WGU D336 OA Study Guide - 2025 | Mastering IT Service Management📖
Embrace your world of IT service management, where business strategies are dealt with together with technology to ensure a smooth business flow. In this article, you will uncover three significant concepts that are not only vital in helping you pass your WGU D336 module but are also important for understanding why IT is imperative to business success.
This article explores essential frameworks and processes for business analysis and service management:
- PESTLE Analysis: PESTLE Analysis examines the external factors—Political, Economic, Social, Technological, Legal, and Environmental—that impact an organization’s strategic decisions and performance.
- Service Request Management and Incident Management: These are two critical IT service management processes: Service Request Management handles customer requests for services, while Incident Management focuses on restoring normal service operations as quickly as possible after disruptions.
- Service Value System (SVS) and Service Value Chain (SVC): SVS is a holistic approach to managing value creation through services, while the Service Value Chain is a model that outlines how an organization delivers services, from design to delivery and improvement.
Whether you’re preparing for WGU D336 OA questions or curious about IT operations, this article will guide you step by step. Ready? Let’s set sail!
How to Use This Guide for the WGU D336 OA Exam?📖
The D336 Business of IT – Applications OA exam at WGU evaluates your understanding of business analysis frameworks, IT service management, and value-driven service strategies. This guide simplifies the key concepts of PESTLE analysis, service request management and incident management, and the Service Value System (SVS) and Service Value Chain (SVC) to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D336 OA exam.

PESTLE Analysis: A Guide to Understanding Business Environments For D336 OA📝
Have you ever asked yourself how some companies choose locations to establish new offices extend existing ones or even launch a new product or enhance a service line? Most of the time, these decisions are not arrived at without appropriate research has been conducted. Among the most common tools that companies use in environmental analysis is the PESTLE Analysis. When doing WGU’s Business of IT Applications module (D336), knowledge about PESTLE Analysis is of very high importance. Now that we know what it is and how let’s try to grasp its significance.

What is PESTLE Analysis?
PESTLE stands for Political, Economic, Social, Technological, Legal, and Environmental factors. It is a structured framework businesses use to understand the broader environment in which they operate. Let’s break it down further:
- Political: These factors include government policies, political stability, tax laws, and trade restrictions. For instance, a company expanding into a new country must understand the local government’s stance on business regulations and international trade policies.
- Economic: This concentrates on how the state of affairs such as inflation, interest rates, and economic growth affect a business. For instance, during inflation periods, the cost of operations of a certain business might go high ultimately reducing profit margins.
- Social: These include social factors and culture, these are the population size, population growth, and their dietary change, customers’ preferences among others. Organizations have to ensure that the things they are supplying to the market fit into the new culture — such as the increasing concern for environmental conservation.
- Technological: Technology evolves rapidly, and businesses must stay updated on innovations to maintain competitiveness. From advancements in AI to automation and digital transformation, technological factors can redefine market landscapes.
- Legal: Businesses must comply with local and international laws, such as labor laws, health and safety standards, and intellectual property regulations. Failure to adhere to these legal factors can result in penalties and reputational damage.
- Environmental: These are factors such as; climate change, sustainability, and development, resource depletion, etc. Many organizations are implementing green strategies to conform to norms put in place and also to satisfactorily attend to the growing demand for environmentally sustainable practices.
Consequently, PESTLE Analysis, which stands for Political, Economic, Sociological, Technological, Legal, and Environmental factors is designed to give businesses a brutally honest marketers’ checklist of everything that is going on at large outside a business and how this influences it. It will help them to proactively manage problems, maximize prospects, and position strategies optimally. Not only do we talk about risks of innovations but also we consider opportunities that can be derived from external opportunities for innovating companies.
Breaking Down the Components of PESTLE Analysis
This paper will argue that each part of PESTLE has a specific role in assisting organizations in managing the external context. Let’s explore these in more detail:
1. Political Factors
Political factors encompass government policies, regulations, and stability. For businesses, understanding these can mean the difference between success and failure in a particular region. For instance:
- Government Stability: In regions with unstable governments, businesses face risks like abrupt policy changes, nationalization of assets, or disruptions caused by political unrest.
- Taxation Policies: Comparing the taxation structures of different countries highly determines where a firm should establish its operations.
- Trade Agreements: Tariffs, import/export quotas, or any other trade policies work as spectacular cost and supply chain influencers.
2. Economic Factors
Economic factors determine the financial health of markets and consumers. These include:
- Inflation and Interest Rates: High inflation may reduce consumers’ purchasing power while fluctuating interest rates impact borrowing costs for businesses.
- Economic Growth: Strong growth signals higher consumer spending, creating opportunities for businesses to expand.
- Currency Exchange Rates: These influence the cost of international trading especially to countries that rely on the exportation of their manufactured products.
3. Social Factors
Social factors delve into societal trends and cultural norms that shape consumer behavior:
- Demographic Shifts: Residents that are aging would boost the use of healthcare products while technology-progressive youth could improve the uptake of technology products.
- Cultural Preferences: Businesses need to tailor their offerings to align with local tastes, traditions, and values.
- Lifestyle Trends: The rise of eco-conscious living has fueled demand for sustainable products and services.
4. Technological Factors
Technology is a rapidly evolving domain that can either propel or disrupt businesses:
- Innovation: Breakthroughs in artificial intelligence, blockchain, and the Internet of Things create new business models and revenue streams.
- Adoption Rates: Companies that embrace emerging technologies often gain a competitive edge, while late adopters risk obsolescence.
- Infrastructure: Strong digital infrastructure, such as broadband networks, can facilitate smoother operations and customer interactions.
- Innovation: Breakthroughs in artificial intelligence, blockchain, and the Internet of Things create new business models and revenue streams.
5. Legal Factor
Legal factors are non-negotiable for businesses seeking long-term success:
- Consumer Protection Laws: An important condition that companies must fulfill is avoiding and addressing unfair practices in products and marketing.
- Employment Laws: Most countries require employers to pay the workers reasonable wages and not to discriminate against any employee; they require employers to make sure that the workplace is safe for employees, and that policies are affected.
- Intellectual Property (IP) Regulations: It is crucial to safeguard patents, and to a growing extent, trademarks in an effort to protect the innovations.
- Consumer Protection Laws: An important condition that companies must fulfill is avoiding and addressing unfair practices in products and marketing.
6. Environmental Factors
Environmental considerations are increasingly integral to strategic planning:
- Climate Change: Companies in energy-intensive sectors must adapt to stricter emissions targets and renewable energy trends.
- Sustainability Practices: Recycling, energy efficiency, and eco-friendly sourcing are becoming competitive advantages.
- Natural Disasters: Businesses in regions prone to floods, earthquakes, or hurricanes need robust contingency plans.
- Climate Change: Companies in energy-intensive sectors must adapt to stricter emissions targets and renewable energy trends.
By analyzing each of these factors thoroughly, businesses gain insights into external challenges and opportunities, allowing them to devise strategies that are both resilient and forward-looking.
Why is PESTLE Analysis Useful?
PESTLE Analysis is not just important for recognizing threats It is also helpful when one is searching for opportunities. Here’s how companies use it:
- Strategic Planning: Because decision-making that involves setting goals and objectives involves formulation of needs, objectives, goals, and other factors that need to be accomplished in the future, need to be justified.
- Market Entry: Before embracing a certain market, firms evaluate the conditions of that market with the help of PESTLE.
- Risk Management: Based on Horn, Kim, Rowley, and Walters, realizing possible threats such as economic decline or increase in regulatory control enables firms in the industry.
- Product Development: Social and technological insights from PESTLE guide product innovation to meet market needs.
How PESTLE Connects with Other Tools
PESTLE works well with other analytical tools, like SWOT Analysis (Strengths, Weaknesses, Opportunities, and Threats). While PESTLE focuses on external factors, SWOT includes internal capabilities. Combining these tools gives businesses a comprehensive view of their situation.
Real-World Example
Imagine a tech company planning to launch a new product in a foreign country. Here’s how they might use PESTLE:
- Political: Are there trade restrictions? What’s the political stability like?
- Economic: Do people in this country have disposable income to buy tech products?
- Social: Are customers interested in cutting-edge technology?
- Technological: Does the country have a strong internet infrastructure?
- Legal: Are there regulations about data privacy they need to follow?
- Environmental: Is the product sustainable and eco-friendly?
This analysis helps the company decide whether the market is worth entering and what strategies to use.
Importance For D336 OA
By mastering PESTLE Analysis, you’ll not only excel in your WGU D336 module but also gain a skill that’s invaluable in real-world business scenarios. Whether it’s understanding how political changes affect industries or leveraging technology trends, PESTLE equips you to think strategically and make smarter decisions.
Understanding Service Request Management and Incident Management For D336 OA📝
When technology powers nearly every aspect of business operations, managing IT services efficiently becomes critical. Two vital processes in this domain are Service Request Management and Incident Management. If you’re studying WGU’s Business of IT Applications (D336) module, mastering these concepts will not only help you succeed academically but also prepare you for real-world IT service challenges. Let’s explore these processes step by step.
What is Service Request Management?
Service Request Management (SRM)is a refined process that guarantees user’s recurrent requests are handled professionally and orderly through Service Request Management (SRM). It involves activities that can be well estimated and are repetitive so that IT departments can render service delivery in a set time. These requests typically revolve around non-urgent and predefined needs, such as:
- Access to a software application.
- Upgrading hardware.
- Retrieving specific information.
Unlike incident management, SRM focuses on tasks that do not stem from unplanned disruptions.
Key Components of SRM
- Service Requests: These are formal submissions by users to access IT services or resources. For example, an employee might request access to a new software tool.
- Service Catalog: A comprehensive list of available IT services, typically accessed through an online portal, where users can browse and submit their requests.
Workflow for Service Request Management
The SRM process ensures requests are handled systematically:
- Submission and Categorization:
- Users submit requests via a service portal or email.
- Requests are categorized and prioritized based on predefined criteria.
- Assessment:
- The IT team evaluates the request for its validity and urgency.
- Permissions and resource availability are checked.
- Handling and Fulfillment:
- The request is executed using pre-approved workflows. For instance, installing software or providing hardware upgrades.
- Closure:
- Once completed, the user is informed, and the request is marked as resolved in the system.
What is Incident Management?
Incident Management is a very clear-cut IT service management that is directly related to addressing and addressing an interruption in as short a time as possible. An incident may be a minor issue with an application nobody has possibly seen until now, to a large disaster affecting thousands of users due to a server failure. The aim of handling such an eventuality is to minimize the disruption consequences on the business as well as on service delivery standards and time taken to address the disruption. This process is in fact the problem-solving process and a recognition of the root that needs to be fixed so that similar issues don’t occur in the future hence enhancing the reliability of the whole system.
Key Components of Incident Management
- Incident Definition: Any unplanned event that disrupts or reduces the quality of IT services.
- Incident Lifecycle: This includes detection, logging, categorization, prioritization, investigation, resolution, and closure.
Workflow for Incident Management
Here’s how incidents are typically handled:
- Detection and Logging:
- Incidents are identified through monitoring tools or user reports.
- Detailed information is recorded in a centralized system for tracking.
- Categorization and Prioritization:
- Incidents are classified based on their type and impact on the business.
- High-priority incidents are addressed first to minimize disruptions.
- Investigation and Diagnosis:
- IT teams analyze the root cause of the incident, often using historical data or knowledge bases.
- Resolution and Recovery:
- Appropriate actions are taken to resolve the issue, such as deploying patches or restarting systems.
- The aim is to restore services as quickly as possible.
- Closure:
- Once resolved, the incident is closed in the system, and users are notified of the outcome.
Importance For D336 OA
You will fully grasp pertinent IT service management concepts with these lessons and thus be ready to tackle hurdles inherent in SRM to meet user requirements or difficulties related to the management of incidents. These skills are beneficial always when doing your WGU D336 module and when working in the IT sector.
Tired of reading blog articles?
Let’s Watch Our Free WGU D336 Practice Questions Video Below!
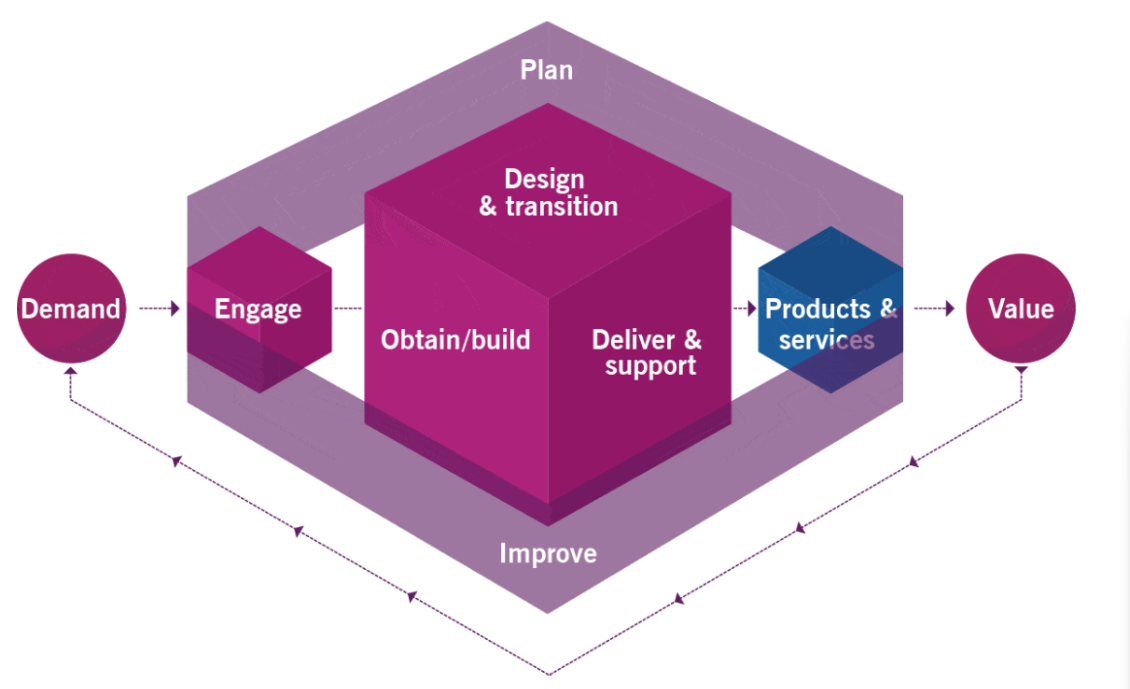
Understanding the Service Value System (SVS) and Service Value Chain (SVC) For D336 OA 📝
The Service Value System (SVS) and Service Value Chain (SVC) are integral components of ITIL 4, the modern framework for IT Service Management (ITSM). Together, they provide organizations with a structured approach to delivering value through IT services. These concepts are essential for students of WGU’s Business of IT Applications (D336) module. Let’s break them down step by step.
What is the Service Value System (SVS)?
The Service Value System is a comprehensive model that explains how various organizational components and activities work together to create value. It is a high-level framework that connects all elements of service management. The SVS consists of five key components:
- ITIL Guiding Principles These are recommendations designed to guide an organization’s decisions and actions. They focus on creating value, fostering collaboration, and promoting continuous improvement. Examples include:
- Start where you are: Build on existing resources and capabilities.
- Focus on value: Always consider what benefits stakeholders.
- Governance Governance ensures that the organization’s objectives are aligned with its actions. This involves setting policies, monitoring performance, and ensuring compliance with regulations. Governance establishes accountability across teams.
- Service Value Chain The Service Value Chain is the operational aspect of the SVS. It outlines the core activities needed to respond to demand and create value through services. More on this below.
- Practices Practices are sets of organizational resources designed to achieve specific objectives. They are more dynamic than traditional processes and adapt to changing business needs. Examples include Change Enablement, Incident Management, and Problem Management.
- Continual Improvement This focuses on enhancing services, processes, and practices over time. Continual Improvement encourages organizations to regularly assess their performance and identify areas for growth.
What is the Service Value Chain (SVC)?
The Service Value Chain is the operational model within the SVS. It is made up of six key activities that work together to transform demand into value. These activities are flexible and adaptable to different business needs:
- Plan This activity involves defining organizational goals and determining how IT services can help achieve them. Strategic planning ensures alignment between business objectives and IT capabilities.
- Improve Continuous improvement is at the heart of the value chain. This activity identifies opportunities for enhancing services and processes to meet evolving stakeholder expectations.
- Engage Building strong relationships with stakeholders is crucial. This activity involves understanding stakeholder needs and ensuring that services meet their requirements.
- Design & Transition This step focuses on designing new services or modifying existing ones. It ensures that these changes are effectively transitioned into operation without disrupting ongoing activities.
- Obtain/Build This activity includes acquiring or developing resources such as technology, people, or infrastructure needed to deliver services.
- Deliver & Support The final activity ensures the effective delivery of services and provides ongoing support to users, maintaining high levels of satisfaction and reliability.
Why Are the SVS and SVC Important?
- Optimized Service Delivery: By identifying and improving interdependent activities, organizations can reduce inefficiencies and deliver consistent value.
- Strategic Alignment: Ensures IT services are directly aligned with business objectives, creating a cohesive strategy.
- Enhanced Customer Satisfaction: By focusing on value creation and stakeholder engagement, organizations can meet or exceed user expectations.
- Agility and Adaptability: The flexible nature of the SVC allows businesses to respond to changing demands and market conditions.

Wrapping Up: Your Key to WGU D336 OA Success📄
As we conclude our journey through PESTLE Analysis, Service Request and Incident Management, and the Service Value System (SVS) and Service Value Chain (SVC), it’s clear how these concepts form the backbone of IT service management. These aren’t just abstract ideas—they’re practical tools and frameworks that ensure businesses can navigate challenges, seize opportunities, and deliver consistent value.
Mastering these topics is not just about acing your WGU D336 OA; it’s about gaining the skills to excel in IT service management roles. Remember:
- PESTLE Analysis equips you to understand external factors shaping business strategies.
- Service Request and Incident Management keep IT services running smoothly and efficiently.
- The SVS and SVC provide a comprehensive approach to delivering value through IT services.
These are essential building blocks for your future success, both in your course and in the professional world.
As you prepare for your final assessment, take time to review these concepts, apply them to real-world scenarios, and collaborate with your peers. Don’t hesitate to revisit this article whenever you need a quick refresher.
Good luck on your WGU D336 journey—you’ve got this!






