WGU D303 OA Study Guide I I - 2025 | Azure Security: A Guide to Identity Protection and RBAC📖
Greetings to an exciting tour dedicated to the sphere of Azure security! In this article, we’ll explore two powerful tools that are essential for managing cloud environments: Identity Protection and Conditional access policies, and Role-Based Access Control. If you have ever been curious about how many organizations protect their resources and at the same time make them available to the right personnel, then have a full share of it.
- Identity Protection and Conditional Access Policies: Identity protection helps detect and mitigate security risks, while conditional access policies enforce rules based on user location, device, and behavior to enhance authentication security.
- Role-Based Access Control (RBAC): RBAC restricts system access based on user roles, ensuring that employees have only the permissions needed for their job, improving security and compliance.
By the time you are through with this article, you will not only discover what these are all about but also realize why they are important to Azure’s security environment. Well then, let’s wade in and explain precisely why and how those tools make Azure a safe and efficient place for business around the world!
How to Use This Guide for the WGU D303 OA Exam?📖
The D303 Azure Fundamentals OA exam at WGU evaluates your understanding of Azure security features, identity management, and access control mechanisms. This guide simplifies the key concepts of Identity Protection and Conditional Access Policies and Role-Based Access Control (RBAC) to help you grasp the topics tested in the exam.
We also provide exam-style questions and practical applications to ensure you’re fully prepared for the questions on the WGU D303 OA exam.

Understanding Identity Protection and Conditional Access Policies For D303 OA📝
For organizations today, control and especially protection of resources is a crucial factor in the digital environment. Azure Identity Protection and Conditional Access Policies are two strong provided security features to protect user identity, as well as how and when the user can access the application. Now let’s disentangle these concepts one by one and look at how they operate and why they need to be a functional part of a genealogy organization.
What Is Identity Protection?
Identity Protection refers to a system of tools and practices that help secure user identities from threats such as unauthorized access and identity theft. Microsoft Azure provides Identity Protection through Azure Active Directory (Azure AD). Here’s what makes it important:
- Managing Identities: Identity Protection ensures that each user has a unique digital identity. It helps organizations control what users can do, which applications they can access, and under what conditions.
- Azure Active Directory (Azure AD): Azure AD is a cloud-based service that combines identity management, application access, and advanced security measures. It acts as the backbone of Identity Protection, managing how users log in and access resources.
Key Features of Identity Protection
- Risk-Based Conditional Access:
- Azure Identity Protection evaluates the risk level of user sign-ins. For example, if someone tries to log in from an unfamiliar location, it might flag the sign-in as risky.
- Based on this assessment, it can enforce additional security measures like multi-factor authentication (MFA).
- Least Privilege Principle:
- This principle ensures that users only have the permissions they need for their tasks. Elevated permissions are granted temporarily and only when necessary.
- This principle ensures that users only have the permissions they need for their tasks. Elevated permissions are granted temporarily and only when necessary.
- Multi-Factor Authentication (MFA):
- MFA adds an extra layer of security by requiring users to verify their identity in multiple ways, such as entering a code sent to their phone after typing their password.
- MFA adds an extra layer of security by requiring users to verify their identity in multiple ways, such as entering a code sent to their phone after typing their password.
- Real-Time and Offline Risk Detection:
- Azure uses advanced algorithms to detect unusual patterns, like impossible travel (logging in from two far-apart locations within a short time).
- Azure uses advanced algorithms to detect unusual patterns, like impossible travel (logging in from two far-apart locations within a short time).
- Machine Learning:
- Azure continuously learns from user behavior to detect anomalies, making it smarter at identifying potential threats.
- Azure continuously learns from user behavior to detect anomalies, making it smarter at identifying potential threats.
What Are Conditional Access Policies?
Conditional Access Policies define if the user is allowed for particular applications at certain conditions. These policies are like armed door-men at the door telling who and under what circumstances would be allowed to gain entrance into a building. They consider the context of the login, the security of the device being used, and the type of application that is being accessed. Real-time Client applications that work with Conditional Access continually respond to these circumstances and permit only the appropriate users the proper resources, all while being secure and protecting performance.
- Definition: A Conditional Access Policy allows or blocks access based on factors like user location, device type, or risk level.
- Dynamic Policies: These policies adapt to real-time risk assessments, ensuring the right level of security for every access attempt.
How Conditional Access Policies Work
Conditional Access Policies in Azure provide a highly dynamic and customizable framework to enforce security measures. Let’s break down how they function:
- Evaluating User Risk:
- The policy assesses the risk of a user’s access attempt by analyzing factors like their location, device status, and sign-in behavior. For instance, logging in from a known and compliant device in a typical location is deemed low-risk, while accessing from an unknown country raises the risk.
- The policy assesses the risk of a user’s access attempt by analyzing factors like their location, device status, and sign-in behavior. For instance, logging in from a known and compliant device in a typical location is deemed low-risk, while accessing from an unknown country raises the risk.
- Device Compliance:
- Policies verify if the accessing device meets the organization’s security standards, such as having updated antivirus software or being enrolled in the organization’s device management system.
- Policies verify if the accessing device meets the organization’s security standards, such as having updated antivirus software or being enrolled in the organization’s device management system.
- Application Sensitivity:
- Conditional Access Policies can be tailored to the sensitivity of the application being accessed. For example, a financial application might require MFA or restrict access to on-premises networks only.
- Conditional Access Policies can be tailored to the sensitivity of the application being accessed. For example, a financial application might require MFA or restrict access to on-premises networks only.
- Policy Actions Based on Conditions:
- When conditions are met (e.g., a user accesses from a secure device), the policy allows seamless access.
- If conditions are not met (e.g., accessing from an unregistered device), additional steps like MFA verification or outright denial of access are triggered.
- Granular Access Rules:
- Administrators can define highly specific rules. For instance, a rule might allow access to HR applications only during business hours and block access outside of these times.
- Administrators can define highly specific rules. For instance, a rule might allow access to HR applications only during business hours and block access outside of these times.
- Risk-Adaptive Security:
- The policies use real-time risk detection and adapt security requirements accordingly. This ensures robust protection without being unnecessarily restrictive for legitimate users.
By implementing Conditional Access Policies effectively, organizations can create a dynamic security layer that adapts to changing threats, providing both protection and user convenience.
The Role of Conditional Access in Identity Protection
Conditional Access is tightly integrated with Azure Identity Protection to create a dynamic and secure access system:
- Risk Evaluation: Based on real-time analysis, it determines whether an access attempt is safe.
- Adaptive Access: Security measures change based on assessed risk levels. For instance, high-risk users might need MFA, while low-risk users access resources seamlessly.
- Zero Trust Model: This approach assumes no user is trusted by default, requiring verification for every access attempt. Conditional Access and Identity Protection align perfectly with this model, ensuring robust security.
Best Practices for Implementing Identity Protection and Conditional Access
- Center Security Around Identities:
- Treat identity as the primary security boundary rather than relying solely on network security.
- Treat identity as the primary security boundary rather than relying solely on network security.
- Regularly Review Permissions:
- Conduct audits to ensure users have appropriate access based on their roles.
- Conduct audits to ensure users have appropriate access based on their roles.
- Leverage Azure Tools:
- Use built-in features like identity protection alerts and monitoring to stay informed about potential threats.
Why These Tools Matter
These tools are not just about stopping bad actors; they’re also about creating a seamless user experience. By intelligently managing risk, organizations can ensure that users access the resources they need without unnecessary hurdles. Students preparing for WGU D303 OA exams should understand how these tools make Azure a secure and flexible platform.
Importance For D303 OA
Azure Identity Protection and Conditional Access Policies are essential components of modern security strategies. By understanding and applying these tools, organizations can effectively safeguard their digital environments. For those tackling WGU D303 OA questions, mastering these concepts is a step toward excelling in Azure fundamentals and becoming proficient in managing cloud-based identities and access policies.
Understanding Role-Based Access Control (RBAC) For D303 OA 📝
In as much as there are significant benefits associated with cloud computing, the issue of managing who gains access to organizational resources hosted within the cloud is one of the most sensitive security concerns that organizations need to address effectively. Azure RBAC is a rich model to implement and authorize users, groups, service principals, and managed identities in Azure resources. To aid our understanding let’s look at how this works in a step-by-step manner with reasons behind its requirement.
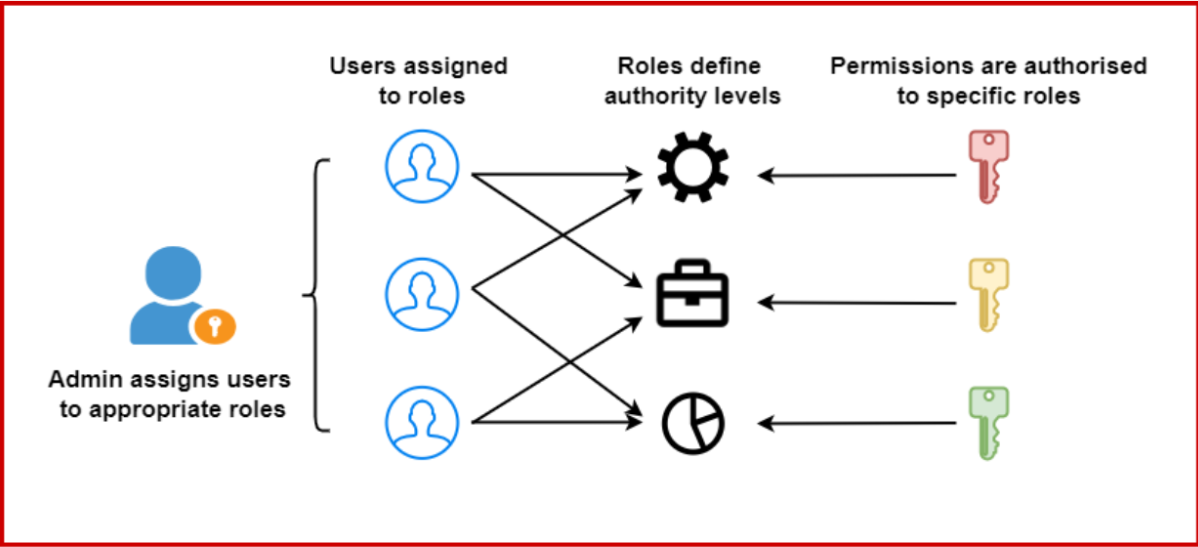
What Is Role-Based Access Control (RBAC)?
RBAC is a system where an organization may control access to resources through Roles allocated to users, groups, and applications. This way, people are granted only those permissions sufficient for their work, so this concept is called least privilege.
- Purpose of RBAC: RBAC also curtails what some users can do by limiting the capability of users. For instance, a clerk in an organization’s accounting section could require access to financial databases but not to engineering databases.
- Importance in Azure: In the cloud, where resources can be provisioned dynamically, RBAC provides the flexibility to control access effectively while maintaining security.
Core Concepts of RBAC
To understand RBAC in Azure, it’s important to familiarize yourself with its core components:
- Roles:
- Roles define the actions that a user or group is allowed to perform. Azure provides built-in roles like Owner, Contributor, Reader, and User Access Administrator.
- Owner: Full control over all resources, including assigning roles.
- Contributor: Can manage resources but cannot assign roles.
- Reader: Can view resources but cannot make changes.
- User Access Administrator: Manages user access to resources.
- Role Assignments:
- Role assignments connect a user, group, or application with a role at a specific scope. For example, you can assign a Contributor role to a user for a specific resource group.
- Role assignments connect a user, group, or application with a role at a specific scope. For example, you can assign a Contributor role to a user for a specific resource group.
- Scope:
- Scope defines where a role assignment applies. It can be set at multiple levels:
- Management Group: Applies to all subscriptions within the group.
- Subscription: Applies to all resources within a subscription.
- Resource Group: Applies to all resources within a specific group.
- Resource: Applies to an individual resource.
- Scope defines where a role assignment applies. It can be set at multiple levels:
Built-in Roles
Azure provides several predefined roles that cater to common needs. Here are some examples:
Role | Description |
Owner | Full access, including assigning roles |
Contributor | Manage resources but cannot assign roles |
Reader | Read-only access |
User Access Admin | Manage user access to resources |
Custom Roles
While built-in roles cover many scenarios, some organizations may require more specific permissions. Azure allows the creation of custom roles to meet these unique needs.
- Creating a Custom Role:
- Identify the specific actions required.
- Define the role using Azure’s JSON-based role definition.
- Assign the role to users or groups at the appropriate scope.
Assigning Roles
The process of assigning roles is straightforward but must be done carefully to avoid over-permissioning. Let’s explore this process in detail:
- Choose the Appropriate Role:
- Identify the specific tasks that need to be performed and select a role that provides only the necessary permissions. For example, if a user needs to manage resources without assigning roles, the Contributor role would be appropriate.
- Avoid assigning overly broad roles like Owner unless absolutely necessary to minimize security risks.
- Select the Scope:
- Define the level at which the role will apply. Scopes can range from broad (e.g., an entire subscription) to specific (e.g., a single resource).
- Examples:
- Assigning a role at the subscription level grants permissions for all resources within that subscription.
- Assigning at the resource group level restricts access to resources within that specific group.
- Assign the Role:
- Use one of the following methods to assign the role:
- Azure Portal: Navigate to the resource or scope, select “Access Control (IAM),” and add a role assignment.
- Azure CLI: Use commands like az role assignment create to assign roles programmatically.
- PowerShell: Utilize cmdlets like New-AzRoleAssignment for automation.
- Clearly document the role assignments to maintain transparency and support future audits.
- Use one of the following methods to assign the role:
- Review and Adjust:
- Periodically review role assignments to ensure they remain aligned with the user’s responsibilities.
- Revoke unnecessary roles promptly to reduce the risk of over-permissioning.
By following these steps, organizations can ensure that roles are assigned appropriately, providing the right balance between accessibility and security.
Monitoring and Auditing
RBAC doesn’t just provide access control; it also enables monitoring and auditing to ensure compliance:
- Monitoring Access Patterns: Use Azure Monitor to track how roles are used and identify unusual access attempts.
- Auditing Role Assignments: Regularly review role assignments to confirm that they align with organizational policies.
Common Use Cases for RBAC
RBAC is versatile and supports various scenarios, including:
- Development Environments: Limiting developers to specific resource groups.
- Production Access: Granting read-only access to production environments for certain teams.
- Third-Party Vendors: Assigning minimal permissions to external consultants.
How RBAC Integrates with Other Azure Security Features
RBAC seamlessly integrates with other Azure security features to create a robust access control framework. It works closely with Azure Active Directory (Azure AD) to manage identities, ensuring users and groups are appropriately assigned roles. By leveraging Privileged Identity Management (PIM), RBAC enables just-in-time access to critical resources, granting roles temporarily to reduce risks. Integration with Azure Monitor enhances security by logging role assignments and tracking access patterns, allowing administrators to detect and respond to unusual activity. Furthermore, RBAC’s compatibility with Deny assignments provides an additional layer of control by explicitly preventing specific actions for certain users or groups. These integrations ensure that RBAC not only controls access but also enhances the overall security and compliance posture of Azure environments.
Enhancing Security with RBAC
RBAC enhances security in cloud environments by:
- Enforcing least privilege to reduce the risk of unauthorized actions.
- Supporting granular control to ensure users have the right level of access.
- Providing detailed audit logs to maintain accountability and compliance.
Importance For D303 OA
Azure Role-Based Access Control (RBAC) is an essential tool for managing access to resources in a secure and efficient way. By understanding roles, scopes, and best practices for implementation, students preparing for WGU D303 OA exams can gain valuable insights into how RBAC enhances security in Azure environments. Implementing RBAC effectively ensures that organizations can protect their cloud resources while maintaining operational flexibility.
Tired of reading blog articles?
Let’s Watch Our Free WGU D303 Practice Questions Video Below!
Wrapping Up: Mastering Azure Security for WGU D303 Success📄
Congratulations on exploring the fascinating concepts of Identity Protection, Conditional Access Policies, and Role-Based Access Control (RBAC)! These tools are the backbone of Azure’s security, empowering organizations to safeguard their cloud environments with precision and flexibility.
As you prepare for your final WGU D303 OA, take the time to review these topics thoroughly. Understand how Identity Protection secures user identities and ensures safe access, and how RBAC assigns just the right permissions to keep systems both secure and efficient. These concepts aren’t just vital for exams; they’re essential skills for managing real-world cloud environments.
Remember, the key is to grasp the underlying principles and their practical applications. With this knowledge, you’re well on your way to mastering Azure security and excelling in your WGU D303 journey.
Good luck with your final OA—you’ve got this!