitive data.
- RC4 – Used in early versions of Wi-Fi security.
- RC5 and RC2 – Used in various encryption applications.
Asymmetric Cryptography: The Two-Key System
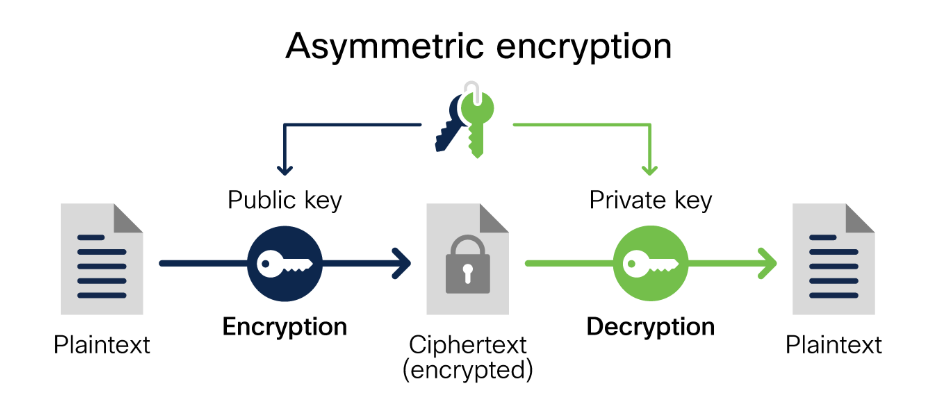
Now, imagine you have a special box that needs two keys—one to lock it and another to unlock it. One key is public (anyone can have it), but the other is private (only you have it). This is the idea behind asymmetric cryptography.
How It Works
- Asymmetric encryption relies on a pair of keys: a public key for encryption and a private key for decryption.
- The public key can be shared freely and is used to encrypt messages or data.
- The private key is kept secret and is used to decrypt the received encrypted data.
- Even if an attacker gains access to the public key, they cannot decrypt the data without the corresponding private key.
- The secure communication is achievable across public networks even when there’s no pre-established confidential key using this encryption protocol.
- Digital signatures along with SSL/TLS certificates depend on asymmetric cryptography for encryption and secure key exchanges to conduct critical online communications.
Advantages of Asymmetric Cryptography
- More secure: Secure communication remains possible because the private key stays private without sharing needs.
- Enables digital signatures: Digital signatures become possible through this method because it verifies message authenticity in secure communication scenarios.
- No need for key exchange: Unlike symmetric encryption, there’s no need to securely share a secret key beforehand.
Challenges of Asymmetric Cryptography
- Slower than symmetric encryption: Since it requires more processing power, it is not ideal for encrypting large amounts of data.
- Computationally expensive: It requires more resources, making it less efficient for everyday encryption.
Examples of Asymmetric Cryptography
- RSA (Rivest-Shamir-Adleman) – Used for secure web browsing (HTTPS).
- DSA (Digital Signature Algorithm) – Used for verifying digital signatures.
- El Gamal – Used in encryption and key exchange protocols.
Symmetric vs. Asymmetric Cryptography: Key Differences to know For D334 OA
Feature | Symmetric Cryptography | Asymmetric Cryptography |
Number of Keys | One key (same for encryption and decryption) | Two keys (public and private) |
Speed | Fast and efficient | Slower and computationally intensive |
Security | Less secure if the key is exposed | More secure since the private key is never shared |
Best Use Case | Encrypting large amounts of data | Secure key exchange and digital signatures |
Examples | AES, RC4, RC5 | RSA, DSA, El Gamal |
Now that we understand how encryption works, let’s explore different cipher modes like ECB, CBC, CFB, OFB, and CTR—each designed for specific security needs in WGU D334.
Understanding Cipher Modes and Their Characteristics For D334 OA📝
Now that we understand how encryption works, let’s explore different cipher modes like ECB, CBC, CFB, OFB, and CTR—each designed for specific security needs in WGU D334.
What Are Cipher Modes?
Cipher modes define how encryption algorithms process data. They ensure that encryption is secure and efficient by determining how plaintext is converted into ciphertext. Some modes focus on confidentiality, while others emphasize error handling and performance. Choosing the right cipher mode depends on the type of data being encrypted and the security requirements of the system.
Electronic Codebook (ECB) Mode
ECB is the simplest encryption mode. It encrypts each block of plaintext independently using the same encryption key. While this makes ECB straightforward and fast, it also presents a significant security risk. Since identical plaintext blocks produce identical ciphertext blocks, patterns in the original data remain visible, making it vulnerable to attacks.
One major drawback of ECB is its predictability. If an attacker analyzes ciphertext, they can detect repeating patterns and infer information about the plaintext. This makes ECB unsuitable for encrypting large amounts of structured data. However, it is sometimes used for encrypting small, random pieces of information like cryptographic keys.
Key Features of ECB:
- Simple and efficient for small amounts of data.
- Does not introduce additional randomness.
- Vulnerable to pattern analysis attacks.
Cipher Block Chaining (CBC) Mode
To overcome ECB’s security flaws, CBC mode introduces chaining. Each plaintext block is XORed with the previous ciphertext block before being encrypted. The first block uses an Initialization Vector (IV) to ensure randomness.
This dependency between blocks improves security, making pattern analysis nearly impossible. However, CBC has a downside: error propagation. If a single bit is altered during transmission, it will affect subsequent blocks, making decryption difficult.
CBC is commonly used for securing file encryption and database protection because it provides strong confidentiality while remaining computationally efficient.
Key Features of CBC:
- Prevents identical plaintext blocks from producing identical ciphertext.
- Requires an IV for the first block to introduce randomness.
- Can suffer from error propagation, where one corrupted bit affects multiple blocks.
Cipher Feedback (CFB) Mode
CFB mode transforms a block cipher into a stream cipher, allowing encryption of data in smaller units than the block size. Instead of encrypting plaintext directly, CFB encrypts an IV and then XORs it with the plaintext.
This mode is particularly useful for applications that require real-time encryption, such as network transmissions and streaming data. Unlike CBC, errors do not propagate beyond the affected section, making it more resilient to data corruption.
Key Features of CFB:
- Converts block ciphers into stream ciphers.
- Suitable for encrypting small, continuous data streams.
- Less vulnerable to error propagation compared to CBC.
Output Feedback (OFB) Mode
OFB mode is another variation that converts a block cipher into a stream cipher. Instead of using the previous ciphertext block for encryption (like CBC), OFB continuously encrypts an IV to generate a keystream, which is then XORed with the plaintext.
One advantage of OFB is that it does not propagate errors—a bit error in one block does not affect other blocks. However, like other stream cipher modes, it requires a unique IV for each encryption session to prevent vulnerabilities.
Key Features of OFB:
- Converts block ciphers into stream ciphers.
- Prevents error propagation.
- Requires a secure, unique IV for each encryption session.
Counter (CTR) Mode
CTR mode is one of the most efficient cipher modes available. It encrypts a continuously incrementing counter value, producing a unique keystream for each block. The keystream is then XORed with the plaintext to generate the ciphertext.
One of the biggest advantages of CTR mode is its ability to support parallel encryption. Unlike CBC and CFB, which require sequential processing, CTR can encrypt multiple blocks simultaneously, making it highly suitable for high-speed encryption applications like VPNs, disk encryption, and secure communications.
Key Features of CTR:
- Supports parallel encryption, making it highly efficient.
- Ensures unique keystreams for each block.
- No need for padding, reducing processing overhead.
Comparison of Cipher Modes
To summarize the differences between these modes, the following table highlights their strengths and weaknesses:
Cipher Mode | Best Use Case | Security Level | Speed |
ECB | Encrypting cryptographic keys | Low | Fast |
CBC | File and database encryption | High | Moderate |
CFB | Streaming data encryption | High | Moderate |
OFB | Secure data transmissions | Moderate | High |
CTR | High-speed encryption (VPNs, disk encryption) | High | Very Fast |
Secure digital communication reaches its base with Public Key Infrastructure (PKI) which provides essential authentication and encryption features for WGU D334.
Tired of reading blog articles?
Let’s Watch Our Free WGU D334 Practice Questions Video Below!

Understanding Public Key Infrastructure (PKI) For D334 OA📝
Public Key Infrastructure (PKI) serves as an internet communication framework that utilizes digital certificates together with asymmetric encryption for secure operations. The encryption system enables secure online operations because it protects important information while authenticating genuine participants in cryptographic communications. PKI serves as a base technology that secures web transactions in addition to providing email communication and digital signature verification and enabling secure login systems.
PKI bases its functionality on asymmetric encryption with two main cryptographic keys known as public keys and private keys. The sender encrypts messages through the recipient’s public key to establish secure messaging. Through private key possession, only the message recipient can decrypt and reveal its contents. PKI maintains encrypted web transactions and provides four essential security features namely confidentiality integrity authentication and non-repudiation.
How PKI Works
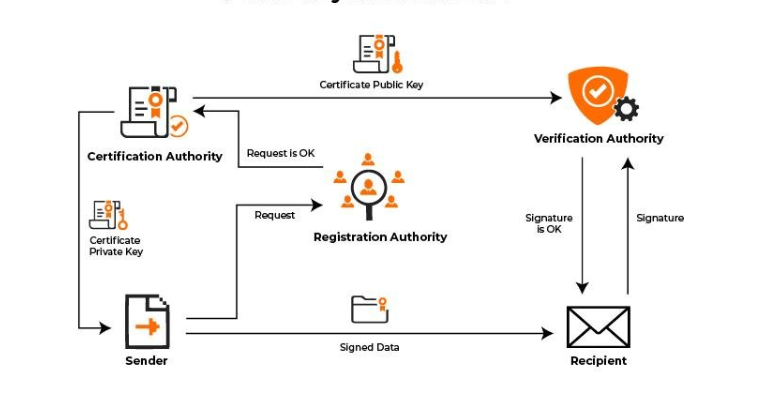
The PKI system functions through a combination of encryption, digital certificates, and trusted authorities. Here’s how the process works step by step:
- Key Generation: A unique pair of public and private keys is created for a user or entity.
- Certificate Issuance: A trusted Certificate Authority (CA) issues a digital certificate, binding the public key to the identity of the owner.
- Encryption & Authentication: The public key encrypts messages, while the private key decrypts them. This process also verifies sender authenticity.
- Certificate Verification: A Registration Authority (RA) validates user identity before certificates are issued.
- Revocation & Expiry: If a certificate is compromised, it can be revoked using a Certificate Revocation List (CRL) or verified using Online Certificate Status Protocol (OCSP).
Key Components of PKI
Several components work together to ensure the effectiveness of PKI. Understanding these components is crucial for grasping the overall security framework.
Component | Function |
Public Key | Encrypts data, available to everyone |
Private Key | Decrypts data, kept secret by the owner |
Digital Certificates | Binds a public key to an entity and verifies its authenticity |
Certificate Authority (CA) | Issues, stores, and revokes digital certificates |
Registration Authority (RA) | Verifies the identity of users requesting certificates |
Certificate Revocation List (CRL) | Lists revoked or expired certificates |
Online Certificate Status Protocol (OCSP) | Provides real-time verification of certificate validity |
Hardware Security Module (HSM) | Securely stores cryptographic keys and ensures their safe management |
Why is PKI Important?
The fundamental role of PKI exists to protect digital communications in modern systems. User data remains exposed to cyber-attacks and unauthorized access along with potential identity theft because of its absence. Here’s why PKI is essential:
- Ensures Secure Communication: PKI maintains protected communication by safeguarding sensitive data thus stopping both spying and unlawful entry attempts.
- Verifies Identities: Digital certificates provide identity verification to stop users from pretending to be someone else and carrying out fraudulent activities.
- Maintains Data Integrity: Such communication methods ensure data stays authentic from the point of origin to its destination.
- Supports Digital Signatures: Digital signatures are supported through PKI for establishing both secure electronic documents and legal transactions.
- Enables Secure Web Browsing: A PKI lets websites establish security over HTTPS through SSL/TLS certificates.
How PKI Relates to Cryptography
PKI is built on both symmetric and asymmetric encryption. Asymmetric encryption (public-private key pair) is used for authentication and secure key exchange, while symmetric encryption (shared secret keys) is used for bulk data encryption after a secure exchange has occurred. This hybrid approach optimizes both security and performance in encryption-based systems.

Final Thoughts: Prepare for Success in WGU D334 OA📄
Cryptography is the foundation of secure digital communication, and mastering its core principles—symmetric and asymmetric encryption, cipher modes, and PKI—is essential for any cybersecurity professional. These concepts will not only help you protect information but will also be tested in your final Objective Assessment (OA) for WGU D334.
Make sure to grasp each concept thoroughly, review practical applications, and test your knowledge with practice questions. Cryptography might seem complex at first, but with the right understanding, it becomes a powerful tool in securing the digital world. Stay confident, study well, and you’ll be ready to ace your WGU D334 OA.
Good luck!






